Facebook rolls out 'Whitehat Settings' to help bug hunters analyze traffic in its mobile apps

Facebook made a significant concession to vulnerability researchers last week by adding a special setting to Facebook accounts to accommodate whitehat security research.
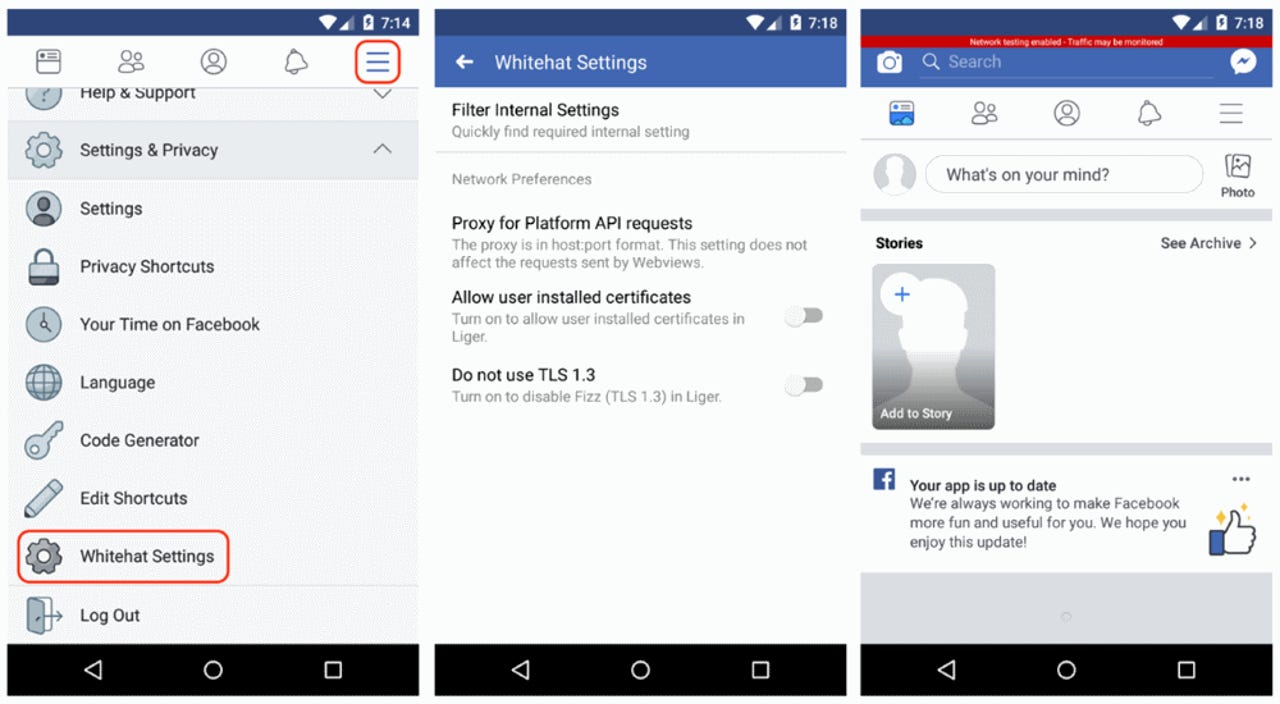
The new option, named "Whitehat Settings," introduces a mechanism through which security researchers can bypass Facebook's Certificate Pinning security mechanism.
Certificate Pinning normally protects traffic that originates from Facebook mobile apps against sniffing operations. But according to Facebook, when security researchers turn on the "Whitehat Settings" option, Facebook will intentionally break its Certificate Pinning mechanism for that account, so the researcher can intercept, sniff, and analyze the traffic that originates from within.
Facebook said it implemented the "Whitehat Settings" option at the behest of security researchers who were having a hard time bypassing the Certificate Pinning security measure.
Facebook rolled out "Whitehat settings" to help analyse traffic in its mobile apps (for #security #vulnerability testing). Such a cool thing to do!https://t.co/AV6KSdzX16#infosec #bugbounty
— Arif Khan (@payloadartist) March 23, 2019
The "Whitehat Settings" option can be enabled on Facebook's main app, its Messenger instant messaging client, and the Instagram app. It is only supported on Facebook's Android apps, but not its iOS clients.
Once the feature is enabled, it also comes with its own settings, such as a built-in proxy for Facebook Platform API interactions, the ability to disable Facebook's TLS 1.3 support, and the option to use user-installed certificates for easier traffic interception.
The "Whitehat Settings" feature can be enabled by visiting this Facebook settings page, with additional details and video tutorials on this support page.
Facebook recommends that security researchers turn this feature off as soon as they stop testing for vulnerabilities, as it also weakens an account's overall security posture.
Facebook has always loved whitehat researchers
It's no surprise that Facebook modified its official apps to support and help whitehat security research. Facebook has always had a friendly approach towards the infosec community, being one of the few companies managing its own bug bounty program, offering large payouts on a regular basis, and often open-sourcing many security-focused tools.
After the Cambridge Analytica scandal last year, Facebook has intensified its efforts into improving the security of its main platform and mobile apps, but also its adjacent third-party app ecosystem.
Since March last year, Facebook started paying significant bug bounties to researchers who discover exposures of user data in popular Facebook third-party apps and games.
Since September, the social network also expanded its bug bounty program to offer rewards for finding cases where third-party services exposed Facebook user access tokens.
Two months later, in November, Facebook also began offering rewards of up to $40,000 to researchers who find vulnerabilities that lead to account takeovers.
Facebook's worst privacy scandals and data disasters
Related cyber-security coverage:
- Tesla car hacked at Pwn2Own contest
- Android ecosystem of pre-installed apps is a privacy and security mess
- Researchers find 36 new security flaws in LTE protocol
- Over 100,000 GitHub repos have leaked API or cryptographic keys
- Severe security bug found in popular PHP library for creating PDF files
- Hacked tornado sirens taken offline in two Texas cities ahead of major storm
- Facebook-Cambridge Analytica privacy scandal: Your data still isn't secure TechRepublic
- Android security program has helped fix over 1M apps in Google Play CNET