Facebook's security measures used against it in fresh phishing campaign

Facebook's platform and security certificates are being used against it in phishing campaigns designed to dupe users into handing over their account credentials.
Cybercriminals are abusing the Facebook application platform to carry out phishing campaigns against users which appear legitimate thanks to the fraudulent use of Facebook's own Transport Layer Security (TLS) security certificates, a protocol used to help keep domains and user communication secure.
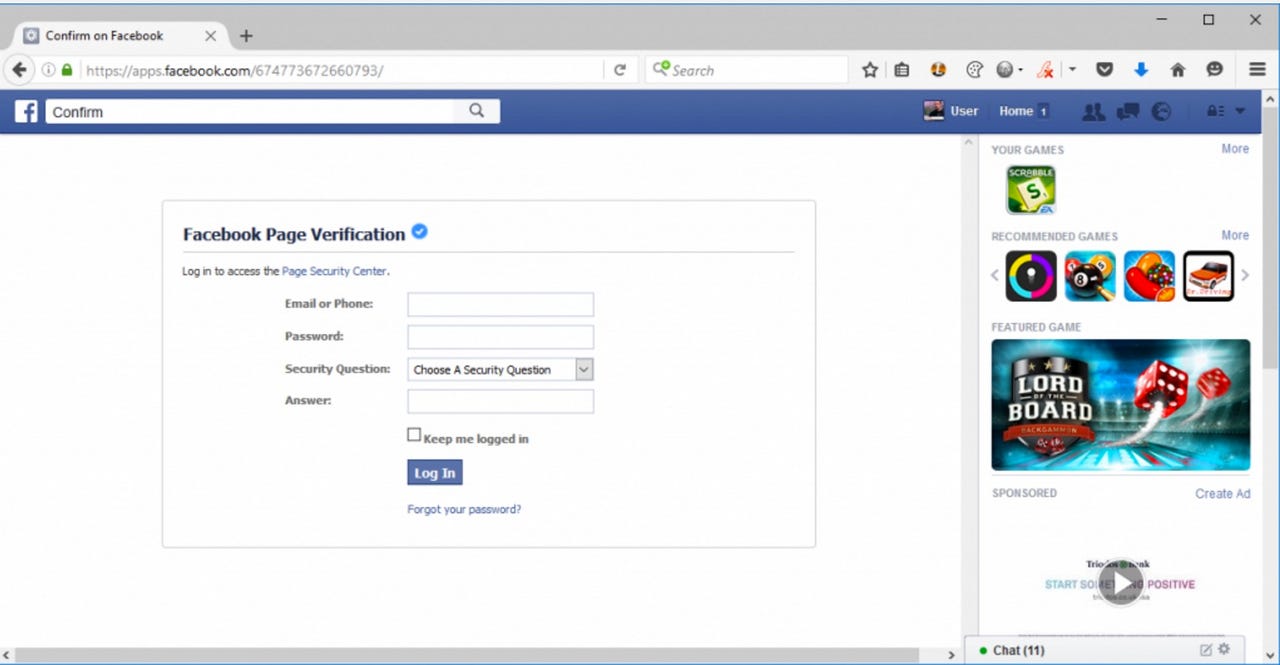
In a blog post, Netcraft security researchers said the phishing campaign masquerades as a Facebook Page Verification form, leveraging Facebook's TSL certification, which is used on all facebook.com subdomains.
Security
Phishing campaigns, usually stemming from fraudulent emails or malicious links, appear to be legitimate organizations ranging from social media giants to banks.
Potential victims are sent messages asking for credentials for a variety of reasons, and they may also be sent to a malicious domain controlled by a cybercriminal which harvests these credentials in order to compromise accounts.
In this example, the phishing attack's verification form is actually served through an iframe from an external HostGator site.
"The external website also uses HTTPS to serve the fraudulent content, so no warnings are displayed by the browser," the researchers say.
This removes the first warning alert. Unfortunately, the group goes a step further to appear legitimate by always pretending the first set of credentials input by a user were incorrect -- reducing suspicion and potentially increasing the chance of wary users trustingly using their true username and passwords.
Whether or not a Facebook user is logged in does not matter.
When submitted, the email form says the user will have to wait up to 24 hours for their submission to be approved. The user will wait, but the email never arrives.
In the meantime, the cyberattacker can either use these credentials or sell them on.
If you want to protect yourselves from these kinds of cyberattack, implementing Facebook's two-step verification process will stop your account from being immediately compromised and will give you a warning when someone is attempting to access your account.
It's not just worth using this security measure on Facebook, however -- as a code is sent to your phone for account access, it is well worth doing so on all across service you use which you consider valuable.
In related news, this week security researcher Orange Tsai discovered a backdoor into Facebook's corporate network while running penetration tests. At least one cybercriminal, if not more, had compromised the network and were logging in through stolen Facebook employee credentials.
Beach reads for tech junkies
Read on: Top picks