Why malware networks are beating antivirus software

The most consistent thing about the malware business is that it’s constantly changing. The field is dominated by gangs that use hit-and-run tactics. A new report by Blue Coat Systems, a security company that specializes in cloud-based services, provides some interesting (and rare) details about how the malware business ebbs and flows.
Between February and May 2011, for example, Blue Coat had 395 unique malware networks under observation. On any given day, their data show, "the number of unique malware networks … ranged from just under 100 ... to fewer than 25 in operation.” The report specifically noted “a drop-off in mid-May as networks relocated and consolidated.”
Back in May, I observed the Mac Defender gang carefully. Lately, I’ve been watching a new round of attacks from a different network. Their product is a Trojan, aimed at Windows users. It arrives via e-mail, as a file attachment called RefundForm, in Zip format. It appears to be from a hotel. The subject line indicates it’s about a “wrong transaction” and the message body says the hotel overcharged the recipient’s credit card and says they need to fill out a claim form (attached) to get the money back
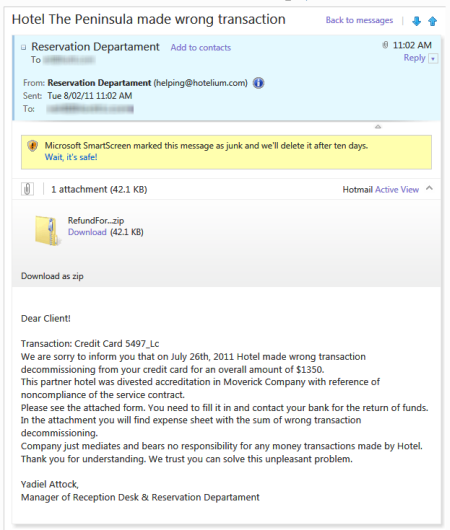
Now, this is terrible social engineering. The message is poorly written, and probably won’t fool a native English speaker. But it might be good enough to fool an unsophisticated Windows user whose English is less than perfect. Because the attached file is inside a Zip file, it can get past mail gateways that block executable files as attachments. The compressed attachment contains a Windows executable file, of course, not an Excel form, as the file icon tries to fool the recipient into thinking:
I first noticed this attack last week, on July 27, when several of these messages showed up in the Junk folder of an account I use for monitoring spam. (It’s from a domain I own but is redirected to a Hotmail server.) I saw multiple copies over the course of several days, including (in a remarkable coincidence) one that included the name of a resort I had actually visited earlier this year.
The copy shown in the screen above arrived Tuesday morning at 11:02AM. I copied the file attachment to my local hard drive and did some basic analysis.
First step: I uploaded a copy of the suspicious file to VirusTotal, which reported that I wasn't the first to report this variant; 6 of 30 antivirus engines had detected it as malware when it was first submitted two hours earlier. When I asked for a reanalysis, it showed that the detection rate had gone up to 13 of 43 engines, presumably based on signatures that had been updated during that brief interval. (After 24 hours, 25 out of 43 engines said it was malware, although they couldn't agree at all on what it is.)
Second step: I went to ThreatExpert and uploaded a copy of the suspicious file. It wasn’t able to identify the sample as a known threat, but a detailed report that arrived via e-mail a few minutes later contained suspicious details:
- File system modifications: Running the file created a new executable, Dxdiag.exe, in the Startup folder. This is the same name as a Windows system tool and is a major red flag.
- Memory modifications: Svchost.exe, a Windows system file that hosts system services, was modified, with new memory pages created in its address space. This is not something a legitimate program does.
- Network access: The program attempted to make a connection to a remote host over port 80 and tried to run a pair of scripts from a server in Russia. It is most likely that these were attempts to download and install additional software, this time in the background.
These are all telltale signs of particularly aggressive malware. Indeed, Microsoft's security team identified it as TrojanDownloader:Win32/Dofoil.G. Trust me, you do not want this thing running on any PC you own.
As a test, I kept the file attachment in a local folder and began checking it every few hours using the on-demand scanning tools in two current, high-end consumer antivirus programs running on Windows 7 desktop systems in my office. Before each check, I downloaded and installed the latest updates for each program. What happened?
See also:
- Stay safe online: 5 secrets every PC (and Mac) owner should know
- IE9 versus Chrome: which one blocks malware better?
- Malware writers using copy protection
- How prevalent is malware on Windows PCs?
- Do you really need antivirus software?
Page 2: AV scanners miss the threat -->
<-- Previous page
Trend Micro Titanium Maximum Security gave the malicious file a clean bill of health for nearly 24 hours. After I installed a definition file that was time-stamped at 9:18AM Wednesday, this file was detected and removed.
Norton Internet Security 2011 offered at least a half-dozen updates in the 24 hours after this message arrived, including one that required a restart. Still, a full day after I downloaded this file, it still wasn’t recognized as dangerous. Norton gave it this green-is-good checkmark.
And here’s the even worse news. Wednesday morning at 3:39AM, another copy of this particular Trojan arrived. It’s at least the eighth distinct variant I’ve seen personally. (Researchers at the University of Alabama Birmingham have confirmed that there are many variants of this threat.) ThreatExpert confirms that it is functionally identical to the previous versions I saw.
Roughly 10 hours after it appeared here, it was recognized as malware by only 7 of 41 engines on VirusTotal. The Trend Micro online service, House Call, flags it as hostile, but my local Trend Micro software waved it through, as did Norton Internet Security.
On my system, at least, the good news is that Tuesday's threat was blocked by a separate security layer. Hotmail’s filters moved the message to the Junk folder, where a recipient is likely to be much more suspicious and where downloads of file attachments are not allowed without extra steps. All formatting is stripped away, making logos and other social engineering tricks ineffective. Within four hours after that variant arrived, Hotmail had blocked the file attachment from even being downloaded, much less opened. Although the message was still in my Inbox, trying to download it resulted in this message:
The fact that I am using a cloud-based service rather than downloading all my mail locally turns out to be a useful security measure, in that these hostile attachments are much less likely to end up on my PC.
On a separate system, accessing the same account using Microsoft Outlook, every copy of the suspicious file was blocked from opening upon arrival.
The point of all this is to establish a simple fact: In the war between malware distributors and conventional signature-based security software, the bad guys have the upper hand. They can morph their software very quickly and basically give themselves a free head start of hours or even days against even aggressively updated security programs.
Don’t get me wrong: scanning is useful. It can block some threats, and it’s effective at cleaning up some malicious downloads. But it’s not a panacea and it shouldn’t be considered the primary layer of protection.
Despite Norton’s slow response in this example, it’s my current favorite overall, precisely because it does more than just scan. In particular, its reputation-based analyses are exemplary. In a follow-up post, I’ll have more on what Symantec is doing and why other AV vendors should follow their lead.
See also: