Microsoft, law enforcement disrupt sprawling Dorkbot botnet

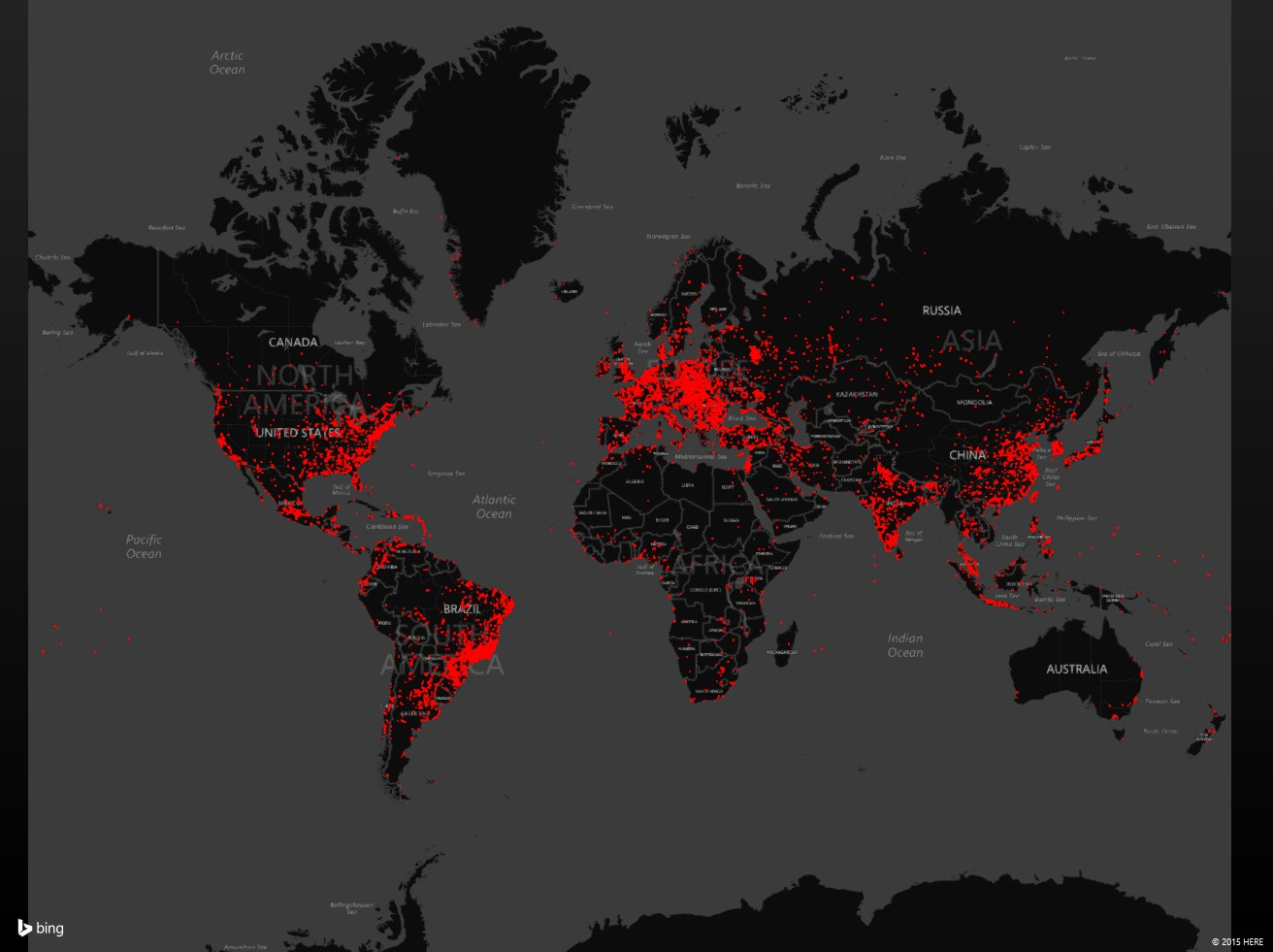
Dorkbot machine detections heat map for past three months
Thursday Microsoft claimed a cryptic victory over Win32/Dorkbot botnet malware, but didn't divulge much about how, simply saying it has assisted law enforcement to "disrupt" Dorkbot botnets. On December 3, US CERT released a Technical Alert about denting Dorkbot, as a collaboration between The United States Department of Homeland Security (DHS), the Federal Bureau of Investigation (FBI) and Microsoft.
