New WannaCrypt ransomware variant discovered in the wild

New ransomware samples of WannaCrypt variants have been discovered in the wild but it is yet to be seen if they pose the same threat as the first ransomware attack wave.
On Friday, at least 47 trusts across England and 13 National Health Service (NHS) services in Scotland were faced with severe disruption as IT services went into lockdown due to the Wanna Decryptor ransomware, also known as WannaCrypt, WanaCrypt0r and WannaCry.
Appointments were cancelled, the general public was urged to not visit NHS Accident & Emergency departments unless absolutely necessary and in some cases, patients were reportedly turned away or moved to other medical establishments as staff were forced to resort to pen-and-paper to try and maintain some order.
IT system provider NHS Digital said in a statement that the attack "was not specifically targeted at the NHS and is affecting organizations from across a range of sectors," words that soon rung true.
See also: Ransomware attack: Hospitals still struggling in aftermath of WannaCrypt's rampage
Following reports of the ransomware attack across the UK, researchers soon discovered instances of the same malware being used in thousands of attacks in 150 countries at last count, including the UK, Russia, and Spain. It is believed the ransomeware has claimed at least 200,000 victims.
Researchers have warned that more attacks may be on the way as the first wave struck on Friday, and in addition, new variants are appearing in the wild which could make fighting the ransomware even more complicated.
WannaCrypt infects vulnerable systems through phishing campaigns, malicious emails and malware-laden attachments in the typical way ransomware generally operates.
However, once one infection is successful, the ransomware then encrypts everything it can get its hands on -- including hard drives and external storage devices -- before performing a scan to find and jump to new systems which are not protected against the malware.
According to security firm Recorded Future, WannaCry first appeared on 31 March but the version now appearing in attacks has been modified, such as the inclusion of "worm-like" capabilities which allow the malware to spread through any networked systems which have not been patched via NetBIOS.
The ransomware uses a known Microsoft Windows Server Message Block (SMB) vulnerability, EternalBlue (MS17-010), which is a bug in Windows SMBv1 and SMBv2.
The security flaw is reportedly one of the same zero-day vulnerabilities released as part of the Shadow Brokers NSA cache.
In addition, as noted by McAfee researchers, the malware generates random IP addresses which are not limited to local networks, and with this, WannaCry may also be able to spread through the web if sites allow NetBIOS packets from outside networks.
"This could be one reason for the widespread infection seen in this outbreak and why many people are unsure about the initial infection vector of the malware," McAfee says.
A British security researcher using the Twitter handle MalwareTech accidentally slowed the spread of the ransomware over the weekend by registering a domain name discovered in the ransomware's code.
As described in the researcher's blog post, rather than acting as a "kill switch," the domain name inclusion was likely "badly thought out anti-analysis."
"I believe they were trying to query an intentionally unregistered domain which would appear registered in certain sandbox environments, then once they see the domain responding, they know they're in a sandbox [and] the malware exits to prevent further analysis," the researcher says.
By registering the domain in question, MalwareTech was then able to create a sinkhole to dupe the ransomware's SMB module connecting to the domain into believing it was in a sandbox environment, therefore preventing new computers infected with the sample from being ransomed.
However, the ransomware can still spread through normal means and if the operators choose to remove a domain check component, the sinkhole will no longer be effective.
"One thing that is very important to note is our sinkholing only stops this sample and there is nothing stopping them removing the domain check and trying again, so it's incredibly important that any unpatched systems are patched as quickly as possible," MalwareTech says.
On Sunday, security researcher Matthieu Suiche also revealed the existence of two new variants of WannaCry.
One of the variants, discovered by researcher Benkow, was reverse-engineered by Suiche who found another domain link hidden in the code. In the same way as MalwareTech, Suiche immediately registered this second domain to sinkhole the address and prevent networked new infections taking place.
Security
The second is only partially operational due to a corrupted archive. This variant was recovered by Costin Raiu, Director of Global Research and Analysis Team at Kaspersky Labs as a Virus Total upload, and as the ransomware archive is corrupted, can still spread but is not fully functional.
No successful infections from this particular strain have yet been reported.
"The fact I registered the new kill-switch today to block the new waves of attacks (sinkhole.tech reported to me they are receiving hits) is only a temporary relief which does not resolve the real issue which is that many companies and critical infrastructures are still dependent on legacy and out of support operating systems," the researcher says.
