Official Monero website compromised with malware that steals funds

Compromised Monero file, highlighted in red
The official website of the Monero cryptocurrency has been compromised to deliver a malware-infected file that steals funds from account owners.
The compromise happened yesterday, November 18. A user spotted the compromised filed and reported the issue on GitHub, with the Monero team confirming the hack in a tweet earlier today.
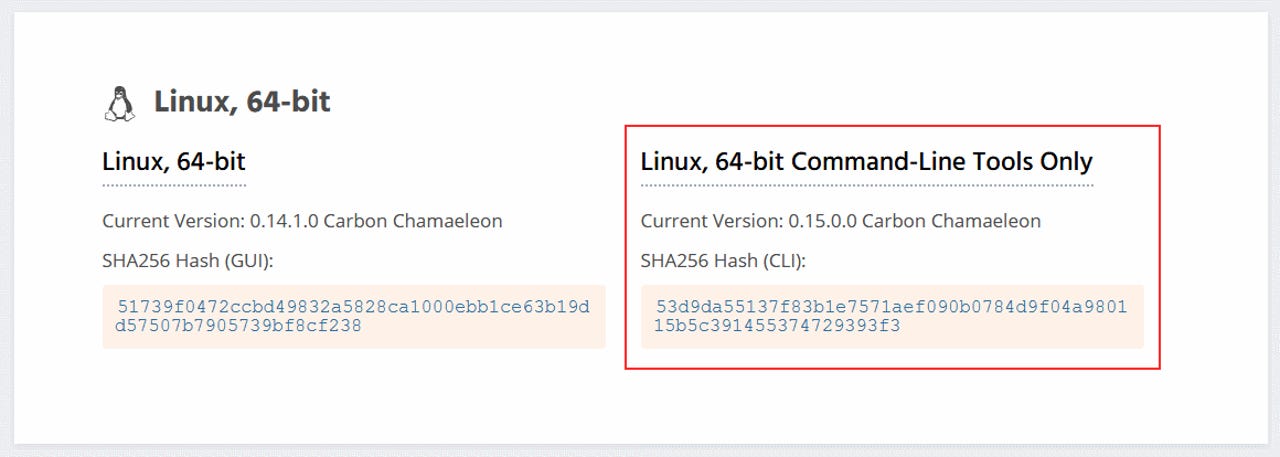
The hack was discovered after the user downloaded a 64-bit Linux binary for working with Monero cryptocurrency from the Linux command-line interface.
After downloading the installer from the official website, the user noticed that the SHA256 hash for the downloaded file did not match the SHA256 hash listed on the official site -- meaning that the file had been altered.
Monero team confirms hack, still investigating
"It's strongly recommended to anyone who downloaded the CLI wallet from this website between Monday 18th 2:30 AM UTC and 4:30 PM UTC, to check the hashes of their binaries. If they don't match the official ones, delete the files and download them again. Do not run the compromised binaries for any reason," the Monero team said in a blog post earlier today.
Although the Monero team claims it intervened to take down the compromised file, at least one user reported losing funds.
"I can confirm that the malicious binary is stealing coins. Roughly 9 hours after I ran the binary a single transaction drained the wallet of all $7000," said a user in a Reddit comment.
At the time of writing, the Monero team said it was still investigating how the hacker (group) compromised its download server. Downloads should be safe now, they said, as they're being delivered from a "fallback source."
While it's unclear how many users lost funds in this hack, the incident shows how important a simple action like verifying file hashes for recently downloaded files can sometimes be -- a practice that very few people follow.
A version of the malware-infected Monero Linux CLI binary is available for download from here (for reverse-engineering purposes, DON'T RUN). A VirusTotal scan is available here.
Article updated on November 19, 03:00pm ET, with new statement from Monero team, widening the site compromise window from 35 minutes to 14 hours. Article updated again at 07:00am ET to add a link to an analysis of the malware that was found in the Monero Linux CLI binary. The researcher points out that he also found a Windows version of the malware on an attacker's server, yet there are no reports that the Windows CLI tools binaries on the Monero site have been compromised as well.