Report says strong authentication use lagging in federal agencies

An annual government report shows that nearly a third of 70,000 reported information security incidents reported by U.S. federal agencies were related to or could potentially have been prevented by the use of strong authentication.
While adoption of strong authentication by federal agencies showed small gains over the past fiscal year, adoption remains stacked in a few agencies and below stated goals or non-existent in most others.
The report on the Federal Information Security Management Act (FISMA) covers Oct. 1, 2013 to Sept. 30, 2014 and is prepared annually for Congress by the Office of Management and Budget (OMB).
The report shows a handful of agencies had yet to deploy any strong authentication by September 2014, even though it is a priority goal for agencies.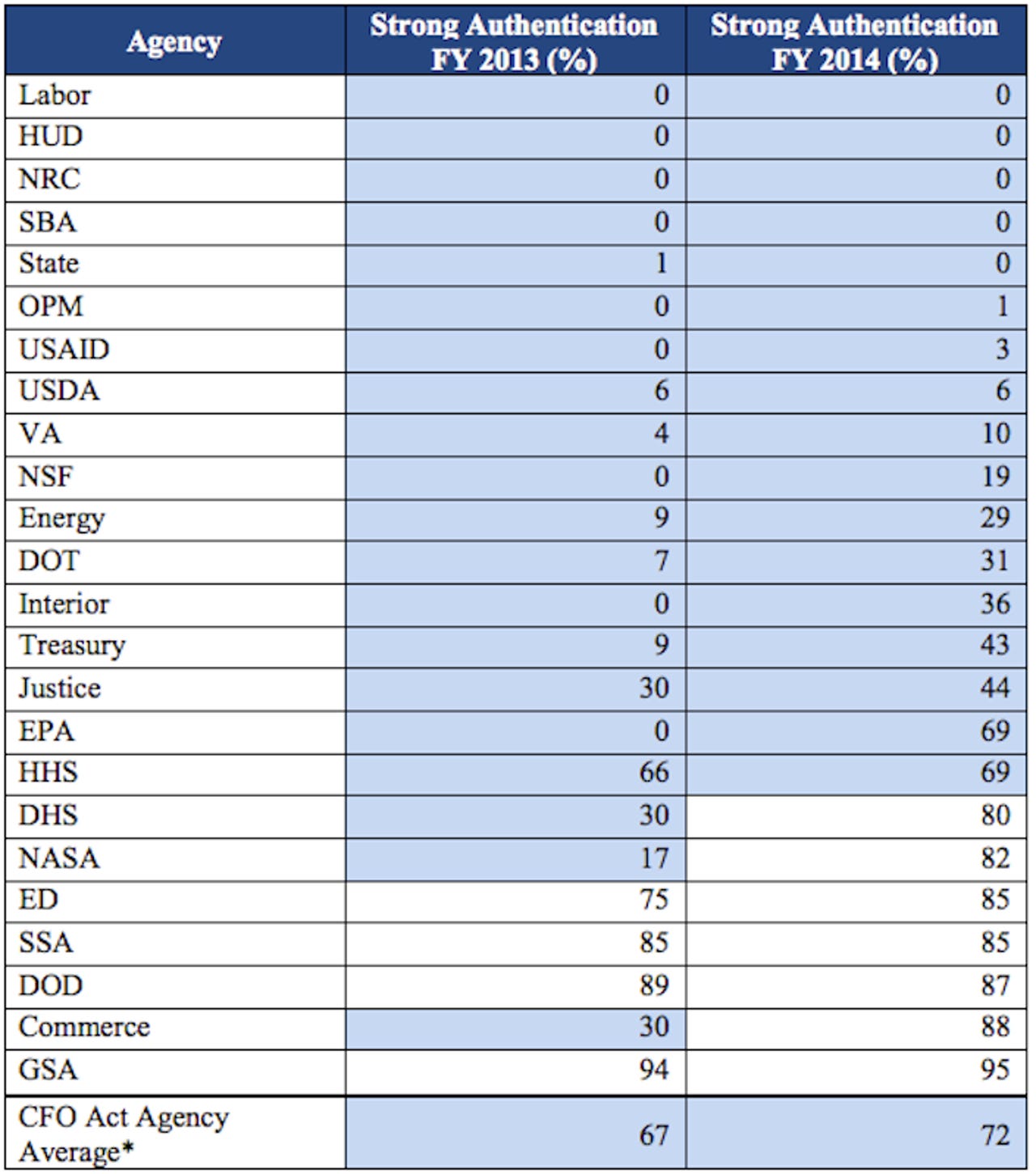
The overall goal was to have 75 percent of each agency's end-users required to use strong authentication, but the report showed only a rate of 41 percent across agencies when subtracting out the size and strong performance of the Department of Defense (DOD), which came in at 87 percent . Only seven of 24 agencies met the 75 percent goal, and 15 agencies have yet to reach even 50 percent implementation, with five of those agencies having no strong authentication implemented. Last year, nine agencies had yet to implement any strong authentication.
The report said these numbers are troubling and raise security concerns.
Not surprisingly, the report found that agencies with the weakest authentication profile allow the majority of unprivileged users to log-in using only a user ID and password.
On the positive side, the Department of Commerce saw a dramatic increase in the use of strong authentication from 30 percent to 88 percent as compared to fiscal year 2013, while the Environmental Protection Agency jumped from 0 percent to 69 percent.
In addition, the report showed that the average percentage of users across agencies required to log-on using Personal Identity Verification (PIV) cards rose from 67 percent to 72 percent, a 7.4 percent increase.
The report highlighted two federal cybersecurity incident types where strong authentication potentially could have mitigated security issues:
- Improper Usage, Suspicious Network Activity, and Unauthorized Access: Improper user behavior can be deterred by reducing anonymity through strong authentication.
- Social Engineering, Phishing, and Malicious Code: These can be deterred through use of PIV-card features such as digitally signing emails, and user training to thwart phishing attacks.
While strong authentication for the federal Cybersecurity Cross Agency Priority (CAP) Goal specifically calls for implementation of PIV-based two-factor authentication, the implementation of non-PIV two-factor authentication is still considered a positive cybersecurity measure, the report said.