Emerging nations see rise in malicious Net activity

Emerging markets such as the BRIC (Brazil, Russia, India and China) nations are moving up the ranks and accounting for more malicious online activity globally, according to a new security report.
Released Tuesday, the Symantec Internet Security Threat Report (ISTR) Volume XV revealed that emerging countries made up half of the global top 10 locations for malicious activity last year.
China remained at No. 2, the same ranking as 2008. Brazil broke into the top three for the first time in five years, boosted by its No. 1 ranking in spam zombies. India, which ranked No. 11 in 2008, jumped to fifth spot last year, while Russia and Poland came in at No. 7 and No. 8, respectively.
The United States remained the country that accounted for the world's highest level of malicious activity, contributing 19 percent of global threats in 2009. However, its volume saw a 23 percent dip from that in 2008. The U.S. also had the dubious honor of being home to the most phishing hosts and bots, among others.
Within the Asia-Pacific region, malicious activity by country in 2009 did not differ much from the previous year, noted Ronnie Ng, Symantec's senior manager of systems engineering for Singapore. He told ZDNet Asia in a phone interview that contrasting the region's malicious activity volume with the global numbers, Asia-Pacific levels were "still good".
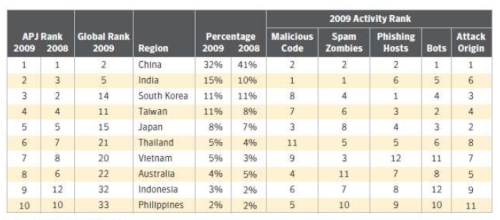
In particular, China's share of malicious activity in the region last year saw a drop compared to 2008, which could be attributed to measures that the Chinese authorities have taken, such as tightening controls over domain name registration.
Targeted enterprise attacks on rise
Another trend highlighted in the Symantec report was the increase in emphasis on targeted attacks against the enterprise.
Citing examples such as Trojan Hydraq or the exploit used in "Operation Aurora" and GhostNet, Ng said the attacks were able to gather pace due to the wealth of corporate intellectual property that could be exploited for financial gain.
"The attackers are trying to get into the [corporate] systems in any way they can--social engineering, doing fact finding on info on the organization, and staying there for an extensive amount of time to try to find information that is of value to them," he warned.
Such targeted attacks, he added, would be the most pressing issue enterprises need to guard against.
To better counter these attacks, organizations need to be wary about corporate information that are exposed through its employees, Ng said. This involves educating users on appropriate Internet access behavior, including the type of information they post on social networking sites.
Other significant findings from the ISTR:
• Globally, Symantec created nearly 2.9 million signatures for malicious code last year. The figure represents a 71 percent jump over 2008 and 51 percent of the total number of signatures the company has created to date.
• The top Web-based attack in 2009 was associated with malicious PDF activity, which accounted for 49 percent of overall activities.
• Hacking accounted for 60 percent of exposed identities in 2009, compared to just 22 percent in 2008.
• Taipei was the city with the most number of bots or zombie computers in 2009, accounting for 5 percent of the worldwide total.
• Mozilla Firefox was affected by 169 new vulnerabilities last year, more than any other browser. There were 94 new vulnerabilities identified in Apple Safari, 41 in Google Chrome and 25 in Opera. Microsoft Internet Explorer had 45 reported vulnerabilities but remained the most attacked browser.