Browser-based cryptojacking sees sudden spike in activity in Q2 2020

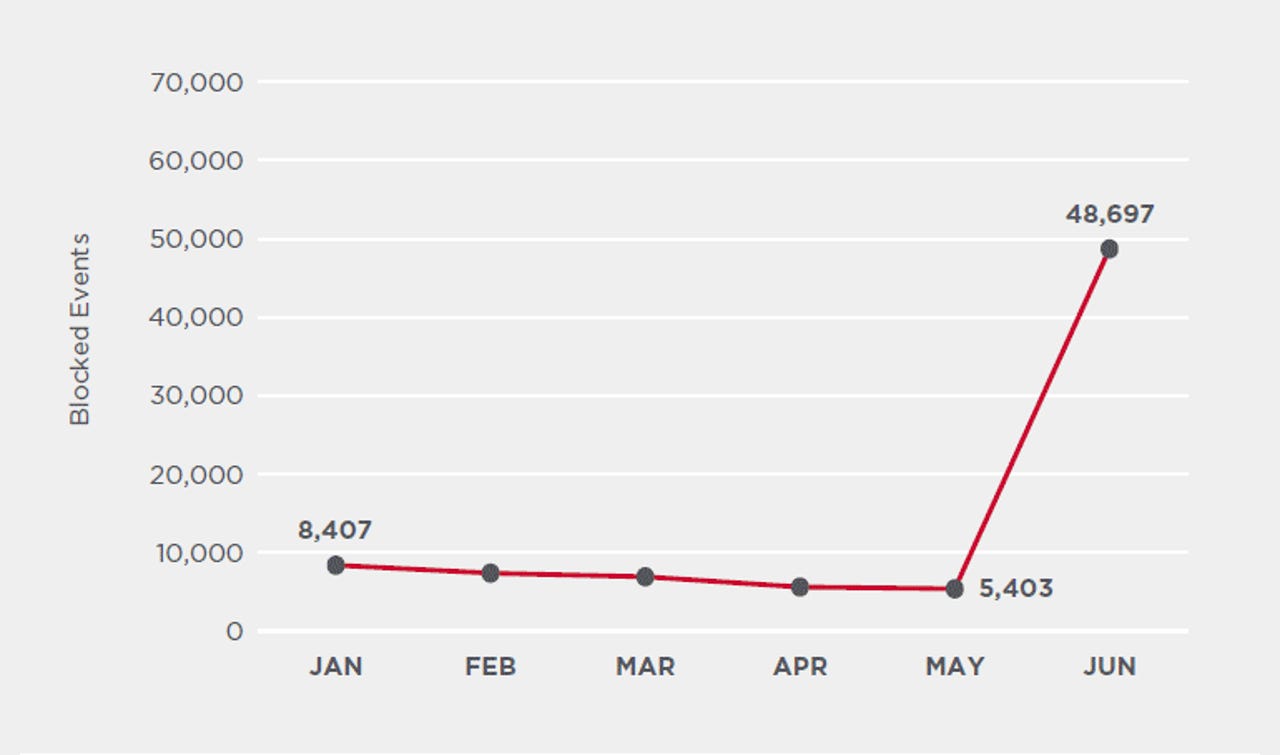
Browser-based cryptocurrency mining, also known as cryptojacking, made a surprising comeback earlier this year, in the month of June.
In its Threat Landscape Trends report for Q2 2020, US cyber-security vendor Symantec said cryptojacking saw a 163% increase in detections, compared to the previous quarters.
The spike in activity is extremely uncharacteristic for this particular threat, considered by all security experts to be long dead.
A short history of browser-based cryptojacking
The glory days of browser-based cryptocurrency mining (cryptojacking) lasted from September 2017 to March 2019, during which time, browser-based cryptojacking become one of the most prevalent forms of cyber-attacks.
The rise of this particular malware trend coincided with the launch and shutdown of Coinhive, a German-based web service that allowed users to mine the Monero cryptocurrency inside their own website just by adding a small JavaScript library (coinhive.js) to their sites' source code.
While the service launched as an alternative website monetization scheme to classic online ads, the service became very popular with cybercrime groups.
Cybercriminals would often hack into websites across the world and secretly load Coinhive's library on the sites, but configured to mine Monero for the criminal groups.
However, in March 2019, out of the blue, the Coinhive operators announced they were shutting down, citing various reasons, including the growing difficulty and efficiency in mining Monero inside web browsers.
Furthermore, by that time, browser makers also had enough of malicious groups slowing down websites and started deploying security features to detect and block cryptojacking operations.
In addition, academic teams also began looking into the scheme's efficiency. For example, an academic paper published in August 2019 discovered that cryptojacking was incredibly inefficient at generating revenue, despite its popularity among cybercrime groups, with just three classic online ads generating 5.5 times more revenue than a web-based cryptojacking script.
These were the reasons why after Coinhive's shutdown in the spring of 2019, detections for cryptojacking attacks have gone off a cliff and flatlined to almost non-existent levels, as most cybercrime gangs moved on to other tactics.
Router-hijacking botnet suspected
Prior to today's report, Symantec said cryptojacking detections have been at the same low detection levels for months.
While the company could not be reached for comment on the source of the June spike, a source in the antivirus industry told ZDNet today that the sudden surge in cryptojacking detections was most likely caused by a router botnet.
The source, who did not want to be identified by name for this report, said that such incidents have happened before, and usually in Latin America.
Malware groups often hack into home routers and change DNS settings to hijack legitimate web traffic, use the hacked routers as proxies, or abuse them to launch DDoS attacks.
In some rare instances, some groups will also experiment with other ways of monetizing their router botnets, such as deploying cryptojacking scripts, usually modified versions of the old coinhive.js library, updated to work without the now-defunct Coinhive service.
However, despite the sudden spike in browser-based cryptojacking detections in June, a full comeback is not expected. Most cybercrime groups who experimented with cryptojacking operations in the past usually dropped it weeks later, as they also discovered that browser-based cryptocurrency-mining was both a waste of their time and too noisy, drawing more attention to their respective operations than profits.