Cryptocurrency wallet caught sending user passphrases to Google's spellchecker

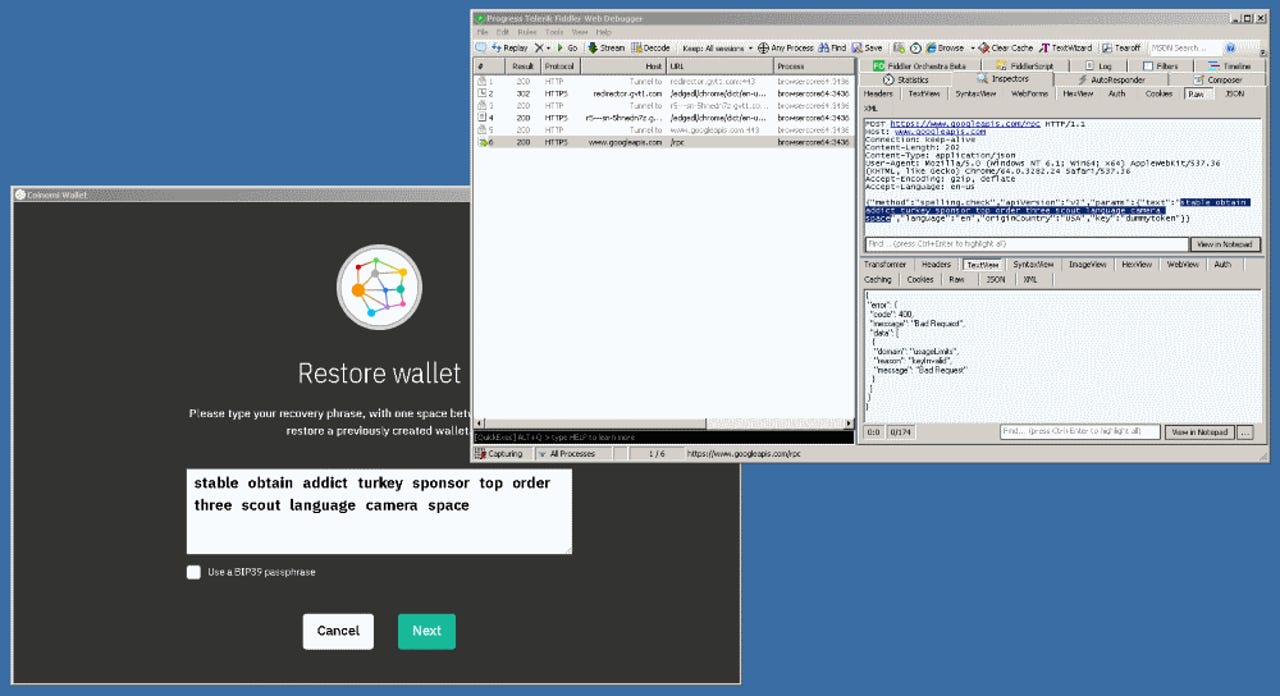
The Coinomi wallet app sends user wallet recovery passphrases to Google's spellchecking service in clear text, exposing users' accounts and their funds to man-in-the-middle (MitM) attacks during which attackers can log passphrases and later take over and empty accounts.
Security
The issue came to light yesterday after an angry write-up by Oman-based programmer Warith Al Maawali who discovered it while investigating the mysterious theft of 90 percent of his funds.
Al Maawali says that during the Coinomi wallet recovery process, when users enter their recovery passphrase, the Coinomi app grabs the user's input inside the passphrase textbox and silently sends it to Google's Spellcheck API service.
"To understand what's going on, I will explain it technically," Al Maawali said. "Coinomi core functionality is built using Java programming language. The user interface is designed using HTML/JavaScript and rendered using integrated Chromium (Google's open-source project) based browser."
Al Maawali says that just like any other Chromium-based app, it comes integrated with various Google-centered features, such as the automatic spellcheck feature for all user input text boxes.
The issue appears to be that the Coinomi team did not bother to disable this feature in their wallet's UI code, leading to a situation where all their users' passwords are leaking via HTTP during the setup process.
Anyone in a position to intercept web traffic from the wallet app would be able to see the Coinomi wallet app passphrase in cleartext.
This passphrase lets attackers gain access to a user's wallet (via the restore wallet function) and all the cryptocurrency accounts associated with that wallet --and implicitly all the users' funds.
While Al Maawali doesn't have definitive proof that this is how hackers stole his funds, he claims that only Coinomi-stored funds were stolen, so he sees no other way hackers might have gained access to those accounts besides gaining access to his Coinomi passphrase.
"Anyone who is involved in technology and crypto-currency knows that [...] 12 random English words separated by spaces will probably be a passphrase to a crypto-currency wallet," Al Maawali said.
The researcher created a dedicated website where he described the issue and the ordeal he went through trying to get Coinomi to acknowledge the vulnerability.
He also posted a proof-of-concept video that was later independently verified and reproduced by Luke Childs, a security researcher, and fellow cryptocurrency aficionado.
Some people don't seem to be able to see the video because the quote tweet is shown instead, here's the video: pic.twitter.com/x592HW9sEi
— Luke Childs (@lukechilds) February 27, 2019
Childs is no stranger to Coinomi issues. Back in 2016, he discovered that the Coinomi Android app was communicating with its backend servers via plaintext HTTP. Just like in Al Maawali's case, Coinomi refused to acknowledge the issue and later deleted Childs' bug report after a heated private exchange --detailed in depth on this page.
Coinomi, which offers a multi-cryptocurrency wallet app for Android, iOS, Linux, Mac, and Windows, did not respond to a request for comment.
Al Maawali claims he lost between $60,000 and $70,000 worth in different cryptocurrencies. There are also other reports on Coinomi's Reddit thread where users are complaining about waking up one day to find all their Coinomi-managed accounts emptied overnight [1, 2].
Update, March 5, 2017: Coinomi sent today a statement regarding the reported incident. The company said it patched the passphrase leak and also contested the researcher's findings that the data was being sent via HTTP. It also said that only its desktop apps were affected, not its mobile apps, and called out the researcher bug report as an extortion attempt.
Top tips for investing in cryptocurrency
Related cybersecurity news coverage:
- Hackers can hijack bare-metal cloud servers by corrupting their BMC firmware
- A third of all Chrome extensions request access to user data on any site
- Hacker steals $7.7 million in EOS cryptocurrency after blacklist snafu
- New browser attack lets hackers run bad code even after users leave a web page
- Researchers break digital signatures for most desktop PDF viewers
- It took hackers only three days to start exploiting latest Drupal bug
- Bitcoin plummets, along with interest in blockchain, cryptocurrency jobs TechRepublic
- Will the Samsung Galaxy S10 come cryptocurrency-ready? CNET