Windows zero-days don't usually work against the latest OS version

Attacks using zero-days are rarely effective against the most recent versions of Windows, according to Matt Miller, a security engineer with the Microsoft Security Response Center.
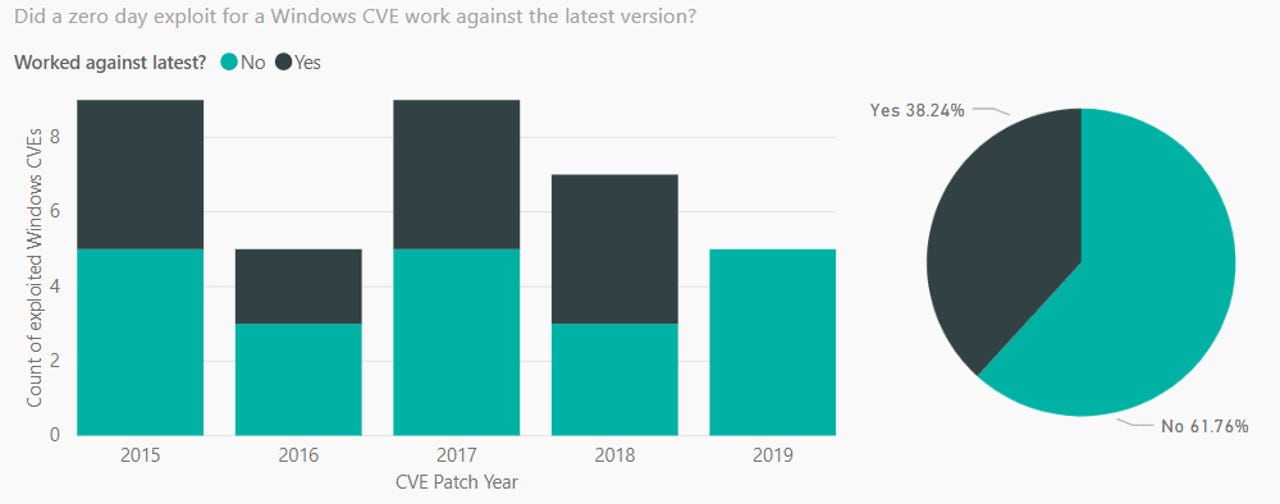
In new statistics released today, Miller said that only around 40% of all Windows zero-days were successfully exploited against the latest Windows versions since 2015.
This means that the vast majority of Windows zero-days used in live attacks only work against older versions of the OS, and users who kept their operating systems up to date where safeguarded from some of these attacks.
Per Miller, in two out of three cases, the zero-days didn't work against recent versions of Windows due to the mitigations Microsoft had added to the OS
The researcher analyzed zero-day exploitation attempts between 2015 and 2019 -- namely since Microsoft launched Windows 10, one of the most secure operating systems around.
When it launched, Windows 10 featured security systems like Control Flow Guard and Device Guard, among others.
The statistics Miller shared today are part of the researcher's upcoming "Trends and Challenges in the Vulnerability Mitigation Landscape" presentation that he'll be giving at the Usenix WOOT '19 security conference in August.
The talk is a continuation of Miller's research into vulnerability trends.
As a member of the Microsoft Security Response Center, Miller has been studying these trends for years, giving numerous talks in the past.
One of his more recent talks was at the BlueHat Israel security conference in February. Back then, Miller shared stats showing that when Windows vulnerabilities are exploited, they are most likely exploited as a zero-day, before Microsoft had a chance to release a patch, or months later, after companies have failed to patch.
Taking today's statistics into account, this also means that attackers would have a better chance at searching for zero-days in older Windows versions, rather than looking for zero-days targeting the most recent release.
In addition, Miller also revealed that around 70% of all security bugs addressed by Microsoft in the past 12 years were memory management-related issues.
Miller's MSRC colleagues have recently announced plans to explore using Rust as an alternative to C and C++, the two main languages used for coding Windows. MSRC said it was looking into Rust because of the language's security-focused features that reduce the number of memory-related bugs.
HackerOne's top 20 public bug bounty programs
More vulnerability reports:
- Vulnerabilities found in GE anesthesia machines
- Tor Project to fix bug used for DDoS attacks on Onion sites for years
- Hackers target 62 US colleges by exploiting ERP vulnerability
- Backdoor found in Ruby library for checking for strong passwords
- Gigabyte and Lenovo servers impacted by common BMC firmware flaws
- Remote code execution vulnerability in VLC remains unpatched
- KRACK attack: Here's how companies are responding CNET
- Top 10 app vulnerabilities: Unpatched plugins and extensions dominate TechRepublic