Twitter hit by multiple variants of XSS worm
17 years old author of the worm Mikey Mooney claimed responsibility for the worm (photo of him is available, podcast interview as well) citing boredom, and insisting that the most recent variant launched on Monday aimed to prove that Twitter did not fix the cross site scripting flaw which they claim was already taken care of earlier during the day.
Let's analyze all of Mikey's campaigns.
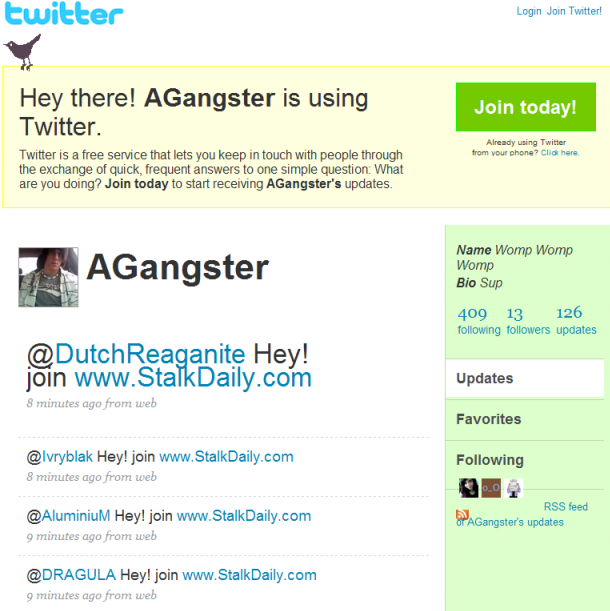
The original StalkDaily.com/Mikeyy XSS worm campaign was using automatically Tweeting the following messages:
"Dude, www.StalkDaily.com is awesome. What's the fuss?" "Join www.StalkDaily.com everyone!" "Woooo, www.StalkDaily.com :)" "Virus!? What? www.StalkDaily.com is legit!" "Wow...www.StalkDaily.com" "@twitter www.StalkDaily.com"
The second Mikeyy XSS worm launched on Sunday is a bit more interesting as it appears that this is a copycat worm which used to take advantage of the following messages:
"Wow...Mikeyy." "Man, Twitter can't fix shit. Mikeyy owns. :)" "Dude! Mikeyy! Seriously? Haha. ;)" "Dude, Mikeyy is the shit! :)" "damn mikeyy. haha." "Twitter should really fix this..." "Mikeyy I am done..." "Mikeyy is done.." "Twitter please fix this, regards Mikeyy"
The most recent variant of the worm was launched yesterday, and was apparently relying on the exploitation of an input validation flaw in what Mikeyy claims to be a second vulnerability that he exploited at Twitter.
- Go through related incidents: Commercial Twitter spamming tool hits the market; XSS worm at Justin.tv infects 2,525 profiles; Four XSS flaws hit Facebook; Facebook vulnerable to critical XSS, could lead to malware attacks; HSBC sites vulnerable to XSS flaws, could aid phishing attacks; Google fixes critical XSS vulnerability
The campaign was using the following messages to propagate:
"Twitter, freaking fix this already. >:[ - Mikeyy" "Twitter, your community is going to be mad at you... - Mikeyy" "This worm is getting out of hand Twitter. - Mikeyy" "RT!! 4th gen #Mikeyy worm on the loose! Click here to protect yourself: http://tinyurl.com/cojc6s" "This is all Twitters fault! Don't blame Mikeyy!!" "ALERT!! 4TH GEN MIKEYY WORM, USE NOSCRIPT: http://bit.ly/4ywBID" "How TO remove new Mikeyy worm! RT!! http://bit.ly/yCL1s"
Deobfuscated the scripts directs to twitter .com/reberbrerber and to stalkdaily .com/ajax.js. Interestingly, based on the public stats from bit.ly, we can easily evaluate the click-through rate of the latest campaign, with 20,140 clicks so far, with 9,268 from the U.S followed by 3,039 from the U.K for the first URL, and 8,961 clicks, with 4,095 from the U.S, followed by 1,452 from the U.K. for the second one.
With or without the malicious intend of spreading malware, Mikey's persistent actions aiming to prove Twitter's inability to fix the cross site scripting flaws are illegal, and so is the potential compromise of iReel.com for hosting purposes of the javascript code. And whereas these campaigns did not introduce malware or tried to monetize the traffic by for instance installing scareware, different people have different motivations, so instead of waiting for the hardcore cybercriminals to take advantage of such flaws, Twitter should really start treating (trivial) cross site scripting flaws more proactively.