An insecure mess: How flawed JavaScript is turning web into a hacker's playground

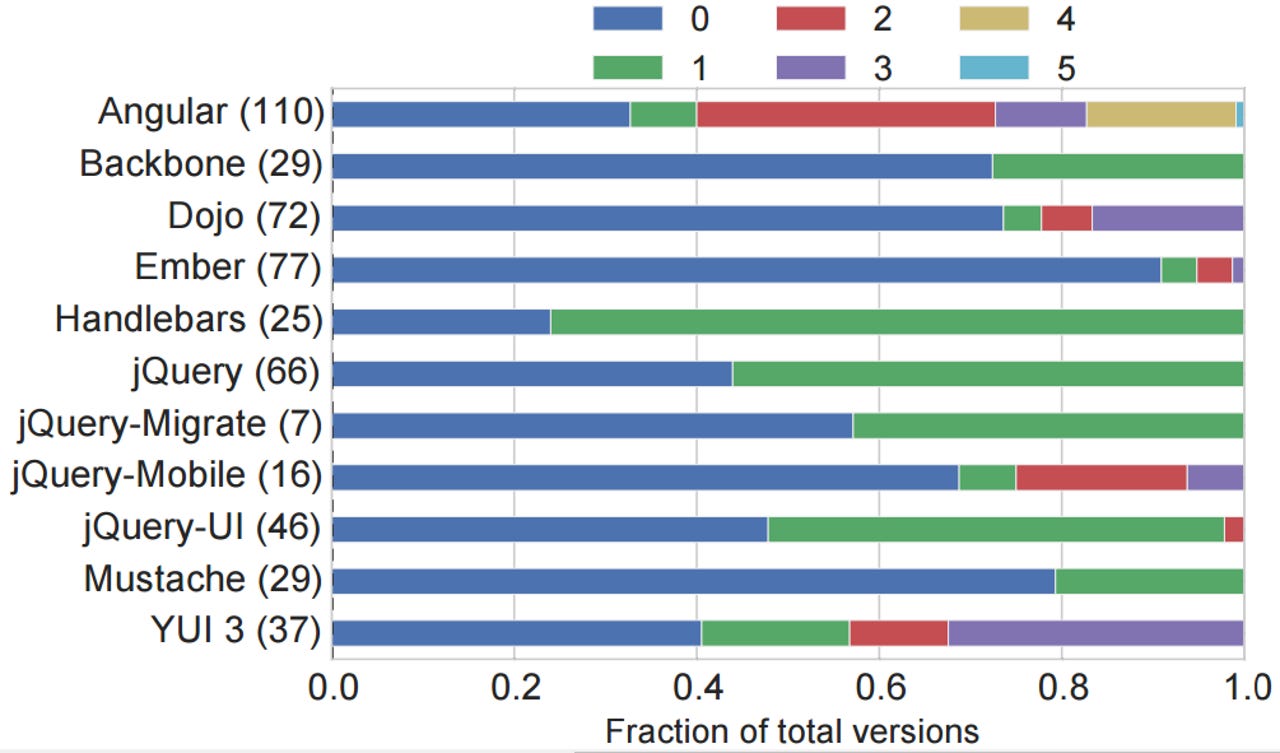
This chart shows the fraction of JavaScript library versions with distinct known vulnerabilities, each represented by colors, out of the total library versions in brackets.
An analysis of over 133,000 websites has found that 37 percent of them have at least one JavaScript library with a known vulnerability.
Researchers from Northeastern University have followed up on research in 2014 that drew attention to potential security risks caused by loading outdated versions of JavaScript libraries, such as such as jQuery, and the AngularJS framework in the browser.
As the Northeastern researchers highlight in a new paper, vulnerable libraries can be dangerous under the right conditions, pointing to an old cross-site scripting bug in jQuery, which will allow an attacker to inject malicious scripts into a vulnerable site.
They looked at domains from Amazon's Alexa Top 75,000 list and 75,000 randomly selected .com domains, assessing 72 different libraries and their respective versions. Overall, 87 percent of the Alexa sites and 46.5 percent of the .com sites use one of the 72 libraries.
The study found that "36.7 percent of jQuery, 40.1 percent of Angular, 86.6 percent of Handlebars, and 87.3 percent of YUI inclusions use a vulnerable version." Additionally, 9.7 percent of the sites in the study use two or more vulnerable library versions.
However, the most popular sites in the study were found to be far less likely to include a vulnerable library. The researchers found that only 21 percent of the top 100 Alexa sites did so.
Still, the researcher's overall take on the state of security for the JavaScript ecosystem is that it's a complete mess.
"Perhaps our most sobering finding is practical evidence that the JavaScript library ecosystem is complex, unorganised, and quite 'ad hoc' with respect to security," the researchers write.
"There are no reliable vulnerability databases, no security mailing lists maintained by library vendors, few or no details on security issues in release notes, and often, it is difficult to determine which versions of a library are affected by a specific reported vulnerability."
Remediation won't be a simple task either because the vast majority of sites use libraries that are so far out of date. For example, the median lag between the oldest version on each website and the newest version is over three years.
"We observe that only very small fraction of potentially vulnerable sites -- 2.8 percent in Alexa, 1.6 percent in .com -- could become free of vulnerabilities by applying patch-level updates, ie, an update of the least significant version component, such as from 1.2.3 to 1.2.4, which would generally be expected to be backwards compatible," the researchers note.
"The vast majority of sites would need to install at least one library with a more recent major or minor version, which might necessitate additional code changes due to incompatibilities."
More on security
- This USB firewall protects against malicious device attacks
- Google Cloud unveils its custom security chip, new security features
- After CIA leaks, tech giants scramble to patch security flaws
- WikiLeaks: We will work with tech companies to fix CIA hacking holes
- Could new cloud service ease compliance headaches?
- FBI, CIA launch investigation into WikiLeaks file dump
- Google says Chrome, Android already shielded from 'many' CIA exploits