DreamBus botnet targets enterprise apps running on Linux servers

Chances are that if you deploy a Linux server online these days and you leave even the tiniest weakness exposed, a cybercrime group will ensnare it as part of its botnet.
ZDNET Recommends
The latest of these threats is named DreamBus.
Analyzed in a report published last week by security firm Zscaler, the company said this new threat is a variant of an older botnet named SystemdMiner, first seen in early 2019.
But current DreamBus versions have received several improvements compared to initial SystemdMiner sightings [1, 2, 3].
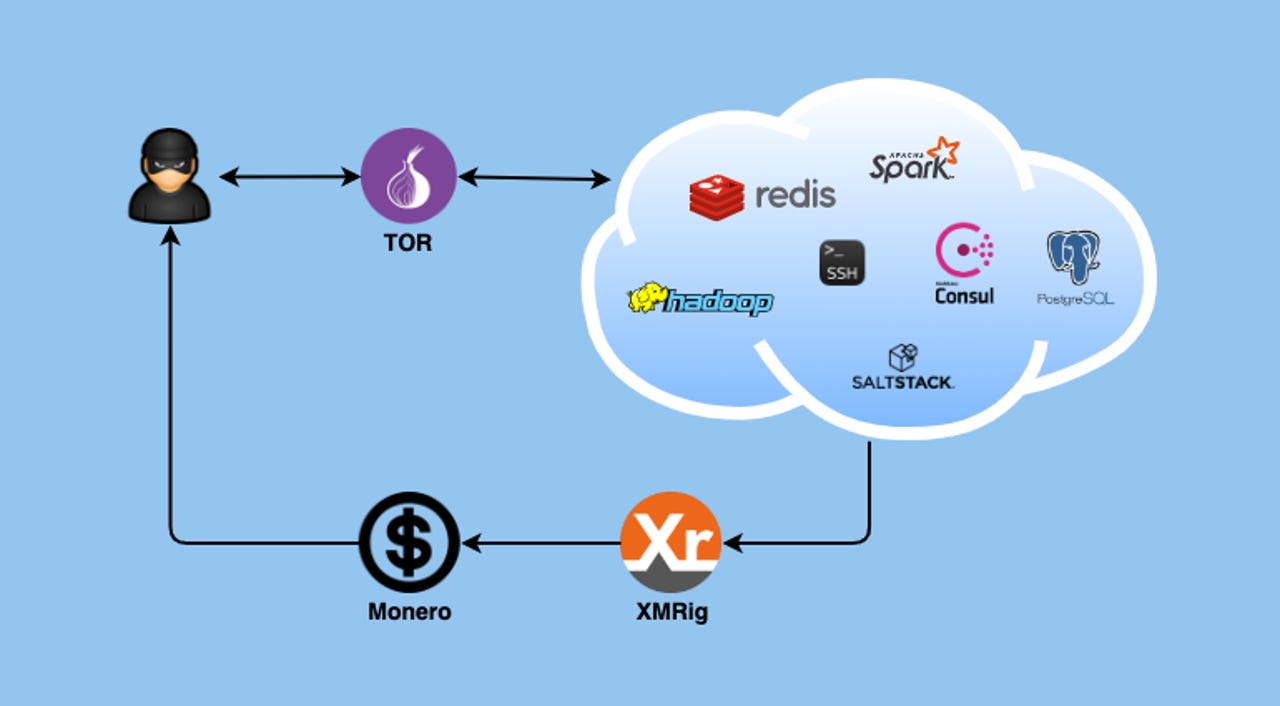
Currently, the botnet targets enterprise-level apps that run on Linux systems. Targets include a wide collection of apps, such as PostgreSQL, Redis, Hadoop YARN, Apache Spark, HashiCorp Consul, SaltStack, and the SSH service.
Some of these apps are targeted with brute-force attacks against their default administrator usernames, others with malicious commands sent to exposed API endpoints, or via exploits for older vulnerabilities.
The idea is to give the DreamBus gang a foothold on a Linux server where they could later download and install an open-source app that mines the Monero (XMR) cryptocurrency to generate profits for the attackers.
Furthermore, each of the infected servers is also used as a bot in the DreamBus operation to launch further brute-force attacks against other possible targets.
Zscaler also said that DreamBus employed quite a few measures to prevent easy detection. One of them was that all systems infected with the malware communicated with the botnet's command and control (C&C) server via the new DNS-over-HTTPS (DoH) protocol. DoH-capable malware is very rare, as it's complex to set up.
[1/2]
— Intezer (@IntezerLabs) August 3, 2020
🆕 Network admins beware, #SystemdMiner is now using DNS over HTTPs to connect to its .onion C2.
We uploaded IoCs to VT:
Modified UPX -> d5b98358d261730a9a81b480bd94cbc8
Unpacked -> 61d36807f333e9dd01737d74b2724ab9
->> pic.twitter.com/6wYrQ8a8dZ
Furthermore, to prevent the C&C server from being taken down, the DreamBus gang hosted it on the Tor network; via a .onion address.
But despite all these protective measures, Zscaler's Brett Stone-Gross believes we're seeing yet another botnet birthed and operated out of Russia, or Eastern Europe.
"Updates and new commands are issued that typically start around 6:00 a.m. UTC or 9:00 a.m. Moscow Standard Time (MSK) and end approximately at 3:00 p.m. UTC or 6:00 p.m. MSK," the researcher said.
But Stone-Gross also warned companies not to take this botnet lightly. Sure, the botnet delivers a cryptocurrency miner right now, but the Zscaler researcher believes operators could easily pivot to more dangerous payloads, such as ransomware, at any time they wanted.