WordPress and Apache Struts account for 55% of all weaponized vulnerabilities

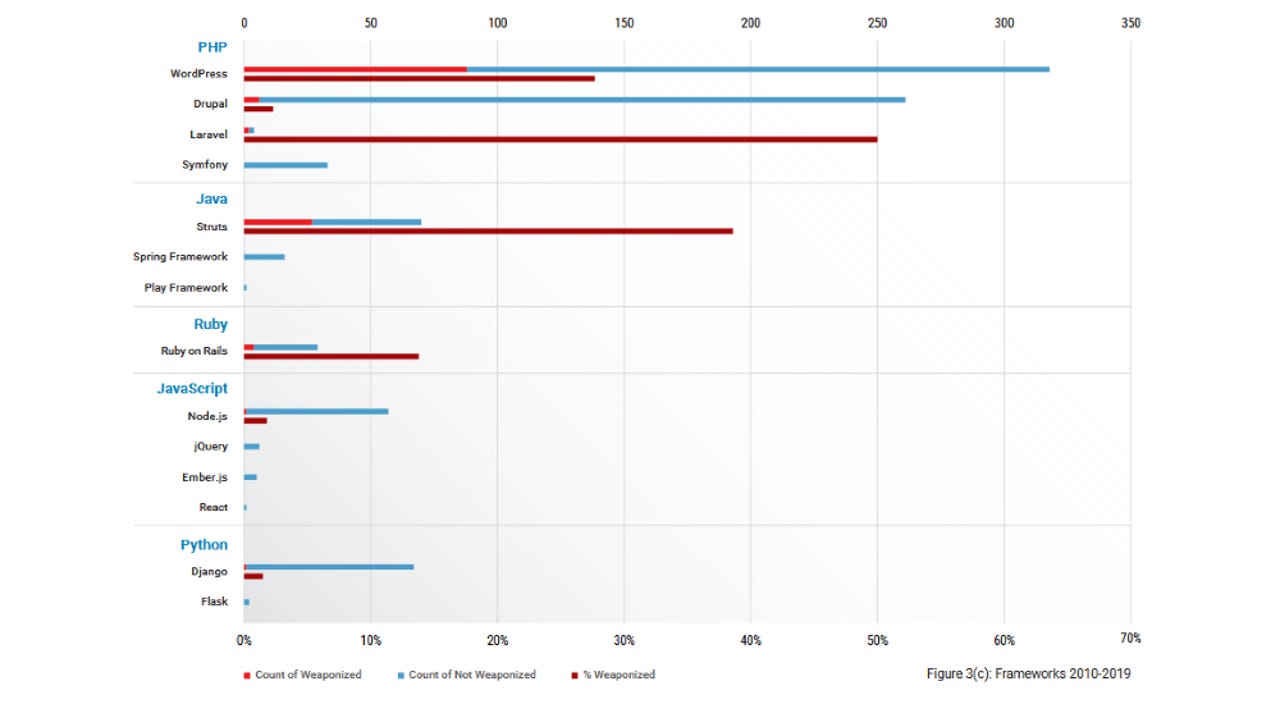
A study that analyzed all the vulnerability disclosures between 2010 and 2019 found that around 55% of all the security bugs that have been weaponized and exploited in the wild were for two major application frameworks, namely WordPress and Apache Struts.
The Drupal content management system ranked third, followed by Ruby on Rails and Laravel, according to a report published this week by risk analysis firm RiskSense.
In terms of programming languages, vulnerabilities in PHP and Java apps were the most weaponized bugs of the last decade.
Keep an eye on Node.js and Django
The least were bugs in JavaScript and Python, but RiskSense anticipates that this will change in the coming years as both languages have now become widely & wildly popular, and their adoption has now skyrocketed.
More specifically, users and security firms should keep an eye on Node.js and Django, the two most popular application frameworks for the JavaScript and Python ecosystems, respectively.
"Node.js had a notably higher number of vulnerabilities than other JavaScript frameworks with 56 vulnerabilities, although only one has been weaponized to date," RiskSense said.
"Likewise, Django had 66 vulnerabilities with only one weaponized.
"While weaponization remains low, the large number of vulnerabilities in these frameworks leaves them open for the potential for risk," RiskSense said, anticipating that hackers will turn their gaze to the new rising stars of the programming world and look into weaponizing older bugs in attempts to compromise today's JavaScript and Python applications.
And in tune with programming trends for the last decade, RiskSense also noted that Perl and Ruby, programming languages that were popular at the start of the 2010s, have now seen fewer and fewer weaponized exploits as the decade ended, and as programmers moved to JavaScript and Python.
Injection vulnerabilities are the most sought after
But RiskSense researchers didn't only look at what application bugs were getting weaponized. They also looked at the vulnerability types.
Per the research team, while cross-site scripting (XSS) bugs were the most common security bugs disclosed in the 2010s, they were not the most weaponized ones.
That title goes to "injection-based" vulnerabilities, which can be abused to allow hackers to inject and run their own commands in the context of the victim's app or OS.
"Vulnerabilities tied to SQL injection, code injections, and various command injections remained fairly rare, but had some of the highest weaponization rates, often over 50%," the RiskSense team said.
"In fact, the top 3 weaknesses by weaponization rate were Command Injection (60% weaponized), OS Command Injection (50% weaponized), and Code Injection (39% weaponized)," researchers added.
Readers interested in learning more about vulnerability weaponization trends for the last decade can find out more in RiskSense's 22-page report, titled "Cracks in the Foundation: Web and Application Framework Vulnerabilities."