Security
This Dorkbot isn't to be confused with same-named tech-focused global organization of artists, hackers, engineers, designers, scientists, and inventors that self-organize to present informal lectures and presentations. That's the good Dorkbot.
The evil Dorkbot infects over 100,000 each month, and has owned more than one million PCs in over 190 countries; it participates in DDoS attacks, and delivering other types of malware. The primary sites Microsoft lists it has seen Dorkbot target stealing user logins and passwords for are AOL, eBay, Facebook, Gmail, Godaddy, OfficeBanking, Mediafire, Netflix, PayPal, Steam, Twitter, Yahoo, and YouTube. LogMeIn, Brazzers, and YouPorn are also on its target list.
Dorkbot can also be commanded by whoever is running it to steal Internet Explorer and Firefox cached login details -- so be glad if you never let your browser "remember" usernames and passwords.
"Once connected to the C&C server," Microsoft wrote, "Dorkbot may be instructed to block certain security websites by blocking access to them. It does this through the hooked DnsQuery API in the IRC module."
There are 39 antimalware and security companies targeted to be blocked by Dorkbot, including Avast, Bitdefender, F-Secure, Kaspersky, Malwarebytes, McAfee, Norton, Sophos, Trend Micro, and VirusTotal.
Fortunately, Microsoft security software detects and removes Dorkbot. But it's the ginormous pseudo-cartel of Dorkbot globally that persists.
Old tricks to pwn new computers
Microsoft explains, "Dorkbot is an Internet Relay Chat (IRC) based botnet. It is commercialized by its creator as a "crime kit" called NgrBot, which hackers can buy though underground online forums. The kit includes the bot-builder kits as well as documentation on how to create a Dorkbot botnet."
You'd think a crime kit would have a better name. Its delivery begins with a drive-by download (such as through infected advertising), and the other usual ways consumers are compromised, such as spam emails and tainted links shared on social media sites. It literally worms its way in by exploiting unpatched software to infect the user's computer. "In its first communication, the worm sends the C&C server its geolocation, the version of Windows running on the computer, and a unique computer identifier." At this point, Dorkbot is ready to begin executing commands sent by the botnet operator, like downloading more malware and spreading to other computers.
Dorkbot then spreads itself from there in a variety of ways, including USB sticks and removable drives. US CERT warns, "Dorkbot tries to use the Windows Autorun function to propagate via removable drives (e.g., USB flash drive). You can disable Autorun to stop the threat from spreading."
Microsoft explains that Dorkbot is sold online, and that there are many operators currently utilizing Dorkbot.
In the most active campaign, Dorkbot was distributed within a loader module. This loader has its own code for updating itself and distributing other malware. It is also responsible for guiding Dorkbot's connection to another command-and-control (C&C) server. The operator appears to be abusing the older IRC-based Dorkbot variant by disabling the self-check routine, changing IRC commands, and using the loader to force it to connect to the operator's own C&C server.
If you're infected by Dorkbot, then you're very likely infected with other malware. Microsoft explains, "the Dorkbot worm can receive commands to download and install additional malware on the infected computer, causing users whose computers are infected with Dorkbot to be infected with other types of malware as well." Microsoft lists 14 malware families that it has seen downloaded by Dorkbot worms.
Like many attacks, Dorkbot erases its files. But Microsoft analysis found some files that may appear, which can indicate the presence of Dorkbot. Filenames include, facebook-profile-pic--JPEG.exe, %APPDATA%\windowsupdate\live.exe or %TEMP%\Adobe\Reader_sl.exe, -- see this page for the full list.
Dorkbot may also, at some point, pop up the following message:
To prevent or detect a Dorkbot infection, Microsoft advises:
Be cautious when opening emails or social media messages from unknown users. Be wary about downloading software from websites other than the program developers. Run antimalware software regularly. Our real-time security software, such as Windows Defender for Windows 10 for Windows 10 with up-to-date AV definitions will to ensure you have the latest protection against Dorkbot threats. Alternatively, standalone tools such as Microsoft Safety Scanner, and the Malicious Software Removal Tool (MSRT), can also detect and remove Dorkbot.
Microsoft is also continuing the collaborative effort to help clean Dorkbot-infected computers by providing a one-time package with samples (through the Microsoft Virus Initiative) to help organizations in protecting their customers.
Security fact or fiction? How to 'sanity check' cybercime news