Connection discovered between Chinese hacker group APT15 and defense contractor

In a report published today, cyber-security firm Lookout said it found evidence connecting Android malware that was used to spy on minorities in China to a large government defense contractor from the city of Xi'an.
Lookout's 52-page report [PDF] details a years-long hacking campaign that has primarily targeted the Uyghur ethnic minority, living in western China, but also the Tibetan community, to a lesser degree.
The campaign infected individuals in these communities with malware, allowing government hackers to keep an eye on the activities of minority communities in China's border regions but also living abroad in at least 14 other countries.
"Activity of these surveillance campaigns has been observed as far back as 2013," Lookout researchers said.
The company attributed this secret surveillance to a hacking group they believe operates on behalf of the Chinese government.
Some of the group's past hacking operations have been documented by other cyber-security firms, and the hacking group is already known in industry circles under different codenames, such as APT15, GREF, Ke3chang, Mirage, Vixen Panda, and Playful Dragon.
The vast majority of past APT15 attacks involved malware designed to infect Windows desktops, but Lookout said the group also developed an arsenal of Android hacking tools.
Hacking tools that were already known include malware strains identified as HenBox, PluginPhantom, Spywaller, and DarthPusher. On top of these, Lookout said it also discovered four new ones, which they codenamed SilkBean, DoubleAgent, CarbonSteal, and GoldenEagle. (see image below for their features)
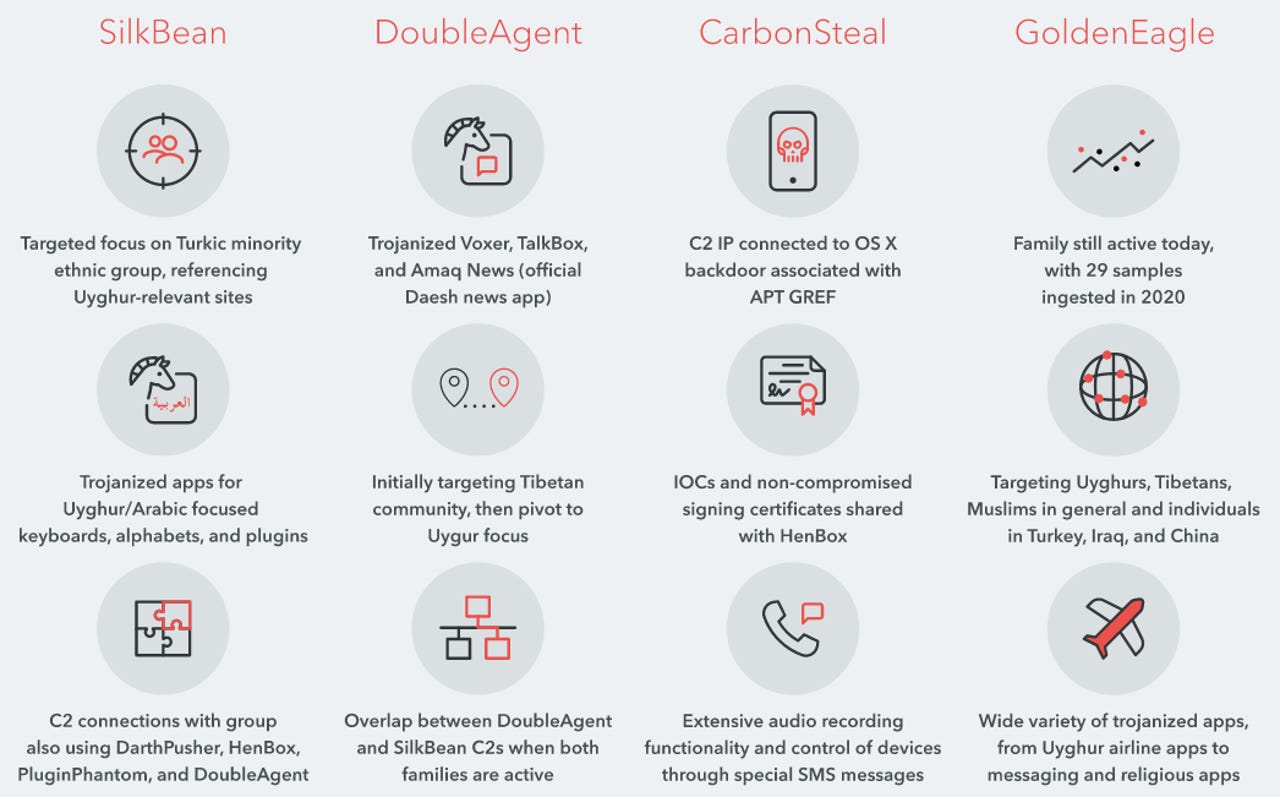
Lookout said it undeniably tied these new Android malware strains to previous APT15 Android hacking tools because of shared infrastructure and the use of the same digital certificates to sign various samples.
To distribute their malware, Lookout said APT15 didn't upload the apps on the Google Play Store but instead used a technique known as a "watering hole attack," where they hacked legitimate sites and inserted malicious code in them. The malicious code redirected users to web pages, forums, app stores, and other sites from where users were asked to download and install apps infected with APT15's malware.
Ties to a defense contractor in central China
But Lookout said that during the early stages of its research into APT15's new malware, they found a command-and-control server for the GoldenEagle spyware that was left unprotected.
Security researchers said they accessed the server and collected information on victims and the operators who were managing the malware.
Looking through logs, Lookout said it found data from the first devices infected with GoldenEagle. When Lookout plotted GPS coordinates obtained from these infected devices, they found that most were around one single area.
Lookout said the GPS coordinates plotted around a building hosting the offices of Xi'an Tianhe Defense Technology, a large defense contractor in the city of Xi'an, in central China.
Security researchers said these initial infections, coupled with their GPS coordinates, appear to be for devices infected in the malware's early development phase, and most likely test devices, suggesting that the company was most likely the one who developed the GoldenEagle malware.
Other doxed APTs
The fact that Lookout linked an APT15 malware sample to a Chinese defense contractor is not a novel discovery. From 2017 to 2019, four other Chinese state-sponsored hacking groups have been linked to contractors hired by Chinese intelligence agencies operating in various regional offices.
This includes:
- APT3 - linked to a company named Boyusec operating on behalf of Chinese state security officials in the province of Guangdong
- APT10 - linked to several companies operating on behalf of Chinese state security officials in the province of Tianjin
- APT17 - linked to several companies operating on behalf of Chinese state security officials in the province of Jinan
- APT40 - linked to several shell companies operating on behalf of Chinese state security officials in the province of Hainan
Operators behind APT3 and APT10 have eventually been charged by the US Department of Justice in November 2017 and December 2018, respectively.
Based on previous threat intelligence reports published by cyber-security firm Recorded Future and CrowdStrike, the Chinese Ministry of State Security outsources hacking operations to outside contractors, who report directly and take orders from intelligence officials.