Microsoft Windows zero-day disclosed on Twitter, again

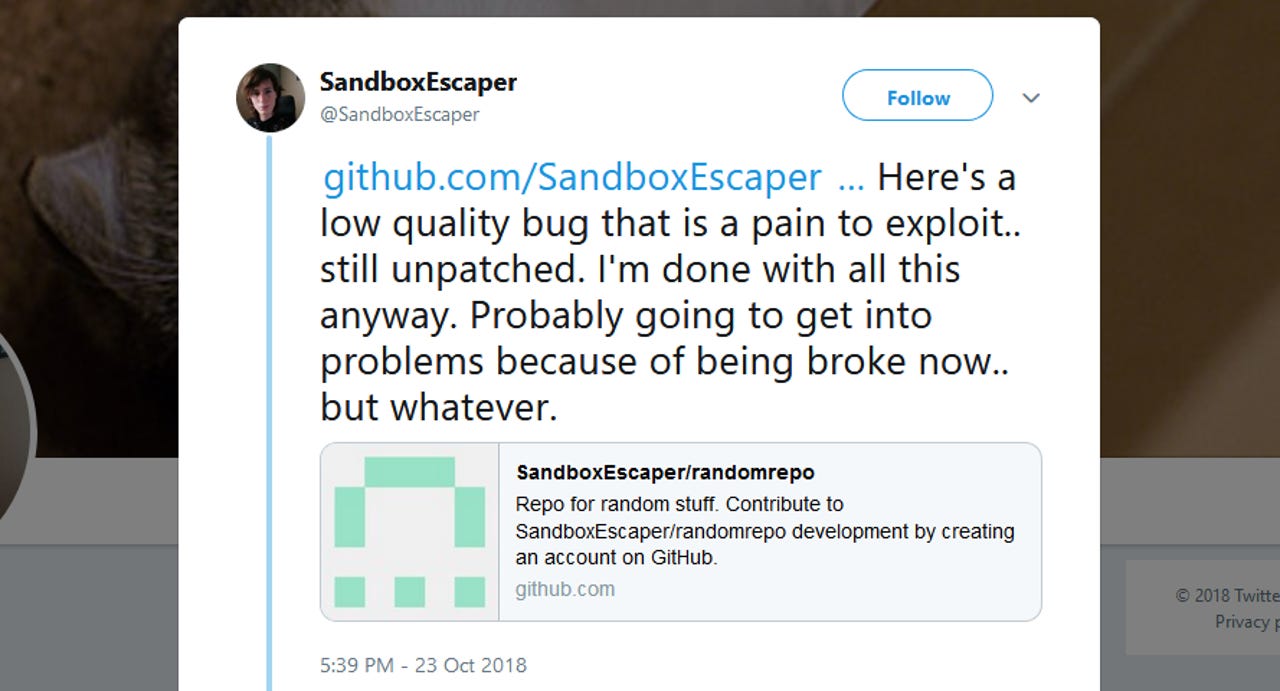
A security researcher has disclosed a Windows zero-day vulnerability on Twitter for the second time in the span of two months. The researcher, who goes online by the pseudonym of SandboxEscaper, also published proof-of-concept (PoC) on GitHub.
Security
This second Windows zero-day affects the Microsoft Data Sharing (dssvc.dll), a local service that provides data brokering between applications.
According to several security experts who analyzed the zero-day's PoC, an attacker can use it to elevate their privileges on systems they already have access to.
The PoC, in particular, was coded to delete files for which a user would normally need admin privileges to do so. With the appropriate modifications, other actions can be taken, experts believe.
The zero-day only affects recent versions of the Windows OS, such as Windows 10 (all versions, including the latest October 2018 Update), Server 2016, and even the new Server 2019, according to several security experts who confirmed the PoC.
According to Will Dormann of CERT/CC, this is because the "Data Sharing Service (dssvc.dll), does not seem to be present on Windows 8.1 and earlier systems."
Today's zero-day is also almost identical to SandboxEscaper's first zero-day that she also published on Twitter at the end of August, according to infosec sleuth Kevin Beaumont.
"It allows non-admins to delete any file by abusing a new Windows service not checking permissions again," Beaumont said in a tweet.
Mitja Kolsek, co-founder and CEO of ACROS Security, advised users against running SandboxEscaper's recent PoC. While the PoC for the first zero-day wrote garbage data to a Windows PC, the PoC for the second zero-day will delete crucial Windows files, crashing the operating system, and forcing users through a system restore process.
Malware authors were quick to integrate SandboxEscaper's first zero-day --a local privilege escalation in the Advanced Local Procedure Call (ALPC) service-- inside malware distribution campaigns.
Microsoft eventually patched the issue a week after the bug was used in the wild, during the September 2018 Patch Tuesday updates.
SandboxEscaper argues that this second zero-day can be just as useful for attackers as the first. The expert believes malware authors can use the zero-day to delete OS files or DLLs and replace them with malicious versions.
Just like it did for the first zero-day, Kolsek's company released an update for their product (called 0Patch) that would block any exploitation attempts until Microsoft releases an official fix. Kolsek and his team are currently working on porting their "micro-patch" to all affected Windows versions.
Contacted by ZDNet after the researcher dropped the zero-day on Twitter, Microsoft offered the following statement:
"Windows has a customer commitment to investigate reported security issues, and proactively update impacted devices as soon as possible. Our standard policy is to provide solutions via our current Update Tuesday schedule."
Article updated on October 24, 09:00 AM ET with statement from Microsoft.
RELATED ZERO-DAY COVERAGE:
- Magecart group leverages zero-days in 20 Magento extensions
- Zero-day in popular jQuery plugin actively exploited for at least three years
- Researcher finds simple way of backdooring Windows PCs
- New Flash 0-day exploit bypasses browser, infects via Office instead TechRepublic
- Microsoft October 2018 Patch Tuesday fixes 0-day exploited by FruityArmor APT
- Apple MacOS Mojave zero-day privacy bypass vulnerability revealed