Norton Internet Security 2009: Photos

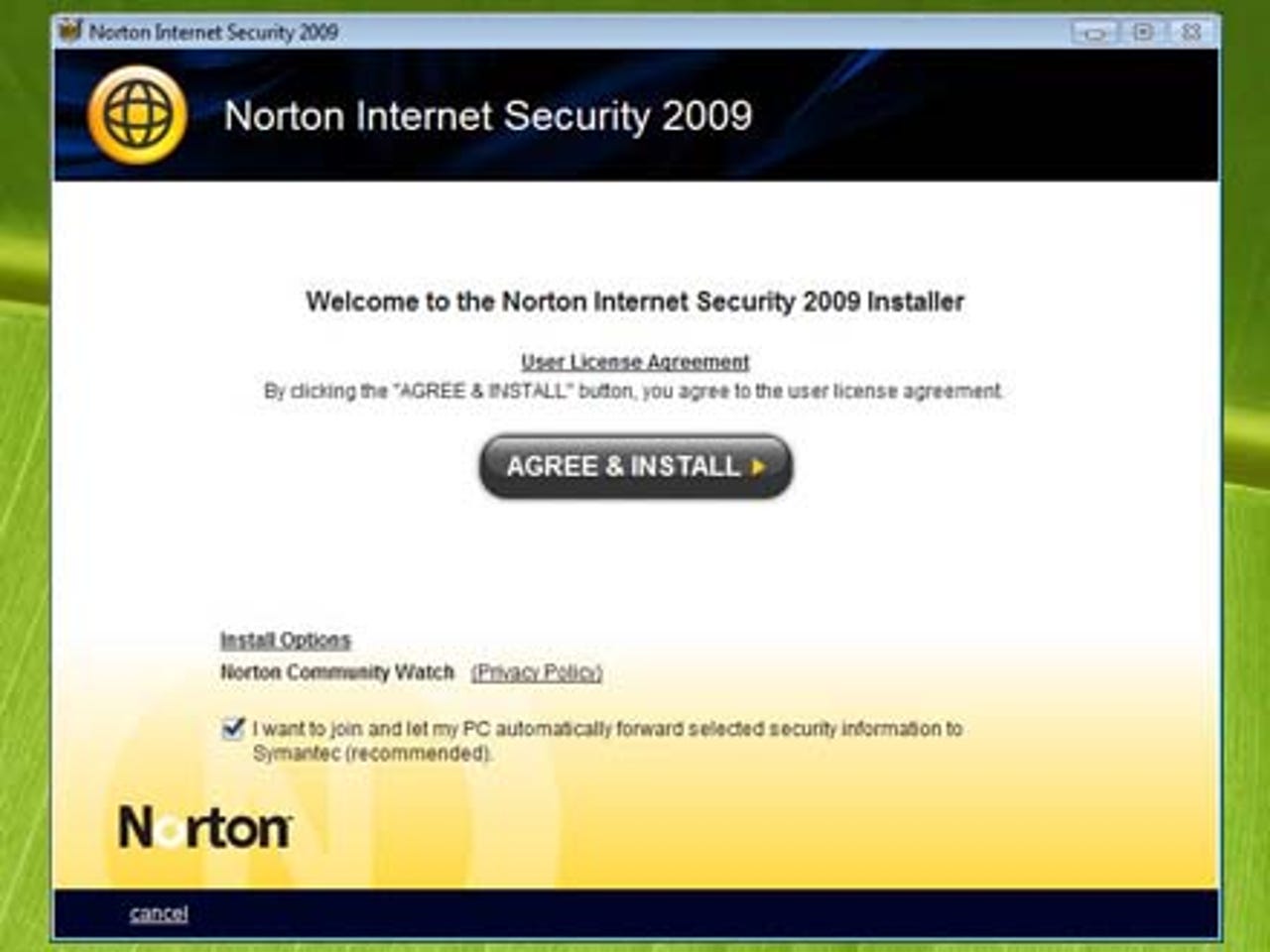
The initial installation screen for Norton Internet Security 2009.
The installation was quite quick, in contrast with previous editions of Norton.
Unlike a lot of software we've tried, the status bar was even quite accurate.
Symantec provided us with a product key to trial Norton 2009.
Norton 2009 forces you to create a Norton account to be able to use the software.
This screen provides details of your licensing agreement.
Norton 2009's home screen.
Conducting a scan.
Oops! We've found some cookies. They're probably harmless. We tested Norton Internet Security 2009 on a clean install of Windows Vista, so we didn't expect to find much.
Norton's web site, where you can log in to your Norton account and make some configuration changes.
The network security map page drills down to network details.
Norton's Identity Safe feature allows users to securely store web login credentials, as well as other information such as credit cards and addresses.
The CPU usage screen shows how much system resources Norton is taking up.
Norton Insight identifies trusted files that do not require scanning, allowing the security process to take less time.
Norton 2009 installs itself into Windows Vista's sidebar.
The software provides a history of actions taken.
There are more settings than you can poke a stick at.