Cybersecurity company warns of American Rescue Plan Act scams as first IRS child tax credit payments released

Cybercriminals are taking advantage of the latest round of IRS payments being sent out to families across the US by launching dozens of credential harvesting sites masquerading as American Rescue Plan Act signup sites, according to a new report from DomainTools.
Last week, the IRS began sending out the first round of child tax credit payments that were part of the larger American Rescue Plan Act passed earlier this year. The payments will be sent automatically by the IRS and require no sign-up.
But cybercriminals have created a maze of associated websites all aiming to trick people into entering their personal information by pretending to be associated with the child tax credit payments, DomainTools' Chad Anderson explained.
Anderson said that by analyzing historical WHOIS information and OSINT techniques, the cybersecurity company was able to tie this specific credential harvesting scam to GoldenWaves Innovations, a web development firm based in Nigeria.
That site was connected to "americaforgivenrelieffund[.]com" and both were registered and hosted through NameCheap. DomainTools was able to tie those two sites and 39 other domains to an email address: goldenwaves247@gmail[.]com.
A spokesperson from GoldenWaves Innovations denied the allegations and said their web hosting account was compromised.
"I have also received several notifications about this and I'm glad you're reaching us. I would be glad to provide you with any information you want to prove that we know absolutely nothing about this. Our web hosting account was compromised, I can show you proof of mail that was sent to our web hosting providers to take down all of these websites hosted by these criminals," the spokesperson said.
The spokesperson shared screenshots of their conversation with NameCheap customer service demanding the sites be taken down starting on June 29. In the chats, the spokesperson said that the NameCheap account initially belonged to himself and another colleague. The two separated and he believed their NameCheap sites would be separate but they were not, according to the screenshots.
The fake sites look exactly like government websites, explain the payments in detail and ask users to "apply now." One site, with the name "reliefcarefunds[.]com," asks for names, addresses, social security numbers, photos of drivers licenses and even your mother's maiden name.
Anderson said researchers found that many of the links associated with the email were also being sent out through Bitly link shortening links, which allowed the people behind the scam to name the link "Unemployment Insurance Relief During COVID-19 Outbreak | American Rescue Plan Act."
These links brought the researchers to other sites that were hosted on Garanntor and OVH, providing them with even more information about the creator and tying all of the sites to an email address registered in Ibadan, Nigeria.
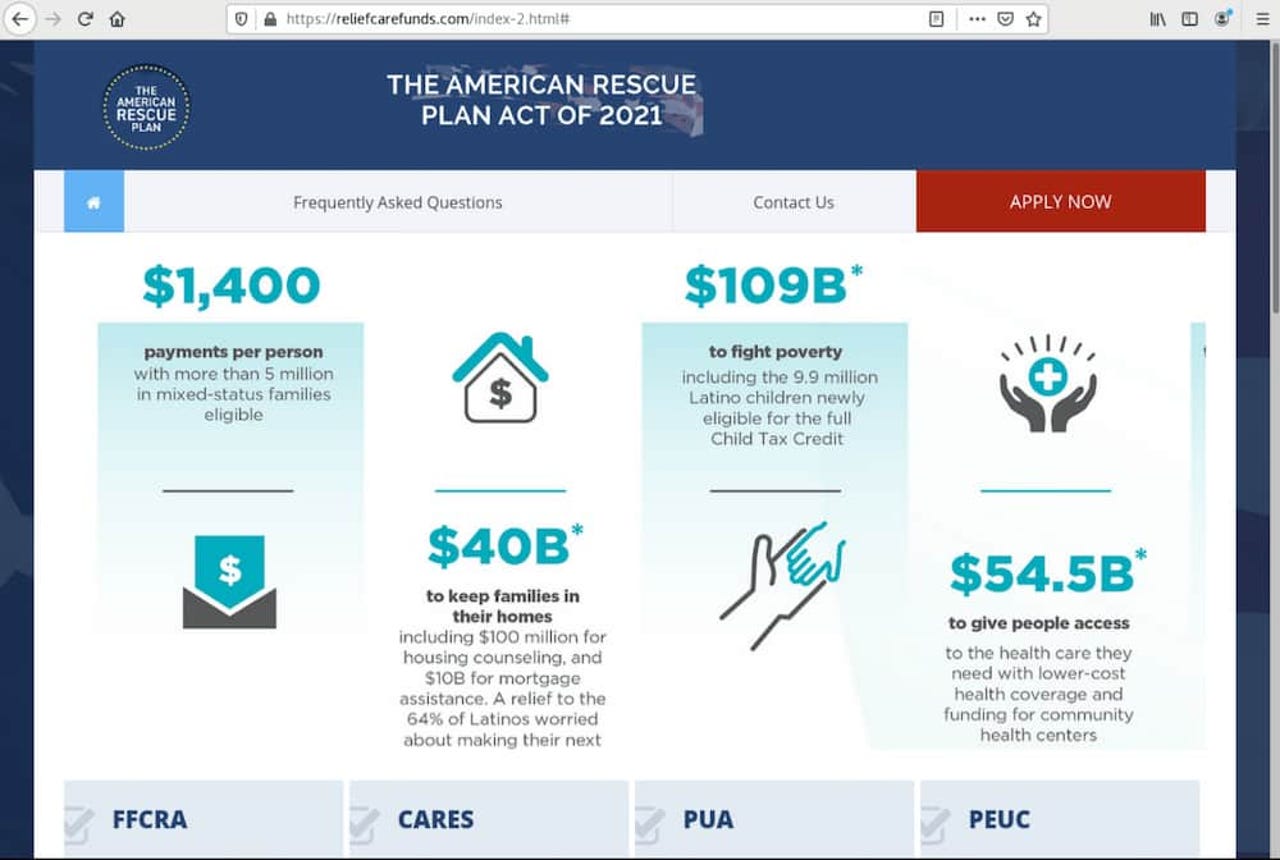
The credential harvesting sites are meant to look exactly like government websites.
