More than 6,700 VMware servers exposed online and vulnerable to major new bug

More than 6,700 VMware vCenter servers are currently exposed online and vulnerable to a new attack that can allow hackers to take over unpatched devices and effectively take over companies' entire networks.
Scans for VMware vCenter devices are currently underway, according to threat intelligence firm Bad Packets.
We've detected mass scanning activity targeting vulnerable VMware vCenter servers (https://t.co/t3Gv2ZgTdt).
— Bad Packets (@bad_packets) February 24, 2021
Query our API for "tags=CVE-2021-21972" for relevant indicators and source IP addresses. #threatintel https://t.co/AcSZ40U5Gp
The scans have started earlier today after a Chinese security researcher published proof-of-concept code on their blog for a vulnerability tracked as CVE-2021-21972.
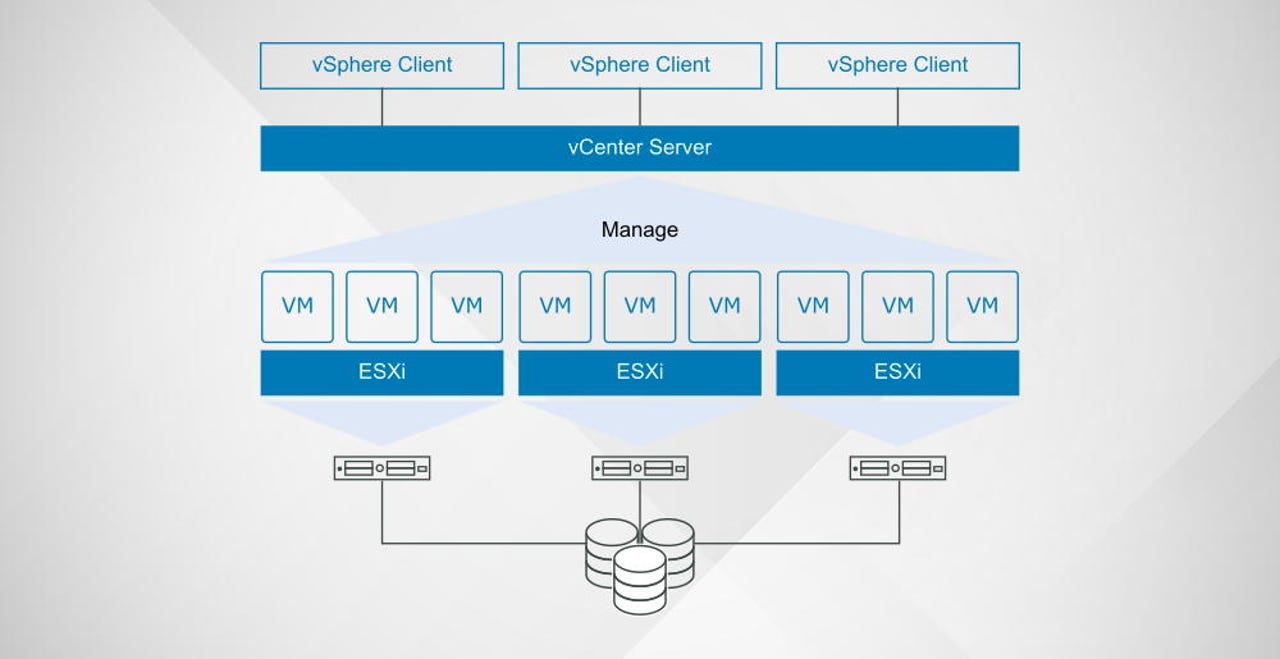
This vulnerability impacts vSphere Client (HTML5), a plugin of VMware vCenter, a type of server usually deployed inside large enterprise networks as a centralized management utility through which IT personnel manage VMware products installed on local workstations.
Last year, security firm Positive Technologies discovered that an attacker could target the HTTPS interface of this vCenter plugin and execute malicious code with elevated privileges on the device without having to authenticate.
Because of the central role of a vCenter server inside corporate networks, the issue was classified as highly critical and privately reported to VMware, which released official patches yesterday, on February 23, 2021.
Due to the large number of companies that run vCenter software on their networks, Positive Technologies initially planned to keep details about this bug secret until system administrators had enough time to test and apply the patch.
However, the proof-of-concept code posted by the Chinese researcher, and others, effectively denied companies any grace period to apply the patch and also started a free-for-all mass-scan for vulnerable vCenter systems left connected online, with hackers hurrying to compromise systems before rival gangs.
Making matters worse, the exploit for this bug is also a one-line cURL request, which makes it easy even for low-skilled threat actors to automate attacks.
There’s a preauth RCE in vSphere with a single HTTP get request, which some orgs face to internet. https://t.co/rKxbQANQ8n
— Kevin Beaumont (@GossiTheDog) February 24, 2021
According to a Shodan query, more than 6,700 VMware vCenter servers are currently connected to the internet. All these systems are now vulnerable to takeover attacks if administrators failed to apply yesterday's CVE-2021-21972 patches.
VMware has taken this bug very seriously and has assigned a severity score of 9.8 out of a maximum of 10 and is now urging customers to update their systems as soon as possible.
Due to the critical and central role that VMware vCenter servers play in enterprise networks, a compromise of this device could allow attackers access to any system that's connected or managed through the central server.
These are the types of devices that threat actors (known as "network access brokers") like to compromise and then sell on underground cybercrime forums to ransomware gangs, which then encrypt victims' files and demand huge ransoms. Furthermore, ransomware gangs like Darkside and RansomExx have already started going after VMware systems last year, showing just how effective targeting these VM-based enterprise networks can be.
Since a PoC is now out in the open, Positive Technologies has also decided to publish an in-depth technical report on the bug, so network defenders can learn how the exploit work and prepare additional defenses or forensics tools to detect past attacks.