Trend Micro finds CEOs are spoofed the most by business email compromise

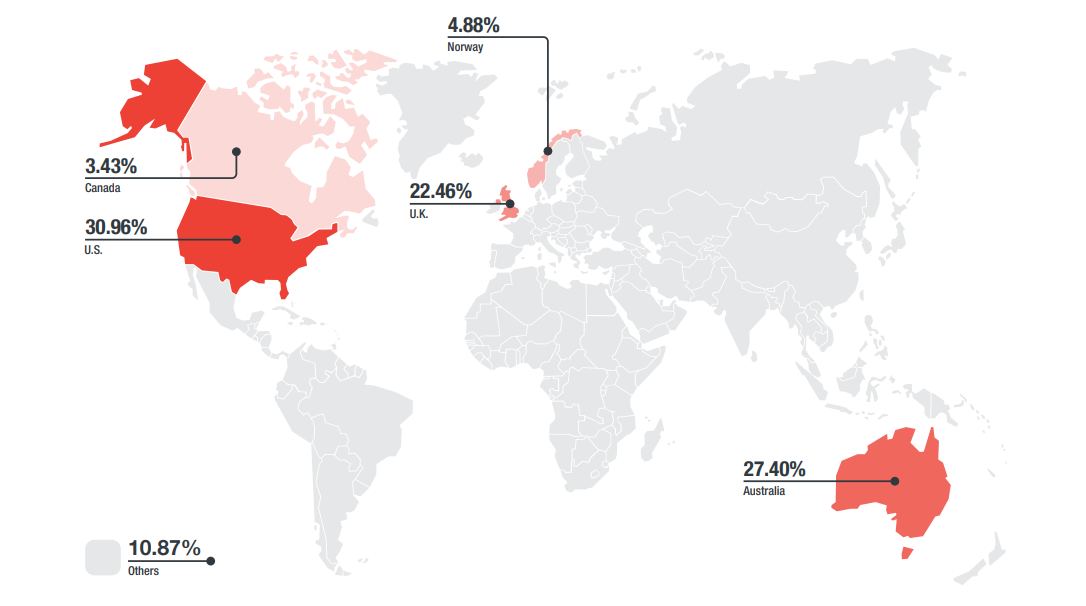
Countries with the most BEC attempts in the first-half of 2017
According to the Federal Bureau of Investigation (FBI), global losses from business email compromise (BEC) since 2013 have reached $5.3 billion, with a mid-year report from Trend Micro highlighting that CEOs were spoofed the most by BEC attacks.
In its 2017 Midyear Security Roundup: The Cost of Compromise report, the security vendor said cybercriminals continued to use schemes such as bogus invoices or supplier swindles, and employ keylogger malware or HTML pages in phishing emails to spoof employees.
While CEOs were spoofed the most, managing directors and directors were fooled nearly as often, the report [PDF] explained.
Trend Micro revealed that CFOs were targeted the most by the 3,000-plus instances of BEC attempts, followed by other employees charged with handling financially sensitive information.
The United States copped the majority of attempted BEC attacks, with 30.96 percent, followed by Australia, with 27.4 percent. The United Kingdom was the target for 22.46 percent of BEC attacks, with Norway and Canada targeted substantially less, at 4.88 percent and 3.43 percent, respectively.
"Employee training on common BEC methods goes hand in hand with a holistic security solution in defending enterprises from a variety of BEC attacks," Trend Micro said. "From small businesses to large corporations, enterprises can become unwitting victims in the multibillion-dollar scam that is BEC."
The report also noted that enterprises suffered major losses from a variety of cyber attacks in the first half of 2017, with ransomware reaching its peak with WannaCry and Petya.
Both outbreaks caused global panic and caught many organisations off-guard, and despite the Petya outbreak appearing to mainly target Ukraine, organisations around the world found themselves victim to this cyber attack.
With the damage bill in the region of $300 million for shipping giant Maersk and £100 million for Reckitt Benckiser, known for Dettol cleaning products, Nurofen tablets, and Durex condoms, Petya also halted chocolate production at Cadbury on June 27, 2017 -- the day the outbreak came to light.
In the first half of the year, 382 new vulnerabilities were publicly disclosed by researchers and contributors from the Zero Day Initiative, the report notes. Although Adobe and Foxit saw an increase in vulnerability counts, major vendors such as Microsoft, Apple, and Google had noticeable drops compared to the second half of 2016.
"Aside from new and unpatched vulnerabilities, old ones can still be exploited if security updates are not deployed," Trend Micro said. "The WannaCry and Petya attacks, for example, exploited a vulnerability already addressed by an earlier patch. It is, however, not always easy or possible to regularly install and manage patches."
Although some businesses use legacy systems or are in the middle of replacing legacy systems that no longer receive patch updates, and many -- such as hospitals -- even have legacy equipment that is too critical to run the risk of mechanical breakdown when patches are installed, Trend Micro said such limitations and challenges should not stop enterprises from adopting security measures.
"Vulnerability shielding and virtual patching can help protect enterprises from both old and new threats -- for both old and new systems," the company wrote.
Additionally, Trend Micro said it blocked 38 billion threats during the first half of 2017 via its Smart Protection Network. It said most of the threats were emails that contained malicious content.