Two Android apps used in combat by US troops contained severe vulnerabilities

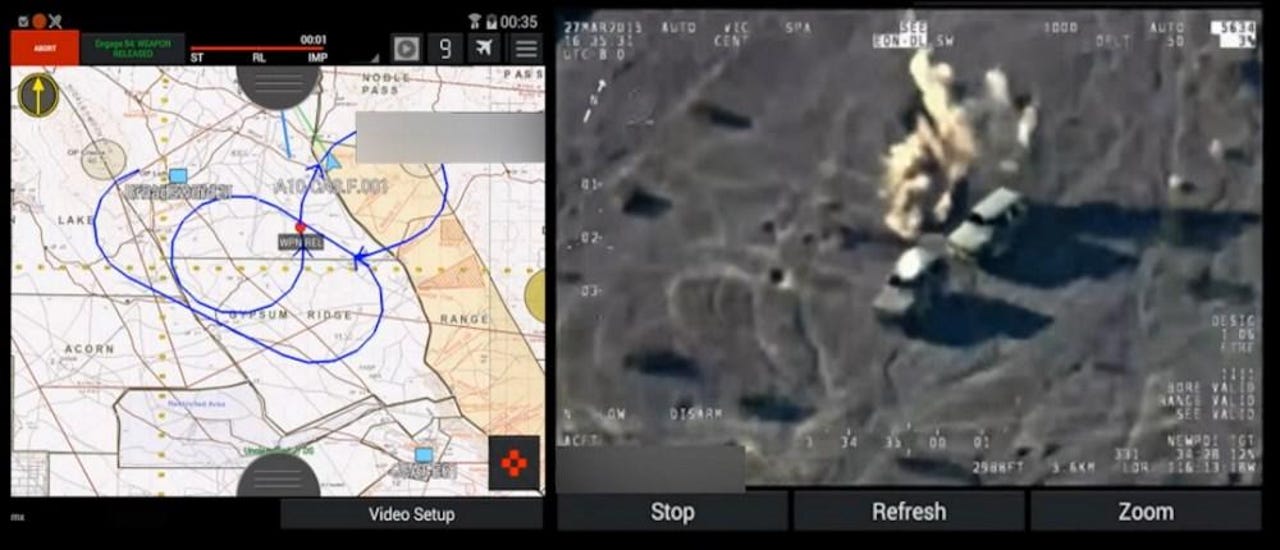
US military troops used two Android apps that contained severe vulnerabilities in live combat scenarios, a Navy Inspector General report revealed today.
Security
The two apps are named KILSWITCH (Kinetic Integrated Low-Cost Software Integrated Tactical Combat Handheld) and APASS (Android Precision Assault Strike Suite).
Both apps work by showing satellite imagery of surroundings, including objectives, mission goals, nearby enemy and friendly forces.
The two apps work as a modern-day replacement for radios and paper maps and allow troops to use a real-time messaging client to coordinate with other military branches, and even call in air-strike support with a few simple screen taps, according to a DARPA press release and accompanying YouTube video.
The apps have been under development since 2012 and starting 2015, they have been made generally available to all US troops via a public app store managed by the National Geospatial-Intelligence Agency.
But according to a Navy Inspector General report from March that was made public today, both apps contained vulnerabilities that could have allowed enemy forces access to troops' information.
The heavily redacted report doesn't detail the nature of the two vulnerabilities, but it does point out that the Navy had failed to control the distribution of these two applications, and later failed to act in warning troops of the danger they were in for almost a year.
The report says that the two apps, KILSWITCH and APASS, were never meant or approved to be deployed in live combat zones.
"Cybersecurity was not a concern for the [apps'] developers," the report said, because developers initially expected the apps to be used for troop training and military exercises primarily.
But the two apps, because of their flashy features and easier to use interface, became wildly popular among US troops, but also other military branches, including foreign allied forces.
The Navy Inspector General said the Navy failed to advise troops about the nature of these two apps. Auditors said the Navy and other military branches should have advised troops against using KILSWITCH and APASS in combat zones, where they should have used another app named ATAK (Android Tactical Assault Kit), which had been thoroughly tested and approved by the US Department of Defense for war zones.
The Navy Inspector General credits a whistleblower's persistent efforts for surfacing these two vulnerabilities. While the whistleblower's name is redacted, the report is about Anthony Kim.
Kim's case is somewhat notorious in military circles. According to a report from the Washington Free Beacon from earlier this year, Kim worked as a civilian program analyst for the Naval Air Warfare Center Weapons Division (NAWCWD), one of the two military divisions who co-developed and promoted the KILSWITCH app.
The Free Beacon, citing Kim's lawyer, says Kim discovered the KILSWITCH and APASS vulnerabilities last year, in March 2017, and notified his direct supervisors, only to be ignored.
When Kim continued to raise the issue about the two vulnerabilities with the civilian leadership of the military base where he worked --the Naval Air Weapons Station in China Lake, California-- he was told to "stop discussing DPSS in any disparaging way."
DPSS stands for Digital Precision Strike Suite, a private-owned military contractor that was involved in the creation of the two applications.
Kim's lawyer says the army's civilian leadership then reduced his client's pay as a warning for insisting on raising concerns about the two vulnerabilities.
However, Kim didn't give up, and he reported the vulnerabilities to Navy high officials via the Pentagon's whistleblower program. Kim's lawyer says that a month after the Navy Inspector General started an investigation into Kim's complaint the army base's management put him on leave, suspended his pay, and withdrew his security clearance.
Now, more than a year after Kim's complaint, investigators have sided with Kim in this dispute.
"Thanks to a brave whistleblower who spoke up, the Navy is now taking the cyber threat posed by these apps seriously and ensuring security measures are in place," said Special Counsel Henry J. Kerner of the US Office of Special Counsel.
"I strongly commend [REDACTED] for his public service in this matter," Kerner added, in a letter sent to the White House. "By filing this disclosure, he exposed a serious issue that potentially endangered the physical safety of forward-deployed military personnel."
"This software was widely distributed across [REDACTED], many of whom used it in combat. [REDACTED] should be lauded for his determination to protect the safety and wellbeing of military personnel who risk their lives to protect the United States," Kerner said.
But besides lauding Kim for his actions, the same White House letter is far more harsh towards NAWCWD officials, claiming they've intentionally misled DOD officials about the app's security, which led to "untested software" reaching combat front-lines.
Kim's comments, as cited in the White House letter, claimed the apps "were marketed and showcased to secure political and capital gains for NAWCWD, with little regard for the consequences of rolling out vulnerable software to units that would rely on it in combat."
Following the completion of the Navy Inspector General report in March, the Navy sent out an official warning to troops in June this year, advising military personnel to stop using the two apps in combat zones. DOD officials also reinstated Kim's security clearance and allowed him to return to work.
Cybercrime and malware, 2019 predictions
More cybersecurity news:
- Facebook bug exposed private photos of 6.8 million users
- US ballistic missile systems have very poor cyber-security
- SQLite bug impacts thousands of apps, including all Chromium-based browsers
- DOD doesn't keep track of duplicate or obsolete software
- Shamoon malware destroys data at Italian oil and gas company
- Thousands of Jenkins servers will let anonymous users become admins
- How to enable spam call filtering on your Android phone TechRepublic
- New antiphishing features come to Google G Suite CNET