$247,000 KillDisk ransomware demands a fortune, forgets to unlock files

The cost of ransomware reached close to $1 billion in 2016, and it's not hard to see why.
The malware family, which targets everything from Windows to Mac machines, executes procedures to encrypt files and disks before demanding a ransom payment in return for keys to decrypt and unlock compromised machines.
However, it is not only the general public which is being targeted with everything from hospitals to schools and businesses now in the firing line.
As the prospect of losing valuable content on computer systems or facing widespread disruption to business operations is often too much to bear, many will simply give up and give in, paying the fee and unfortunately contributing to the cybercriminal's operations.
However, paying up does not guarantee that victims will get their files back, no matter how low or high the payment demand.
This week, ESET researchers discovered that a Linux variant of KillDisk, linked to attacks against core infrastructure system in Ukraine in 2015, is now being used against fresh Ukrainian financial targets.
The ransomware demands a huge amount of money, but there is no underwritten protocol for decryption keys to be released once payment is made.
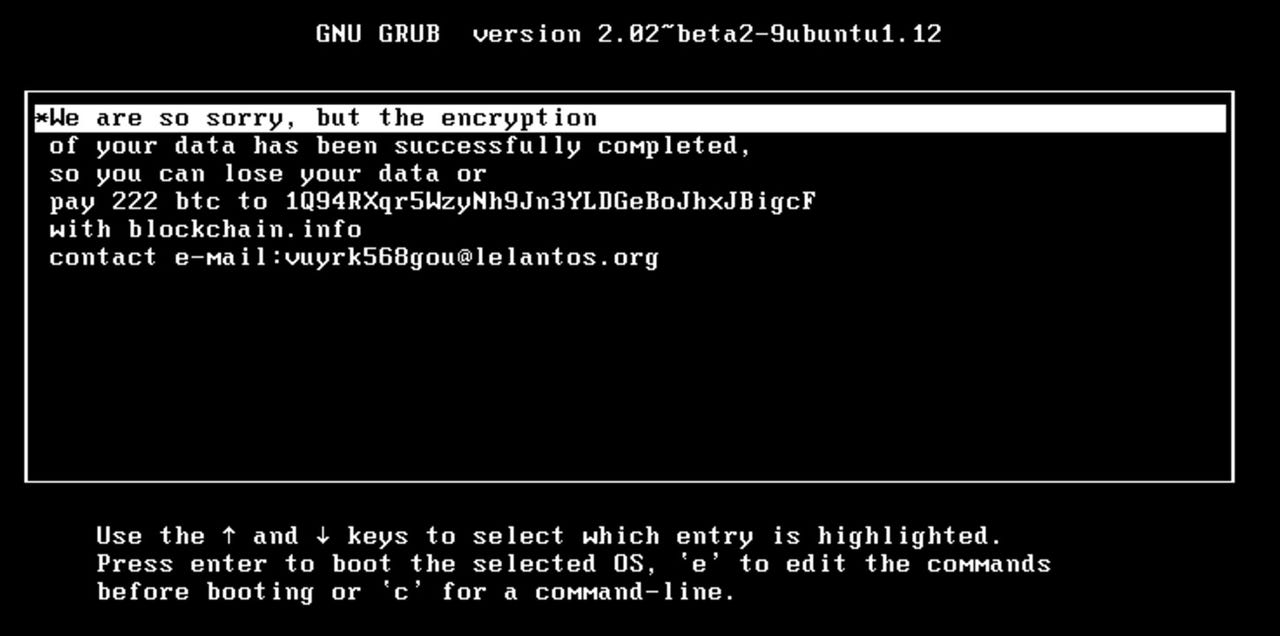
Distributed through phishing campaigns targeting both Windows and Linux, once downloaded, the ransomware throws up a holding page referring to the Mr. Robot television show while files are being encrypted, the research team said in a blog post.
A message then begins with "we are so sorry..." before demanding a laughable 222 Bitcoin ($247,000).
Unsurprisingly, no-one has paid up yet, nor should they, ever.
"This new variant renders Linux machines unbootable, after encrypting files and requesting a large ransom," ESET says. "But even if victims do reach deep into their pockets, the probability that the attackers will decrypt the files is small."
Files are encrypted using Triple-DES applied to 4096-byte file blocks and each file is encrypted using different sets of 64-bit encryption keys. However, the ransomware does not store encryption keys either locally or through a command-and-control (C&C) server, which means that affected systems after reboot are unbootable, and paying the ransom is pointless.
"It is important to note -- that paying the ransom demanded for the recovery of encrypted files is a waste of time and money," the team said. "Let us emphasize that -- the cyber criminals behind this KillDisk variant cannot supply their victims with the decryption keys to recover their files, despite those victims paying the extremely large sum demanded by this ransomware."
See also: Remove ransomware infections from your PC using these free tools | Hit by Globe3 ransomware? This free tool could help you decrypt your files
There is hope, however, for victims. There is a weakness in the encryption used by the ransomware, which makes recovery possible -- at least when it comes to Linux infections.
Earlier this week, researchers at Check Point revealed the latest exploits of the GoldenEye ransomware, a strain of malware which is targeting German HR companies. The malware is contained in phishing emails which appear to be from job applicants, and once downloaded and installed, demands $1000 in Bitcoin to unlock infected systems.