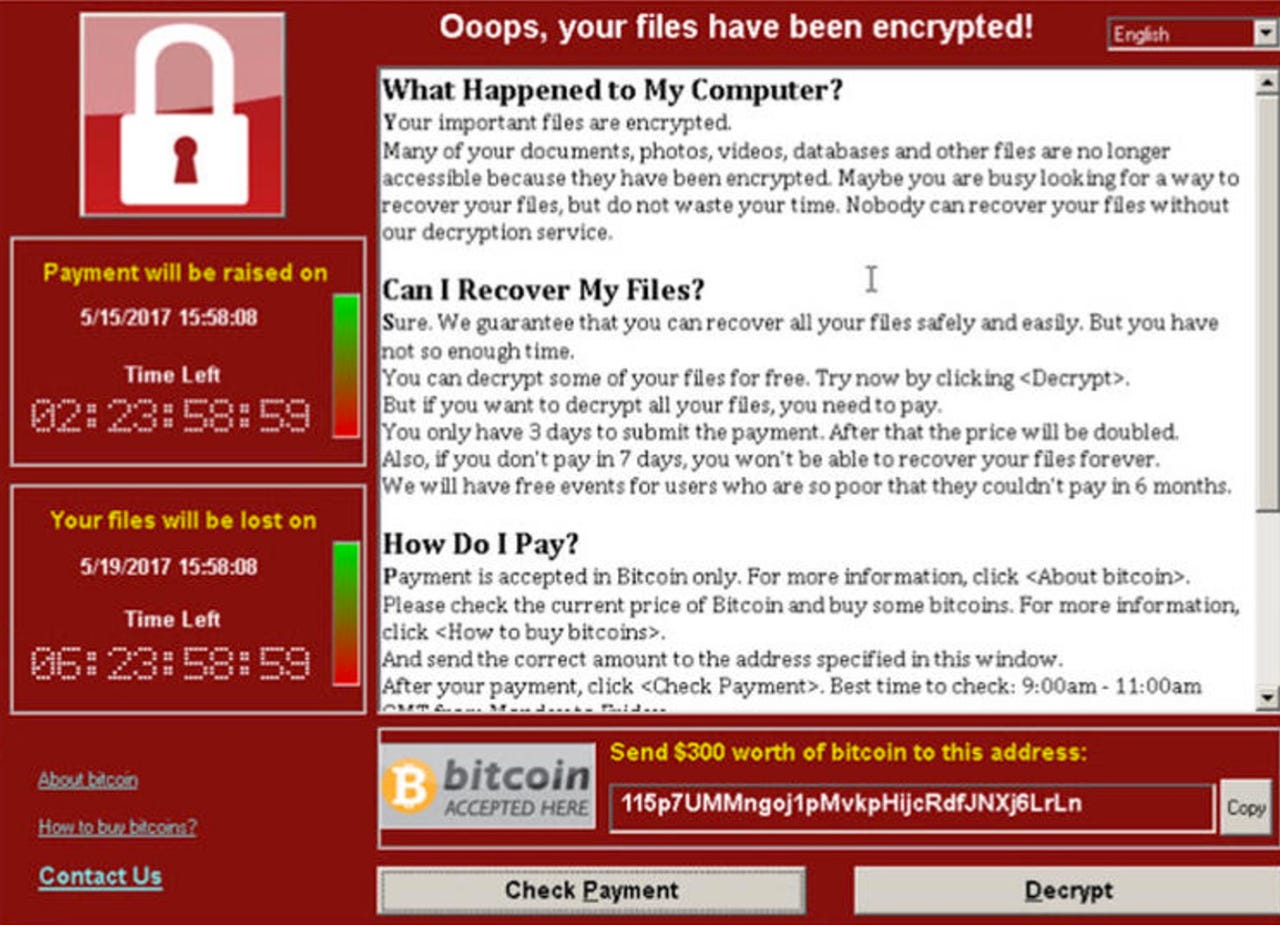
The malware demands $300 in the virtual currency Bitcoin, a ransom demand which doubles after three days of non-payment.
To put even more pressure on individuals, governments, and businesses impacted by the ransomware, the operators also threaten to delete all files permanently if payment is not made within a week. In total, users may be able to decrypt up to 10 files for free.
See also: Hey cyber techbros, smugly yelling 'patch and back-up' won't fix ransomware
Two of the attacker's domains propagating and controlling the ransomware spread have been sinkholed and it appears that the threat actors, despite widespread infection, have not made quite as much money as you may think.
Three Bitcoin wallet addresses (1,2,3) linked to the campaign show that at the time of writing, approximately 25 BTC has been paid to the attackers, which equates to roughly $44,000.
The flaw was patched earlier this year, but old, unsupported systems were left out of the release. Users of Windows 10 are not affected.
To try and stem the flow of attacks, Microsoft took an unusual step and issued an emergency patch for Windows XP and other older versions of Windows which are no longer officially supported without special support contracts.
In a blog post, Microsoft said, "this decision was made based on an assessment of this situation, with the principle of protecting our customer ecosystem overall, firmly in mind."
You can view a live update map of the WannaCry spread here.