Verizon's data breach report: Point-of-sale, Web app attacks take center stage

Payment systems were under fire, 94 percent of security incidents fall into nine basic attack patterns, Web application attacks dominate the financial services sector and point of sale and distributed denial of service attacks plague retail.
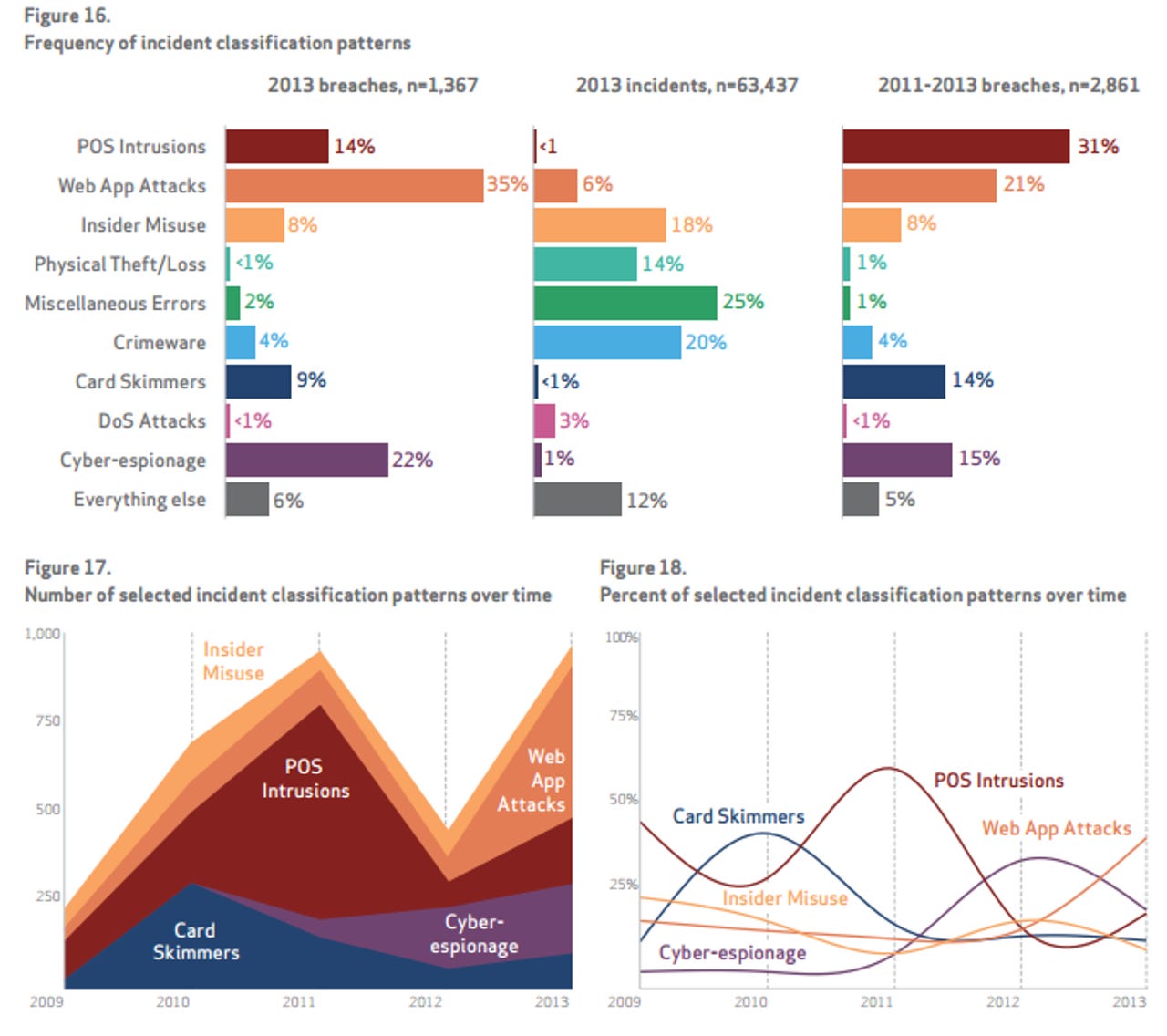
Those were the primary takeaways from Verizon's 2014 Data Breach Investigations Report (DBIR), which had 50 global companies contributing, 1,367 confirmed data breaches and 63,437 security incidents.
Verizon's DBIR report has a bevy of goodies, but the money graphics are these two:
Read this
What that latter graphic highlights is the risk weighting by industry. For instance, hotels and restaurants really need to lock down their point-of-sale systems, but don't have to sweat Web app attacks. Retail needs to focus on point-of-sale terminals and denial of service attacks, but cyber espionage isn't likely to be an issue. Utilities, manufacturing, and mining need to worry about cyber espionage from other countries.
"It's a complex landscape and you can't take a top 10 list and say that everyone defend against the same things," said Jay Jacobs, senior analysts at Verizon Enterprise Solutions and DBIR co-author. "There's a risk grid by industry."
But since 2013 was the year of retail attacks — or at least publicized ones thanks to Target — here's a snippet from the report:
From an attack pattern standpoint, the most simplistic narrative is as follows: Compromise the POS device, install malware to collect magnetic stripe data in process, retrieve data, and cash in. All of these attacks share financial gain as a motive, and most can be conclusively attributed (and the rest most likely as well) to organized criminal groups operating out of Eastern Europe.
Such groups are very efficient at what they do; they eat POSs like yours for breakfast, then wash ‘em down with a shot of vodka. While the majority of these cases look very much alike, the steps taken to compromise the point-of-sale environment offer some interesting variations.
The most popular point-of-sale attack involves RAM-scraping malware, which grabs payment card data while it's being processed in memory before it's encrypted.
Regarding Web attacks, Verizon's Enterprise unit recommended the following controls:
- Don't use single-factor password authentication on anything that faces the Internet;
- Set up automatic patches for any content management system such as Drupal and WordPress;
- Fix vulnerabilities right away before the bad guys find them;
- Enforce lockout policies;
- Monitor outbound connections.
Other items worth noting:
- Insider misuse remains a huge problem and much of security still revolves around trusting an individual — often an employee.
- Healthcare, public sector, and mining are the industries with the most lost and stolen laptops. Thefts are often exposed in these industries due to mandatory reporting requirements.
- Verizon's advice for preventing stolen gear was conventional for the most part — encrypt devices, back them up and lock them down — but did say it may make sense to buy "unappealing tech." Verizon said:
Yes, it’s unorthodox as far as recommendations go, but it might actually be an effective theft deterrent (though it will probably increase loss frequency). That shiny new MacBook Air on the passenger seat may be too tempting for anyone to resist, but only those truly dedicated crooks will risk incarceration for a 4” thick mid-90s lap brick. Or, if being the fastest hunk of junk in the galaxy is a must, perhaps there’s a lucrative aftermarket for clunky laptop covers. She may not look like much, but she’s got it where it counts, kid.
- The US remains the largest victim of cyber espionage, with South Korea a distant second. State affiliated actors are 87 percent of cyber espionage cases and 49 percent of them hail from Eastern Asia.