LinkedIn bug allowed data to be stolen from user profiles

(Image: ZDNet)
A bug in how LinkedIn autofills data on other websites could have allowed an attacker to silently steal user profile data.
The flaw was found in LinkedIn's widely used AutoFill plugin, which allows approved third-party websites to let LinkedIn members automatically fill in basic information from their profile -- such as their name, email address, location, and where they work -- as a quick way to sign up to the site or to receive email newsletters.
Security
LinkedIn only allows whitelisted domains to have this functionality, and LinkedIn has to approve each new domain. Right now, there are dozens of sites in the top 10,000 websites ranked by Alexa that have been whitelisted by LinkedIn, including Twitter, Microsoft, LinkedIn, and more.
That means any of those websites can retrieve this profile data from users without their approval.
But if any of the sites contains a cross-site scripting (XSS) flaw -- which lets an attacker run malicious code on a website -- an attacker can piggy-back off that whitelisted domain to obtain data from LinkedIn.
And it turns out that at least one of them did.
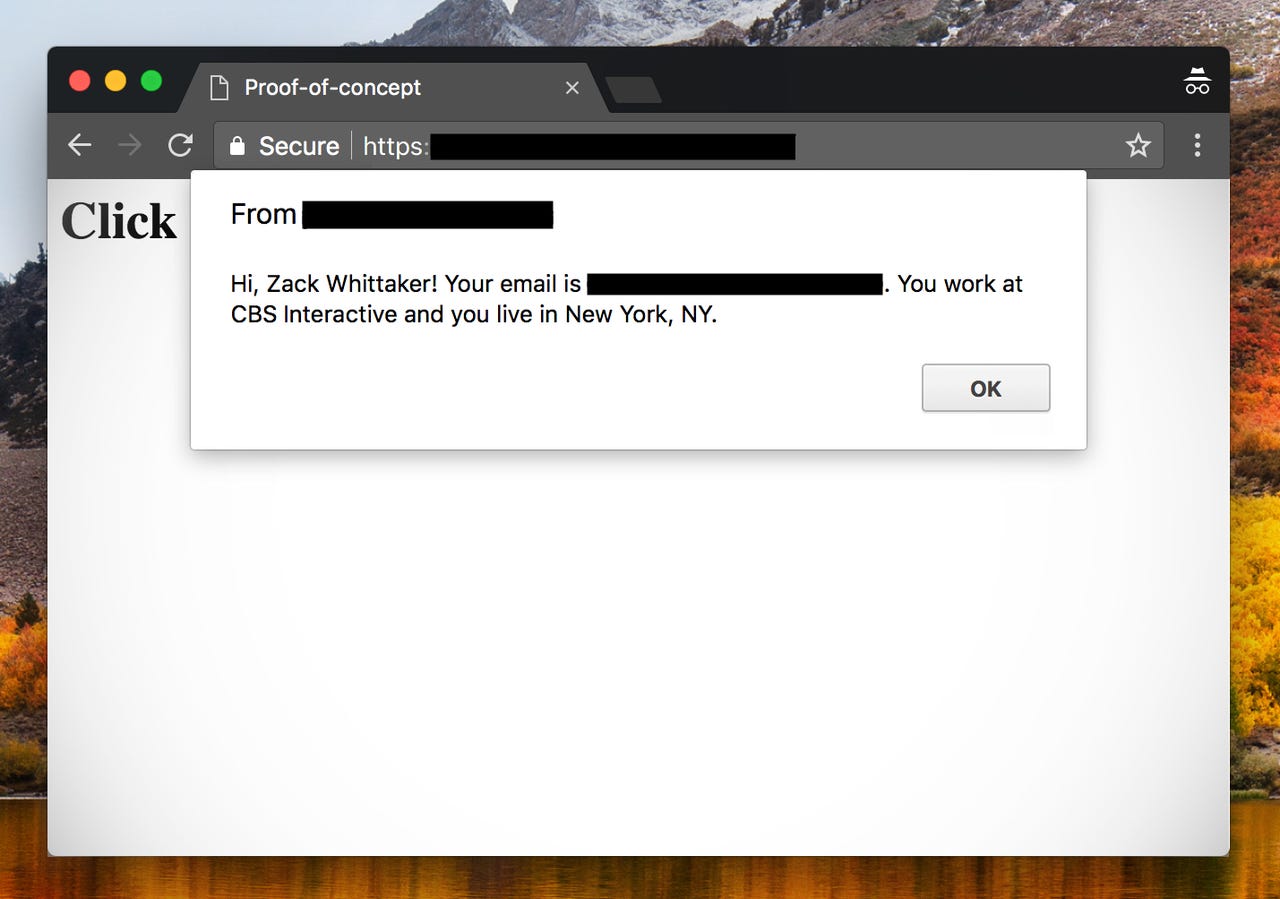
"A user's information can be unwillingly exposed to any website simply by clicking somewhere on the page," said Jack Cable, in a detailed write-up posted Thursday. "This is because the AutoFill button could be made invisible and span the entire page, causing a user clicking anywhere to send the user's information to the website."
Cable reached out to ZDNet after LinkedIn failed to fix the bug the first time around, and did not respond to his later email about the bug that affected whitelisted domains.
LinkedIn confirmed that the bug was eventually fixed Thursday following Cable's disclosure.
He also built a proof-of-concept code to demonstrate the flaw.
An XSS flaw in a LinkedIn-whitelisted website -- which we are not naming -- allowed him to silently run the proof-of-concept code from his own server. The page loaded, and then a message said: "Click anywhere on the page." That's when a box appeared revealing the user's information.
Like with any XSS flaw, this data could be sent to a malicious actor's server.
"That this exposes a user's information regardless of their privacy settings," said Cable. "For instance, if I set my privacy settings to not display my last name or email address and display a general location, this still returns my full name, email address, and zip code."
Email addresses are never displayed on LinkedIn profiles -- unless the user puts it there themselves. That's not only to prevent spam, but also as a security measure, as the email addresses collected by the AutoFill bug are used to log-in to the site.
LinkedIn AutoFill also returned a user's phone number if present, though the proof-of-concept did not display it on the popup. (We verified by checking the JavaScript Console in Chrome.)
"We immediately prevented unauthorized use of this feature, once we were made aware of the issue," a LinkedIn spokesperson said.
"While we've seen no signs of abuse, we're constantly working to ensure our members' data stays protected. We appreciate the researcher responsibly reporting this and our security team will continue to stay in touch with them," the spokesperson added.