"The city of Ibadan is a small, rural town which makes the registration information stand out as almost always technical contacts for Nigerian domains are located in Lagos, the capital city and technology center," Anderson wrote. "Additional searches reveal the same username participating in sales on cybercrime forums, Steam gaming, and other social media sites."
In the chat between NameCheap and GoldenWaves Innovations, the domain hosting site said it had deleted some of the websites related to the American Rescue Plan Act but then another NameCheap representative, Iryna Podolchak, said "since the domains are involved in illegal activity, we are unable to remove them from our side."
Podolchak said the issue was being forwarded to the Legal and Abuse department.
Anderson said that it is with "medium confidence" that DomainTools' researchers believe GoldenWaves Innovations -- which is also registered in Ibadan -- was a "legitimate web design firm in front of the identity document harvesting sites."
"Additionally, the historical WHOIS record unearths an address in New York, New York of 120 E 87th Street. This is an apartment building with condos ranging from $900,000 to $13,000,000 in the heart of Manhattan. While at first that seems strange for a company based in Nigeria, we can see from LinkedIn that one of the company's developers claims to live in New York City," Anderson said.
"Looking at the CEO's current contact information on LinkedIn we can see that GoldenWaves Innovations has a new website in goldenwaves[.]com[.]ng which is also tied to the same email address and registration information. This gives DomainTools researchers high confidence that all of these credential harvesting sites are linked to GoldenWaves Innovations in Nigeria. These sites along with any new ones that have cropped up were reported to Google Safe Browsing for blocking."
Anderson included a list of the domain names being used in the scam and told ZDNet that US law enforcement was informed about the sites.
When asked why a seemingly legitimate business would tie itself to credential harvesting sites, Anderson said "it's certainly sloppy" but added that this proved the usefulness of historical WHOIS data.
Other cybersecurity experts, like Digital Shadows cyber threat intelligence analyst Stefano De Blasi, said that along with extracting credentials, impersonating domains are frequently leveraged to extract financial information, deploy malware on a victim's machine, and distribute disinformation content.
"Additionally, users may be tricked into opening these malicious pages via spear-phishing emails or SMS, as well as being redirected there from other illegitimate websites. In both cases, if an attacker knows enough of social engineering techniques to pressure a victim into opening the URL and inserting their credentials," De Blasi told ZDNet.
"Social engineering attacks remain a predominant initial attack vector for threat actors, thus certifying that they keep working on many people despite its rather simplistic approach. Registering these domains is a trivial task for most attackers, thanks to prepared phishing kits and tutorials that attackers can easily find in cybercriminal forums. However, when registering hundreds of malicious domains, a careless attacker may well leave some crucial pieces of evidence behind that can then be gathered and analyzed by security researchers to assess attribution."