Vulcan Cyber study finds serious problems with vulnerability management

The majority of IT departments are underestimating the maturity of their vulnerability remediation programs by a wide margin, according to a study from Vulcan Cyber.
The company said it was surprised that most organizations think that they are much further along in their work in patching known vulnerabilities yet they have barely begun the work required.
"What caught us off guard was that the vast majority of respondents felt their programs were already mature," said Yaniv Bar-Dayan, co-founder and CEO of Vulcan. "Given the amount of breaches caused by known, unpatched vulnerabilities, we discovered a surprising disconnect that merits a closer look."
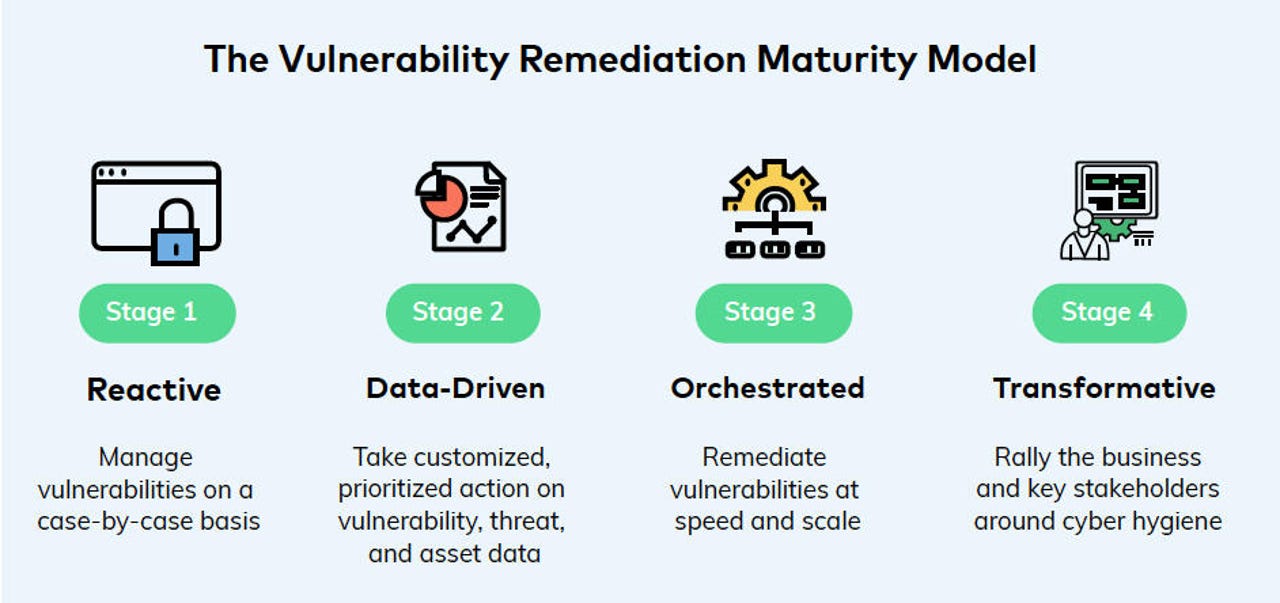
Most organizations are only at Stage 1 in Vulcan Cyber's maturity model
The study asked 100 computer security and IT executives about how they manage vulnerability remediation. It found that 84% reported having "mature" remediation programs. But on further questioning they were found to have only completed very basic tasks and were many stages away from a "mature" program.
Most had completed these basic activities: vulnerability scanning (72%); use of remediation tools (49%); and prioritization of vulnerabilities (44%).
But these tasks were less mature: collaborative remediation (48%); automated remediation (48%); and business alignment around cyber objectives (31%).
Vulnerability remediation can be a problem because there is often no one directly responsible for the program. For example, security teams will identify vulnerabilities and then turn it over to IT teams to complete the patch. Or, they share the work without anyone being clearly responsible for its completion. The work is further slowed by extensive testing that's required to make sure the remediation doesn't break any critical IT processes.
The study reflected this organizational problem with 89% of respondents saying that their security and IT teams spend considerable time working together with cross-functional teams; and for nearly half of them (42%) reporting that it is "a lot" of time; with 7% complaining that it is "too much" time.
Judging by the lack of progress in vulnerability remediation programs, the meetings and the lack of a clear process seem to be getting in the way of the work.
"Vulnerability scanning and prioritization are essential functions, but they are the bare minimum -- not what constitutes a mature program," Bar-Dayan said. " In our experience, program bottlenecks are further along in the remediation lifecycle, stemming from inefficient cross-team collaboration. Changing the status quo requires organizations to update and automate their remediation processes. It's a heavy undertaking."
Vulcan says that the reward for reorganizing how remediation is handled will be far stronger computer security for the enterprise. Most data breaches use known vulnerabilities that haven't been patched.
The Vulcan SaaS platform identifies and prioritizes vulnerability remediation. Additional results from the study can be found here: Vulcan Cyber whitepaper and infographic