Operation Ghoul targets Middle East engineers, industrial players

Researchers have uncovered a wave of attacks against industrial and engineering companies in the quest for cash.
According to Kaspersky, sensitive corporate financial data is the top target of the threat actors behind the campaign "Operation Ghoul," which operates primarily in the Middle East but is known to attack companies worldwide.
The researcher's report, published on Wednesday, says that cyberattackers are using spear phishing as the main technique to infiltrate company servers.
A carefully crafted email lands in a target's inbox which appears to be from banks in the Middle East. If a victim opens the file, they may be lured to click on a malicious link, or in other cases, the email will come with a malicious .7z archive file attachment.
In the majority of cases, CEOs, COOs, managers, supervisors, and engineers receive the email lures.
When malicious attachments are in play, Kaspersky says that the fraudulent emails claim to be "payment instructions." Instead, malware, based on the Hawkeye commercial spyware, executes in order to spy on the user and collect data including passwords, keystrokes, and screenshots.
Kaspersky says the malware also targets clipboard data, FileZilla FTP credentials, browser account data, messaging clients, and email services, as well as license information for some applications.
This information is then sent to the attackers in order to compromise other accounts and steal valuable financial data. In addition, the malware uses "anti-debugging and timeout techniques" to remain on a compromised system.
In total, over 130 companies have been targeted. Kasperksy says:
"The attackers' motivations are apparently financial, whether through the victims' banking accounts or through selling their intellectual property to interested parties, most infiltrated victim organizations are considered SMBs, the utilization of commercial off-the-shelf malware makes the attribution of the attacks more difficult."
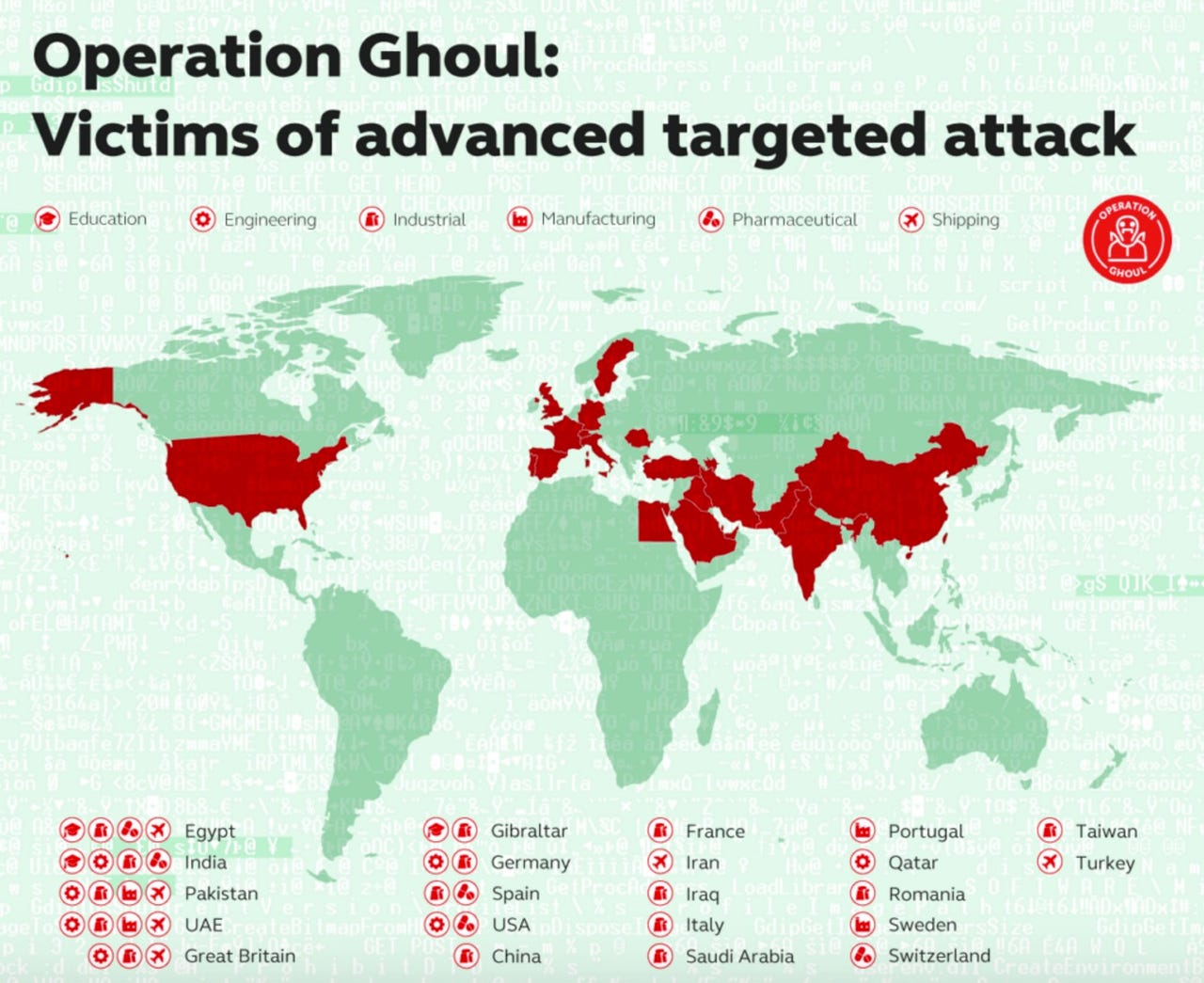
Targets of interest to Operation Ghoul range from petrochemical companies to technology providers, freight shippers to solar energy firms. The main focus appears to be on the industrial and engineering side, with construction, architecture, automaton, transport, and aerospace among the most constantly-attacked sectors.
Kaspersky Labs says that while some companies became victims in 2015, the latest wave of attacks began in June this year and are focusing more on some countries than others.
In total, 70 percent of targets were discovered in the United Arab Emirates alone, and the remainder were found across Russia, Malaysia, India, Jordan, Lebanon, Turkey, Algeria, Germany, Iran, Egypt, Japan, Switzerland, Bahrain, and Tunisia. A handful of other countries has also made the list, including the US, Italy, China, and Switzerland.
The malware strains used in this campaign are recognized as Trojan.MSIL.ShopBot.ww, Trojan.Win32.Fsysna.dfah and Trojan.Win32.Generic.
"Operation Ghoul is one of the many attacks in the wild targeting industrial, manufacturing and engineering organizations," the researchers say. "Kaspersky Lab recommends users to be extra cautious while checking and opening emails and attachments. In addition, privileged users need to be well trained and ready to deal with cyber threats; failure in this is, in most cases, the cause behind private or corporate data leakage, reputation and financial loss."