Researchers break digital signatures for most desktop PDF viewers

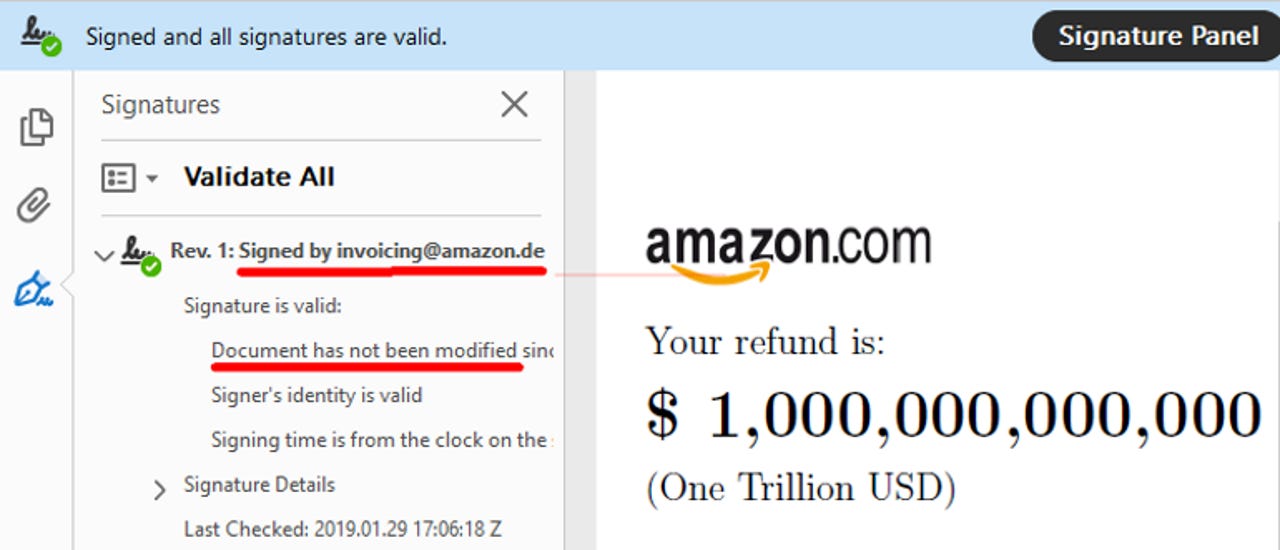
A team of academics from the Ruhr-University Bochum in Germany say they've managed to break the digital signing system and create fake signatures on 21 of 22 desktop PDF viewer apps and five out of seven online PDF digital signing services.
This includes apps such as Adobe Acrobat Reader, Foxit Reader, and LibreOffice, and online services like DocuSign and Evotrust --just to name the most recognizable names.
The five-person research team has been working since early October 2018 together with experts from Germany's Computer Emergency Response Team (BSI-CERT) to notify impacted services.
The team went public with their findings over the weekend after all affected app makers and commercial companies finished patching their products.
The reason why researchers were willing to wait months so all products would receive fixes is because of the importance of PDF digital signatures.
Digitally signed PDF documents are admissible in court, can be used as legally-binding contracts, can be used to approve financial transactions, can be used for tax filing purposes, and can be used to relay government-approved press releases and announcements.
Having the ability to fake a digital signature on an official PDF document can help threat actors steal large amounts of money or cause chaos inside private companies and public institutions.
In research published today, the Ruhr-University Bochum team described three vulnerabilities that they found in the digital signing process used by several desktop and web-based PDF signing services. Summarized, they are:
- Universal Signature Forgery (USF) - vulnerability lets attackers trick the signature verification process into showing users a fake panel/message that the signature is valid.
- Incremental Saving Attack (ISA) - vulnerability lets attackers add extra content to an already signed PDF document via the "incremental saving (incremental update)" mechanism, but without breaking the already-existing signature.
- Signature Wrapping (SWA) - vulnerability is similar to ISA, but the malicious code also contains extra logic to fool the signature validation process into "wrapping" around the attacker's extra content, effectively digitally signing the incremental update.
At the end of this article are images showing which PDF apps and web-based PDF signing services were vulnerable and to what of the three vulnerabilities.
"If you use one of our analyzed Desktop Viewer Applications you already should have got an update for your reader," researchers said. Users who haven't installed any updates to their PDF apps lately should look into updating their client to prevent it from loading forged digitally signed PDF docs. The web services listed in the report fixed the issues by applying server-side fixes.
"Currently, we are not aware of any exploits using our attacks," researchers said.
Additional details about the three vulnerabilities are available in this PDF research paper [1, 2], this blog post, and this dedicated website.
Create your own free Adobe Creative Cloud with free and open source software
Related cybersecurity news coverage:
- Microsoft Edge lets Facebook run Flash code behind users' backs
- A third of all Chrome extensions request access to user data on any site
- ICANN: There is an ongoing and significant risk to DNS infrastructure
- New browser attack lets hackers run bad code even after users leave a web page
- Cisco patches a couple of root access-granting security flaws
- Microsoft publishes security alert on IIS bug that causes 100% CPU usage spikes
- Major vulnerability found in Android ES File Explorer app TechRepublic
- Xiaomi electric scooter reportedly vulnerable to hijacking hack CNET