Windows Defender removes potentially dangerous Dell certificate

Earlier this week, security experts discovered a pair of root certificates, installed by default on some Dell computers, that could allow an attacker to compromise the machines with ease.
The incident is reminiscent of a similar security blunder earlier in the year from Lenovo, which exposed its customers to a similar vulnerability by preinstalling the Superfish adware.
Dell's vulnerable certificates aren't part of a money-making scheme, as Lenovo's were, but instead were part of support tools.
And beginning today, they're being identified and automatically removed from PCs by the built-in Windows Defender security software included with all modern Windows versions.
I saw the cleanup routine in action this morning on a machine with the Dell System Detect software installed. A notification message led to this screen in Windows Defender:
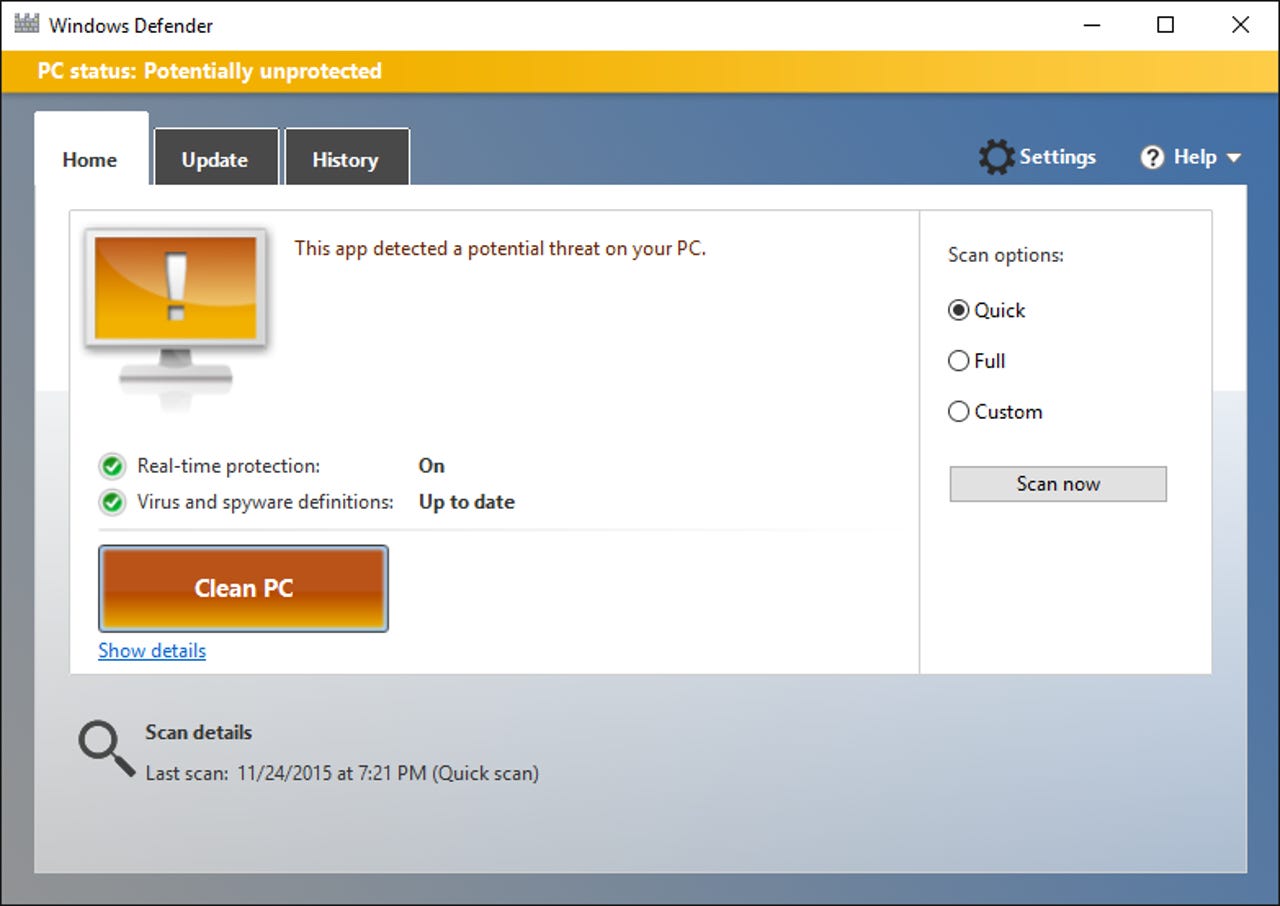
Clicking the Show Details button led to this screen, which identified the potential threat as Win32/CompromisedCert.D. (The link at the bottom of the screen leads to a writeup at Microsoft's Malware Protection Center.)
I checked Certificate Manager before running the cleanup operation and confirmed that the vuilnerable DSDTestProvider certificate was installed. After the cleanup operation completed, it was gone.
The quick response should be a feather in the cap for Microsoft's Security Response group, Ironically, it won't be available for Dell owners whose PCs shipped with third-party antivirus software that's still installed and up to date.
Update: In the comments, several people have asked whether the root certificate will be reinstalled along with Dell System Detect. The answer is no, according tothis support article from Dell. I have confirmed via my own testing that the current release does not install this or any other certificate.