WannaRen ransomware author contacts security firm to share decryption key

A major ransomware outbreak hit Chinese internet users earlier this year in April. For about a week, a ransomware strain known as WannaRen made tens of thousands of victims among both home consumers and local Chinese and Taiwanese companies.
Looking back, in retrospect, four months later, WannaRen's virality can be explained due to the fact that its code was loosely modeled after WannaCry, the ransomware strain at the heart of the May 2017 global outbreak.
Just like their inspiration, the authors of the WannaRen ransomware incorporated the EternalBlue exploit into their infection chain, allowing WannaRen to spread without restrictions inside corporate networks before encrypting and ransom files.
And just like WannaCry, WannaRen spread like wildfire, far beyond what the ransomware's authors had intended, creating more havoc than they anticipated, and the reason why, in the end, the malware's authors gave up the master decryption key for free, so all victims could eventually recover their files.
The Hidden Shadow malware group
More than three years after it happened, we can now say for sure that WannaCry was created by North Korean government hackers as a way to infect a few victims, ransom their files, and use the ransom payments to raise funds for the Pyongyang regime. WannaCry authors never had big ambitions, and causing a global outbreak was never their intent, as this only brought more attention to their illicit sanctions-evading and criminal activities.
However, something similar can also be said for the authors of the WannaRen ransomware, a group that Chinese antivirus maker Qihoo 360 said it's been tracking under the name of Hidden Shadow.
Described as a small-time threat actor, this group has been active for years, being involved in the distribution of an assortment of malware strains, usually via pirated software download sites.
Past operations involved the distribution of password-stealers, keyloggers, remote access trojans, and cryptocurrency-mining malware.
WannaRen was added to the group's arsenal and incorporated into their distribution routine on April 4, this year.
According to multiple sources, WannaRen's initial point of distribution was a modified installer for the Notepad++ text editor that was shared via the Xixi Software Center.
Because access to the official Notepad++ download site is often blocked in China due to the software maker's anti-Chinese stance, and because Xixi is one of China's largest software download sites, infections with WannaRen spike right away.
Thousands of Chinese internet users began asking for help decrypting their files on Chinese forums, social networks, and online chats, starting with the first day when WannaRen infections started getting detected, according to local press.
Hidden Shadow malware spread laterally across networks
While many users were home consumers, many asking for help were IT admins managing corporate networks, where WannaRen was particularly aggressive.
This was likely due to WannaRen's infection routine.
On computers where users installed this booby-trapped version of Notepad++, the installer dropped a backdoor trojan, deployed the EternalBlue exploit to spread laterally across a network (via SMBv1), and used a PowerShell script to download and install the WannaRen ransomware or a Monero-mining module.
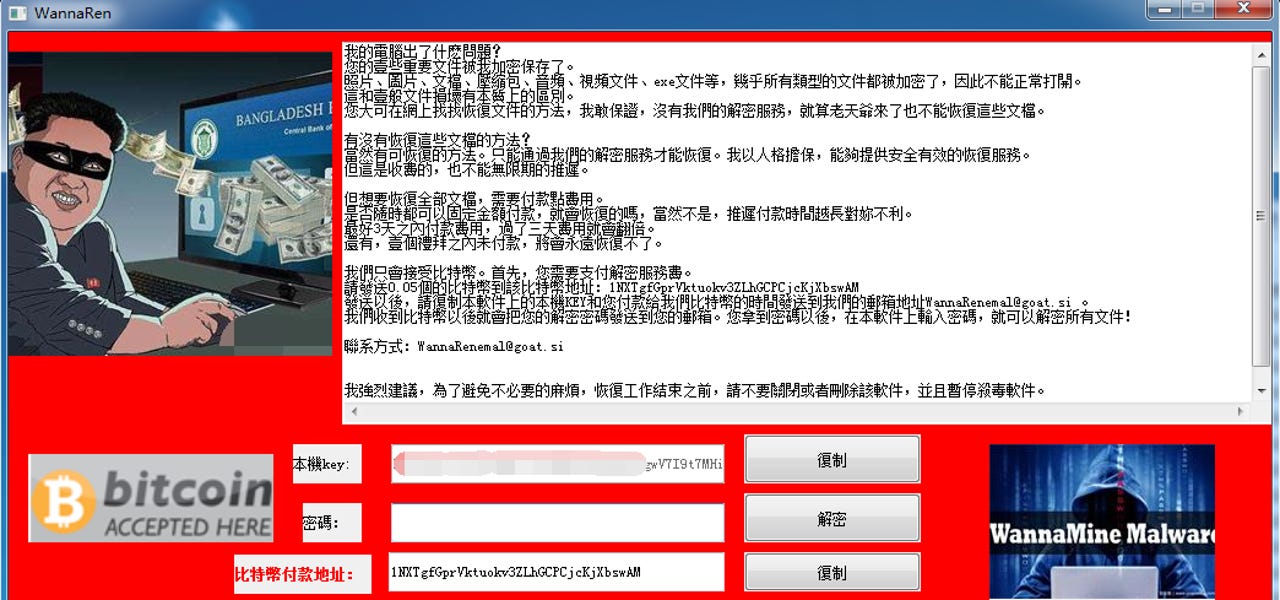
Once it locked users' computers, the ransomware would show a ransom note portraying North Korean dictator Kim Jong-un, and ask users to pay a decryption fee of 0.05 bitcoin (~$550) to decrypt their files.
All computers hit by this ransomware were pretty easy to spot, as all encrypted files had their names appended with the ".wannaren" extension.
WannaRen authors give out their own decryption key
From the pretty niche distribution method and the low ransom demand, it was pretty clear from the get-go that the Hidden Shadow group had not intended for their ransomware to spread so widely and so fast.
Likely fearing or anticipating a crackdown from Chinese authorities, less than a week after they started distributing WannaRen, the Hidden Shadow group reached out to a local Chinese cybersecurity firm named Huorong Security (火绒, or Tinder Security).
In a series of emails the company shared online, the WannaRen authors shared the ransomware's private encryption key (also known as a master decryption key) with Huorong's staff, asking the company to create and share a free decryption utility with infected victims.
On the same day, on April 9, Huorong released its WannaRen decryption utility, followed a few hours later by a similar decryption utility created by RedDrip, a cyber-security division inside QiAnXin Technology, which has also been tracking the ransomware's rapid spread across China.
However, while the vast majority of WannaRen users were in China, the ransomware's extreme virality also allowed it to spread via internal networks from Chinese subsidiaries to some foreign companies as well.
Since not all these companies might be aware that there is a free decryption tool available, or they might not trust the tools created by the two Chinese security vendors, today, Romanian antivirus maker Bitdefender also released its own WannaRen decryption utility.
At the time of writing, WannaRen infections appear to have died out, but victims who may have copies of files encrypted by this threat back in April can now decrypt them for free.