Adware-serving Skype botnet disrupted

An adware-serving botnet harnessing the Skype communications platform has been discovered and disrupted by PhishMe and Microsoft security researchers.
As technology evolves and the cybersecurity landscape changes, so does the nature of threats -- including botnets and phishing campaigns. In the past, botnets would comprise of malware connecting to random posts running on internet relay chat (IRC), forging a connection to a botnet and then awaiting commands from the command and control (C&C) center.
However, things have changed -- and now botnets can run on cloud-based systems including Skype without needing to own or compromise the system itself.
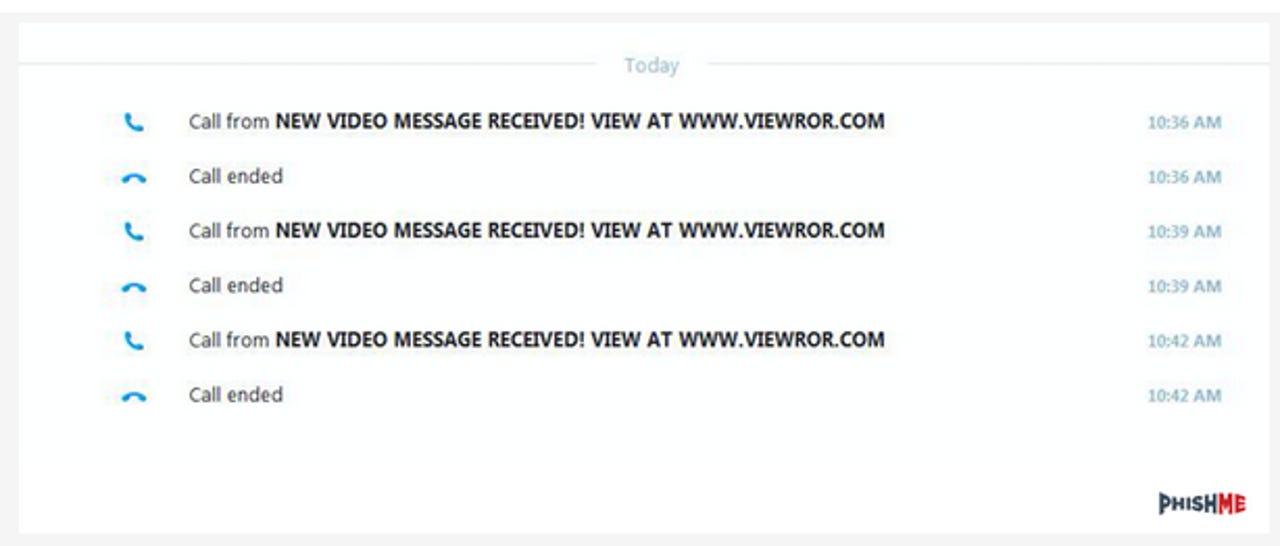
Ronnie Tokazowski from phishing detection and training firm PhishMe revealed the existence of the botnet this week. In a blog post, the security researcher said the Skype botnet was discovered when a PhishMe users received a video message and call attempts.
The messages include a link to the claimed video message. If clicked, the victim is directed to a download link in order to install a "proprietary" video player necessary to play the video.
The security team found during an analysis of the web page's HTML that the download is part of an affiliate program, and the cyberattacker is likely being paid on a per-install or per-download basis. Therefore, spamming the Skype network via an automated botnet could result in rich rewards for the threat actor.
Once the file is downloaded and the executable is opened, the file asks to run as an administrator -- which if accepted, then begins to install a variety of adware programs on the system.
Featured
The so-called "proprietary" media player, however, does download and install -- even though the program, called Media Player Classic, is available for free online legitimately.
In order to disrupt the botnet serving this adware, the team traced the botnet's infrastructure back to hosting in the Amazon AWS cloud. After informing Amazon's security team of the botnet's presence and domains hosting the botnet infrastructure, PhishMe then contacted Microsoft in order to go after the accounts and usernames used to send the botnet's spam messages.
This week, some Skype users suffered disruption and software crashes. Skype acknowledged the bug was caused by a user being sent a simple "http://:" string -- not harmful, but certainly frustrating. The company is working to fix the problem, which appears to affect Windows, Android, and iOS clients.
Read on: In the world of security