International click-fraud bot strikes close to a million victims worldwide

A botnet which has infected systems around the world counts almost one million victim PCs within its network, researchers say.
Botnets are networks of PCs which have been infected with malicious software designed to take control of the system without the owner's knowledge. This can lead to 'slave' PCs being forced to send spam or launch distributed denial-of-service (DDoS) attacks against web domains, but controllers may also redirect slave PC users to malicious domains.
Another feature of botnets is altering PCs to change where traffic goes in the quest for ad clicks. If the operator tampers with internet configuration settings, they can forward searches to third-parties which manipulate search engine results to push users towards pages injected with ads that generate money for the cybercriminals.
One botnet which has been in operation since 2014 has managed to spread across country borders and is now potentially earning vast amounts of fraudulent revenue for the group, having infected at least 900,000 PCs worldwide.
In a blog post, researchers from Bitdefender said the botnet is based on the Redirector.Paco Trojan, which often finds its way onto systems as bundled software with installers for popular applications such as WinRAR or the YouTube Downloader.
The malware is added to legitimate installers through specialized tools.
If an unwitting victim uses the installer, they are infected and their PC now belongs to the network.
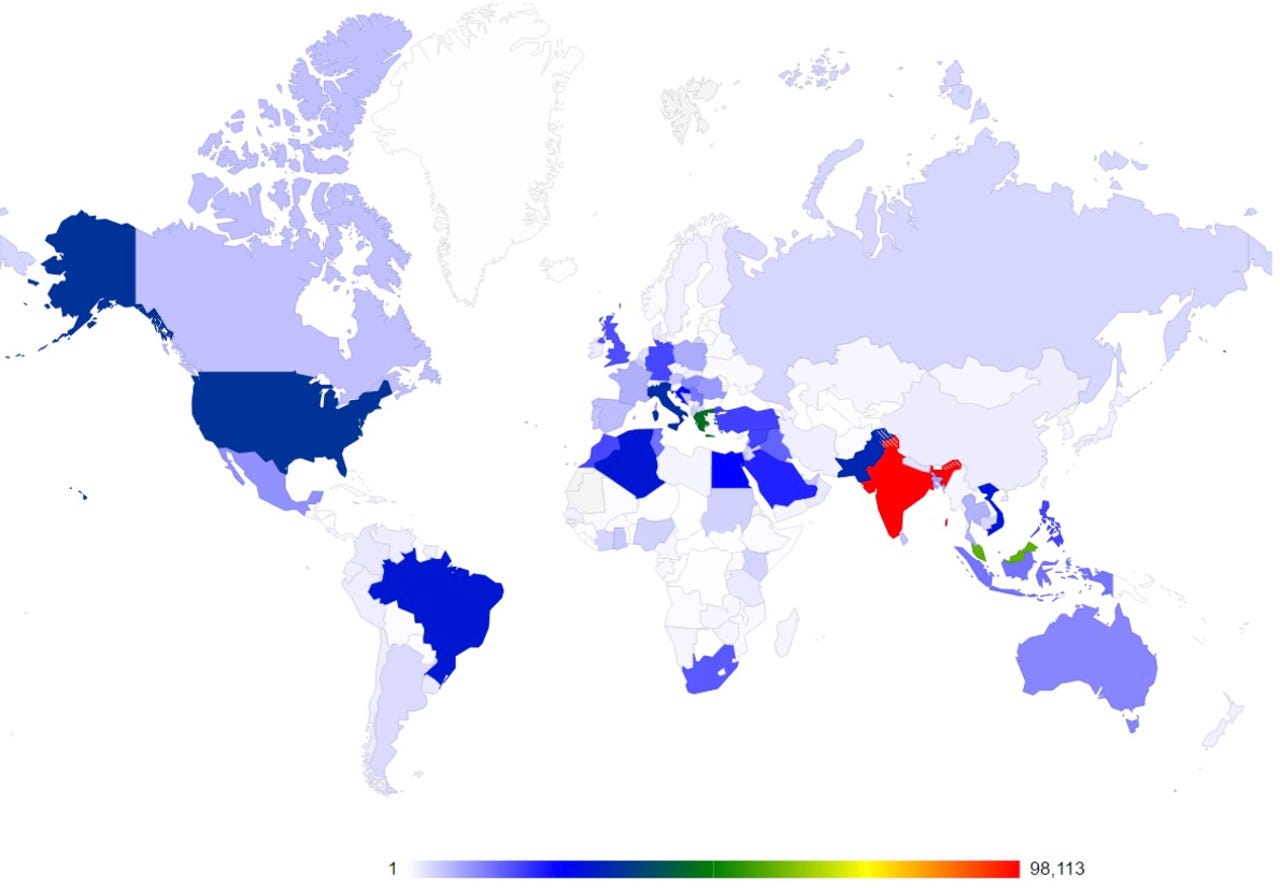
Bitdefender says that victims are mainly from India, Malaysia, Greece, the US, Italy, Pakistan, Brazil and Algeria.
It takes no more than a few simple tweaks in the registry to push traffic to ads which generate fraudulent revenue to operators.
Security
While the diverted search results are made to look authentic, there are some markers which can indicate your system is infected -- such as messages including "Waiting for proxy tunnel" or "Downloading proxy script" in the status bar of your browser.
In addition, search engines will likely take longer than usual to load and in Google's case, the typical yellow "O" above page numbers are not displayed.
In one example, the team found that the installers would drop JavaScript files which downloaded and implemented a proxy auto-configuration (PAC) file, ensuring traffic was routed through a server controlled by the operator.
To circumvent security checks, a free root certificate -- DO_NOT_TRUST_FiddlerRoot -- is used to avoid users realizing their PCs have been compromised.
Ad clicks and fraudulent traffic misdirection remain big business for cyberattackers and not only generate illegal revenue but also place your personal privacy and security at risk. In order to avoid these threats, you should keep your system patched, up-to-date and watch out for warning signs that something isn't right with your PC.
10 things you didn't know about the Dark Web
Read on: Top picks