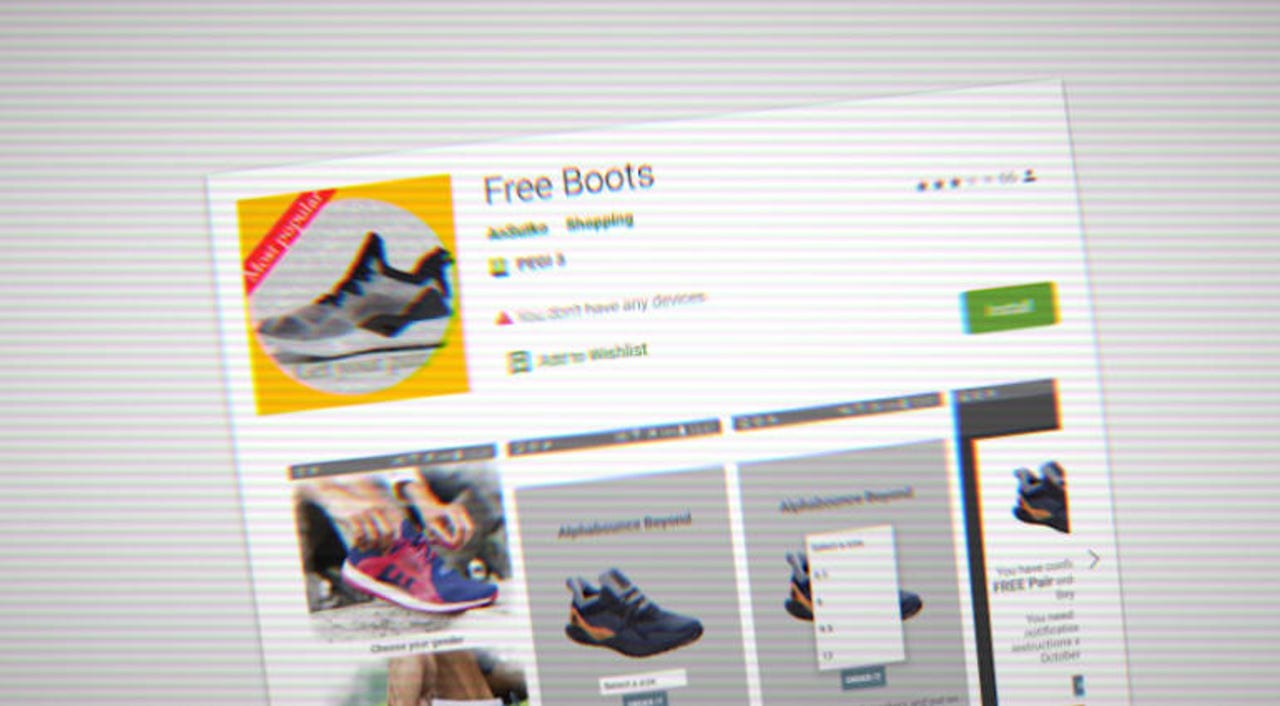
Google Play apps promised free shoes, but users got ad fraud malware instead

Google has removed 56 Android applications from the official Google Play Store that the company says were part of an ad fraud botnet.
Named Terracotta, this botnet was discovered by White Ops, a security firm specialized in identifying bot behavior.
White Ops researchers said they've been tracking Terracotta since late 2019 when the botnet seems to have become active.
Install a malicious app for a free product
Per the researchers, Terracotta operated by uploading apps on the Google Play Store that promised users free perks if they installed the applications on their devices.
The apps usually offered free shoes, sneakers, boots, and sometimes tickets, coupons, and expensive dental treatments. Users were told to install the app and then wait two weeks to receive the free products, during which time they had to leave the app installed on their smartphone.
However, the apps downloaded and ran a modified version of WebView, a slimmed-down version of Google Chrome. The Terracotta gang launched the modified WebView browser, hidden from the user's view, and performed ad fraud by loading ads and gaining revenue from fake ad impressions.
The White Ops team described Terracotta as both complex and massive. It was complex because it used advanced techniques to avoid detection from the defrauded ad networks, and was massive because of the scale at which it operated.
For example, White Ops said that in the final week of June alone, the Terracotta botnet silently loaded more than two billion ads inside 65,000 infected smartphones alone.
Some Terracotta apps have been removed from Google Play
Currently, after Google's intervention, the botnet's presence on the Play Store has been reduced, but not removed altogether, with some devices still appearing to be infected.
Bid request volumes as a result of Play Store enforcement
Some users might think that because the malicious Terracotta apps were defrauding ad networks and not the users directly, this botnet might not be a problem for them, but, on infected devices, the malicious apps would often wear out batteries and consume mobile bandwidth traffic due to the fact the malicious apps are running around the clock.
A list of Terracotta-infected apps is available in this PDF file.
These apps have been taken down from the Play Store and Google has disabled them on all users' devices, stopping their malicious behavior.
"Due to our collaboration with White Ops investigating the TERRACOTTA ad fraud operation, their critical findings helped us connect the case to a previously-found set of mobile apps and to identify additional bad apps. This allowed us to move quickly to protect users, advertisers, and the broader ecosystem – when we determine policy violations, we take action," a Google spokesperson said.
For security researchers, Android app developers, and software engineers, White Ops has published an in-depth technical report detailing Terracotta's inner-workings.