Qihoo & Baidu disrupt malware botnet with hundreds of thousands of victims

Because Chinese users usually hang out in their own corner of the internet, behind the Great Firewall, we tend to forget that they are also targeted by malware on a daily basis; albeit different malware, and not usually the same that targets everyone else.
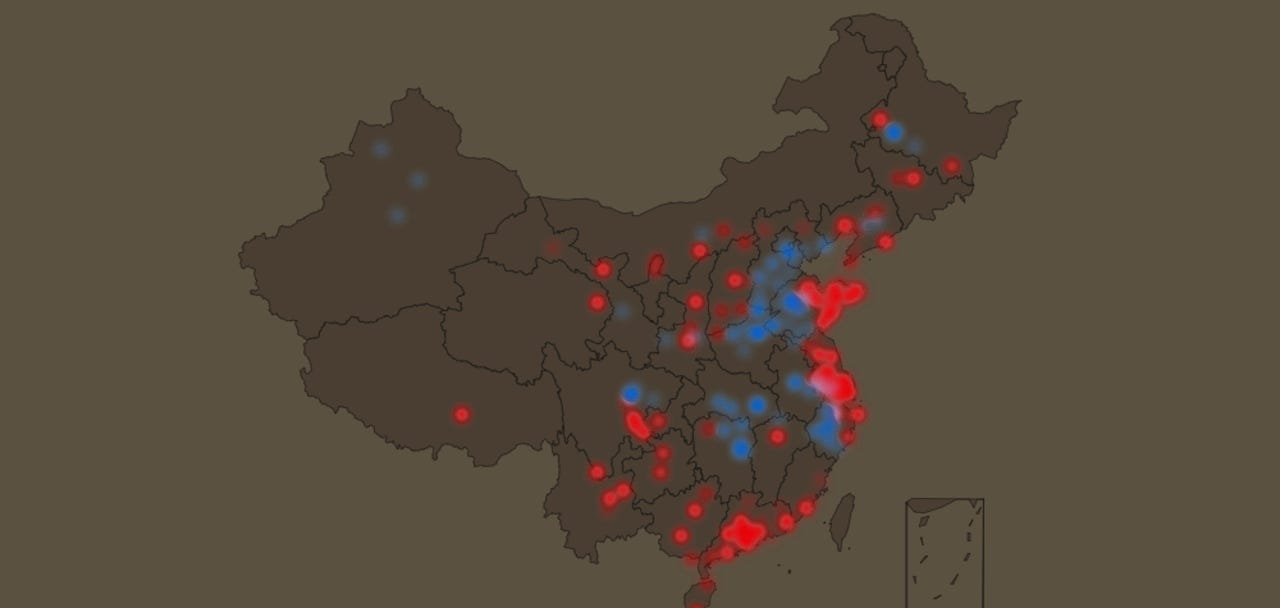
For the past three years, the DoubleGuns trojan has emerged to take the crown as one of China's largest malware botnets.
In an interview with ZDNet earlier today, Chinese antivirus vendor Qihoo 360 says DoubleGuns is exclusively found in China and is believed to have infected hundreds of thousands of Chinese users at the time of writing, with millions of historical infections over the past years.
What is DoubleGuns
DoubleGuns is a malware trojan that targets Windows devices. The malware has been operating since July 2017 when Qihoo researchers spotted the first samples distributed in the wild.
Across the past three years, the DoubleGuns trojan has changed very little, despite growing in scale. To this day, the malware is still primarily distributed via boobytrapped apps shared on Chinese websites, with most being pirated games made available on Chinese social networks and gaming forums.
Its primary purpose is still to infect users with MBR and VBR bootkits, install various malicious drivers, and then steal credentials from local apps, with a focus on Steam accounts.
In addition, DoubleGuns also acts as adware and spamming module. It inserts ads on user devices, and it also hijacks QQ accounts to spread ads to the victim's friends via private messages.
Furthermore, older versions of the DoubleGuns malware were also spotted hijacking traffic from legitimate e-commerce portals, redirecting infected users to clone sites; however, this behavior appears to have been dropped in recent versions.
As mentioned above, the trojan targets Chinese users exclusively, and this is very clear when analyzing the malware's source code, which includes functions to disable security software, most of which are Chinese antivirus products.
Qihoo and Baidu temporarily disrupt DoubleGuns
In a blog post last week, Qihoo 360 says it recently teamed up with fellow Chinese tech giant Baidu to disrupt the botnet's operations, which have grown too large to be ignored.
Qihoo says that since May 14, they've been working with Baidu in a joint operation to take down some of the botnet's backend infrastructure, most of which has been using Baidu's Tieba image hosting service.
According to Qihoo, for the past three years, DoubleGuns has been downloading images from the Tieba service. The images contained secret code (hidden inside the image using a technique known as steganography) that provided DoubleGun bots with instructions of what operations to perform on the infected hosts.
Qihoo and Baidu say that for the past two weeks, they've been taking down images used by DoubleGuns and logging connections from infected hosts, which is how they found about the botnet's massive size, currently estimated at "hundreds of thousands" of infected computers.
The disruption is considered temporary, as other parts of the botnet's infrastructure are still running, and the botnet's operators are still at large.