Crysis ransomware master keys released to the public

The world has been rocked by WannaCry causing disruption and upheaval across core services and businesses alike over the past week, but there is good news for victims of Crysis with the release of 200 master keys to the public.
Posted at the BleepingComputer forum, the keys can be used by victims of the ransomware as well as security firms in the creation of decryption tools.
The keys, uploaded to Pastebin, have been confirmed as valid by security researchers. Users of the keys have also confirmed that they have regained access to the files.
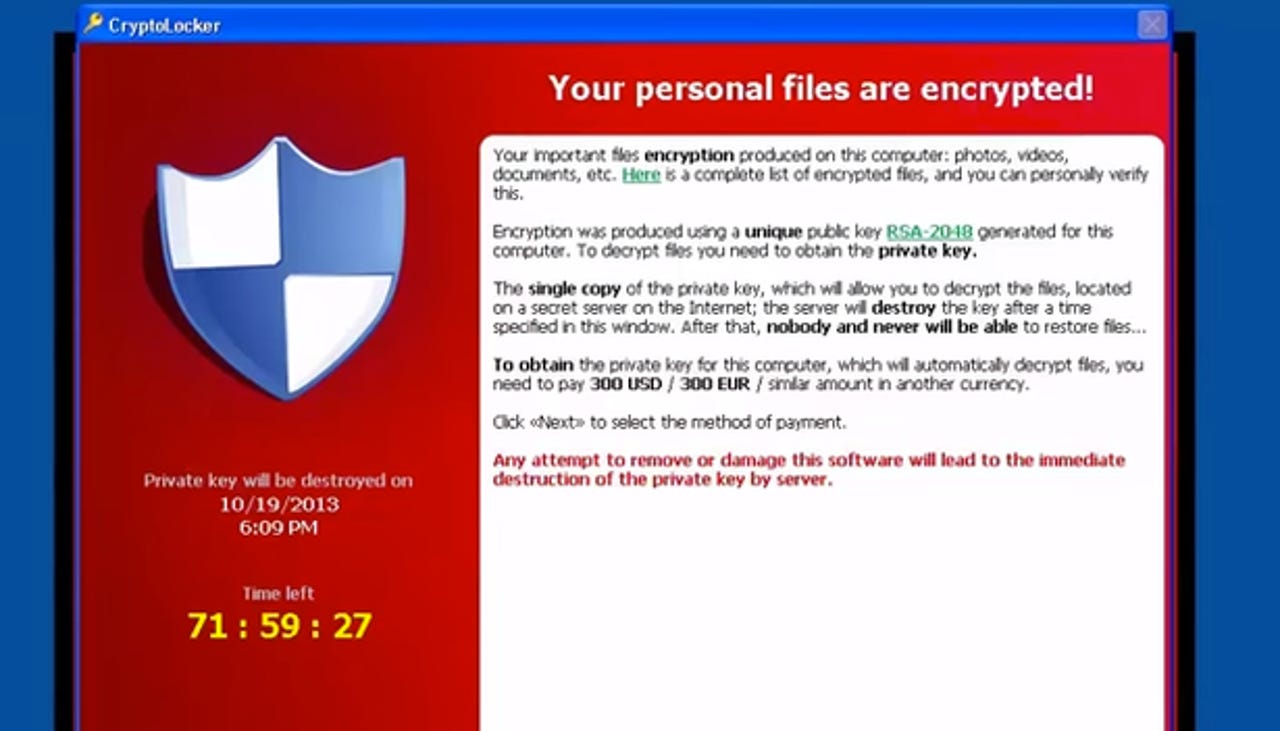
Ransomware is a particularly nasty form of malware which, once executed on a vulnerable PC, encrypts files and locks users out of their system.
Security
In return for a ransom demand in the virtual currency Bitcoin which can reach thousands of dollars, the victims are told that they will be granted a key to decrypt their files and restore access.
However, there is no guarantee that such keys will work, and to pay up only fuels this expanding criminal industry.
Recently, one strain of the malware dubbed WannaCry caused widespread disruption. The ransomware targets elderly Windows operating system builds -- Windows 10 has been protected with an automatic patch -- and enjoyed a successful campaign which is still causing damage and disruption to date.
The ransomware hit the headlines after taking down numerous UK National Health Service (NHS) hospital and trust systems, and since then, has spread worldwide.
In total, 386 samples of malware utilizing WannaCry have been detected in the wild, but if you have accepted automatic updates and keep your system up-to-date, there shouldn't be any need to worry about becoming infected.
See also: Queensland hospitals facing system failure after botched WannaCry patch
This is not the first time master keys for Crysis have been released; in fact, this is the third time. However, what sets this release apart is that the keys can also be used to decrypt files which have been encrypted with .wallet and .onion extensions.
"This has become a habit of the Crysis operators lately -- with this being the third time keys were released in this manner," ESET researchers say. "Since the last set of decryption keys was published, Crysis ransomware attacks have been detected by our systems over ten thousand times."
Why the keys have been released remains a mystery -- it may be that all who were likely to pay up have done so, and so there is no harm in releasing the keys, or perhaps after enjoying some time in the spotlight the campaign's operators are happy to get out of the game.
If you have been affected by this strain of ransomware, you can download a decryption tool provided by security firm ESET here.