US-CERT warning: Windows does not disable AutoRun properly

The U.S. Computer Emergency Readiness Team (US-CERT) has issued a technical cyber-security alert to warn that Microsoft's guidelines for disabling AutoRun in the Windows operating system "are not fully effective" and argues that this "could be considered a vulnerability."
The U.S. CERT warning comes on the heels of live malware/worm attacks that take advantage of the Windows AutoRun and AutoPlay features to improve propagation.
[ SEE: Is there no end to the AutoRun madness? ]
Here's the skinny on Microsoft's hiccup:
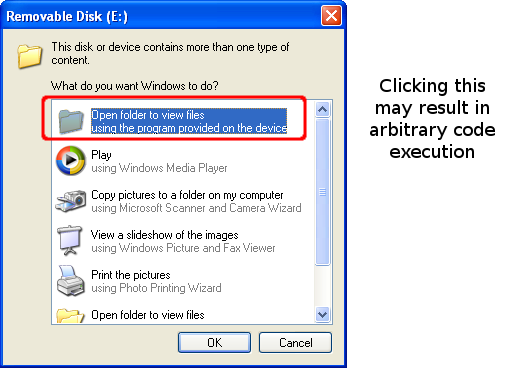
- The Autorun and NoDriveTypeAutorun registry values are both ineffective for fully disabling AutoRun capabilities on Microsoft Windows systems. Setting the Autorun registry value to 0 will not prevent newly connected devices from automatically running code specified in the Autorun.inf file. It will, however, disable Media Change Notification (MCN) messages, which may prevent Windows from detecting when a CD or DVD is changed. According to Microsoft, setting the NoDriveTypeAutorun registry value to 0xFF "disables Autoplay on all types of drives." Even with this value set, Windows may execute arbitrary code when the user clicks the icon for the device in Windows Explorer.
This means that malware authors can place an Autorun.inf file on a device to automatically execute arbitrary code when the device is connected to a Windows system. Code execution may also take place when the user attempts to browse to the software location with Windows Explorer, US-CERT warned.
The alert includes instructions for editing the registry to properly disable AutoRun in Microsoft Windows.
UPDATE: Microsoft sent me an e-mail to point out that its KB953252 document, published in May 2008, describes how to correct the problem of NoDriveTypeAutoRun registry value enforcement. This prompted an update on the US-CERT notice:
After the update is installed, Windows will obey the NoDriveTypeAutorun registry value. Note that this fix has been released via Microsoft Update to Windows Vista and Server 2008 systems as part of the MS08-038 Security Bulletin. Windows 2000, XP, and Server 2003 users must install the update manually. Our testing has shown that installing this update and setting the NoDriveTypeAutoRun registry value to 0xFF will disable AutoRun.