ISP involvement suspected in latest FinFisher gov't spyware campaign

A campaign utilizing a new variant of the government spying software FinFisher has spread, potentially with the help of Internet Service Providers.
FinFisher, also known as FinSpy, is a surveillance suite developed by Munich-based Gamma Group and is sold to government customers and law enforcement worldwide.
The malware -- which often avoids detection by traditional antivirus software -- can be used to monitor communication software such as Skype, eavesdrop on video chats, log calls, view and copy user files, and more.
Gamma Group says the malware "helps government law enforcement and intelligence agencies identify, locate and convict serious criminals."
According to ESET researchers, a new campaign spreading the malware has been detected in a total of seven countries. In two of them, Internet Service Providers (ISPs) are "most likely" working in collaboration with governments to infect targets of interest with the surveillance malware.
The countries have not been named due to safety concerns.
In a blog post, the research team said that FinFisher has been spread through man-in-the-middle (MiTM) attacks, which target communication relays to tamper with data streams, spy on users, and deploy malware.
"We believe that major internet providers have played the role of the man in the middle," said Filip Kafka, an ESET malware analyst.
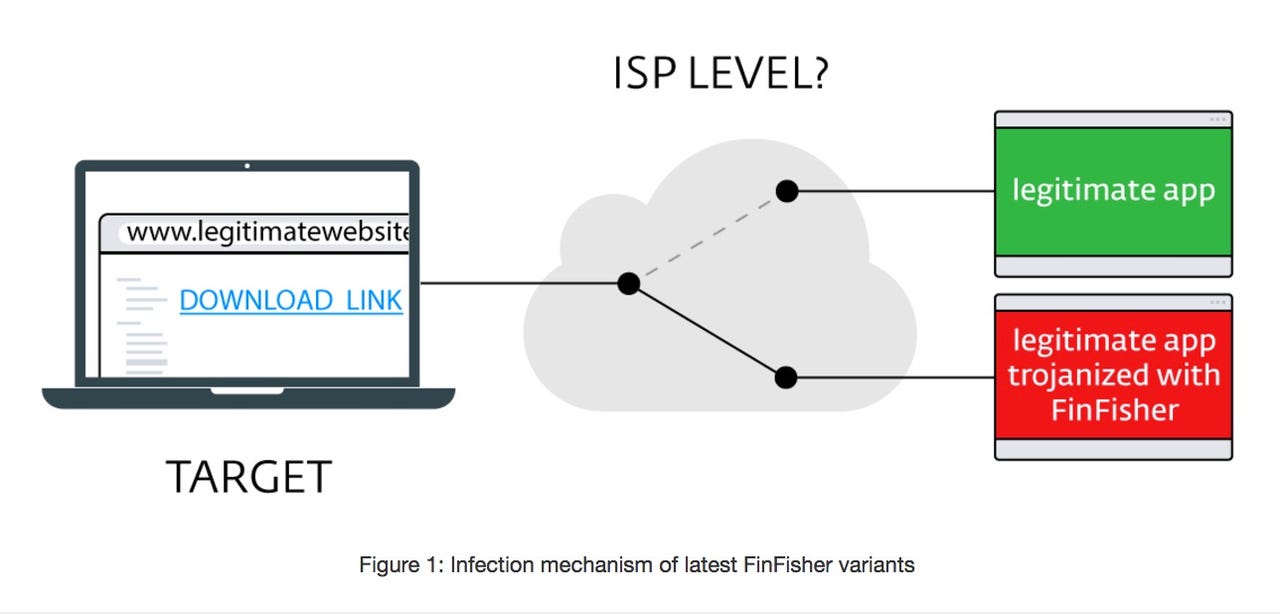
ESET says the latest variant has been deployed with a number of improvements designed to avoid detection and analysis. Rather than rely on fake Flash plugins or older infection techniques such as watering holes or spearphishing, FinFisher can now infect systems when users are attempting to download a popular application such as WhatsApp, Skype, Avast, WinRAR, or VLC Player.
With a successful MiTM attack in play, the target is redirected to the attacker's server, which installs a malicious file containing a Trojan that deploys FinFisher. However, the legitimate app is also installed to prevent suspicion.
In addition, the latest version of the malware uses custom code virtualization to protect the majority of its components, including the kernel-mode driver, as well as anti-disassembly tricks which prevent sandboxing, debugging, and emulation -- making the job of security analysts difficult when it comes to picking apart the malicious code.
"During the course of our investigations, we found a number of indicators that suggest the redirection is happening at the level of a major internet provider's service," commented Kafka.
The new techniques have been used "at the ISP level" in two countries, whereas the other five are still relying on older techniques.
"It would be technically possible for the "man" in these man-in-the-middle attacks to be situated at various positions along the route from the target's computer to the legitimate server (e.g. compromised Wi-Fi hotspots)," ESET notes. "However, the geographical dispersion of ESET's detection of latest FinFisher variants suggests the MitM attack is happening at a higher level - an ISP arises as the most probable option."
As Gamma Group also offers a solution called "FinFly ISP," which can be deployed on ISP networks to distribute this malware, it may indeed be possible that subscribers are being placed at risk by these companies working in collusion.
"The deployment of the ISP-level MitM attack technique mentioned in the leaked documents has never been revealed -- until now," the team says. "If confirmed, these FinFisher campaigns would represent a sophisticated and stealthy surveillance project unprecedented in its combination of methods and reach."
Previous and related coverage
- In Hacking Team's wake, FinFisher spyware rises in popularity with government users
- FinFisher spyware linked to Indonesian government found in Sydney: Report
- Top gov't spyware company hacked; Gamma's FinFisher leaked