Vast majority of cyber-attacks on cloud servers aim to mine cryptocurrency

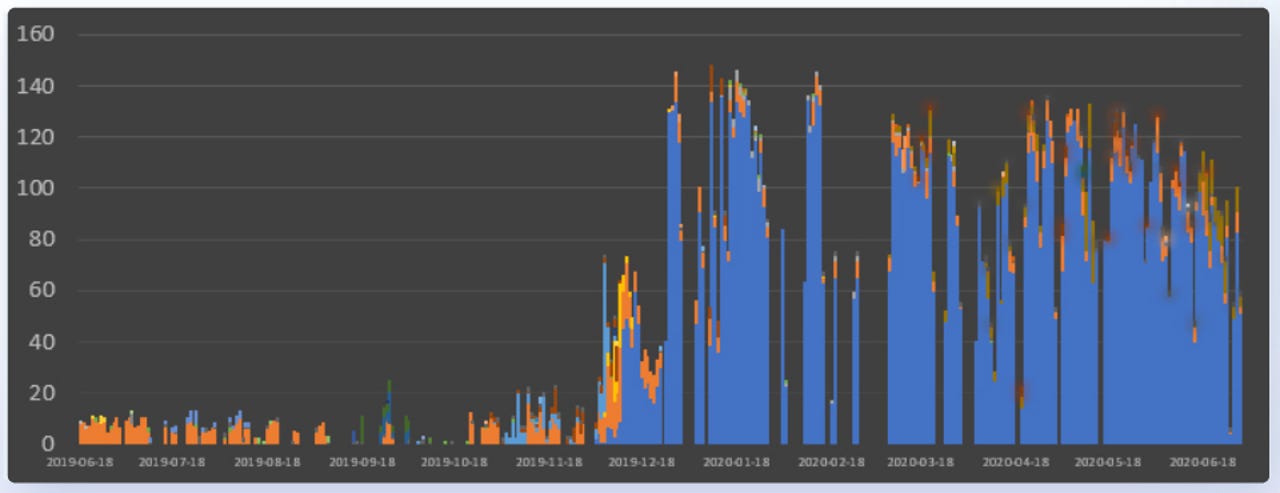
An analysis of one year's worth of cyber-attacks recorded in cloud honeypot servers reveals that the vast majority of hackers target cloud infrastructure with the purpose of deploying crypto-mining malware rather than exfiltrate sensitive corporate information, set up DDoS infrastructure, or other forms of cybercrime.
According to Aqua Security's 2020 Cloud Native Threat Report, which tracked and analyzed 16,371 attacks between June 2019 and July 2020, attacks against cloud systems exploded at the start of the year when the company recorded a 250% jump in attacks from the previous year.
During these attacks, hackers tried to gain control over the honeypot servers and then download and deploy a malicious container image.
Aqua said that 95% of these images were aimed towards mining cryptocurrency, while the rest were used for setting DDoS infrastructure, something that has not been a common occurrence until recently.
"Our analysis suggests that the threat landscape shifted towards organized cybercrime, which is investing in infrastructure," Aqua said.
The involvement of organized cybercrime groups not only led to a spike in attacks but also raised the complexity of these intrusions.
Intrusion methods diversified, and malware complexity improved, Aqua said.
From scanning the internet for cloud servers exposed online without a password, exploiting vulnerabilities in unpatched systems, and carrying out brute-force attacks, hacker groups have been recently orchestrating supply-chain attacks.
These are attacks where hackers plant malware in regular-looking container/server images that they upload to public registries.
Aqua Security says the malware stored inside these malicious containers springs into action and performs malicious actions only after the image is deployed, making it impossible to detect malicious payloads using static analysis or signature-based security systems.
This has led to multiple groups adopting supply-chain attacks as a method of targeting companies managing cloud infrastructure. [i.e., some of previous cases I, II, III, and IV]
Furthermore, the malware is also getting more complex, slowly inching closer to the complexity of malware seen targeting desktops. Aqua said it saw malware strains using multi-stage payloads, 64-bit encoding to hide their malicious code, and techniques to disable competing malware on the same system.
All of this suggests a maturing cybercrime scene that is primarily focused on generating revenue, and the easiest way to do that is by mining cryptocurrency (Monero) on the hacked servers.
For more details on attacks targeting cloud infrastructure, please refer to Aqua Security's 71-page 2020 Cloud Native Threat Report.