Ransomware abusing encrypted chat app Telegram protocol cracked

Ransomware which abuses the Telegram app API has been stopped in its tracks only weeks after discovery.
The malware, TeleCrypt, is typical ransomware in the way that the malicious code operates. If Russian-speaking victims accidentally run and execute the software -- potentially through malicious downloads or phishing attacks -- TeleCrypt will encrypt a system and throw up a warning page blackmailing the user into paying a 'ransom' to retrieve their files.
In this case, victims are faced with a demand for 5,000 rubles ($77) for the "Young Programmers Fund."
However, the malware also has unusual aspects, such as the use and abuse of Telegram Messenger's communication protocol to send decryption keys to the threat actor, which, according to Secure List, appears to be the "first cryptor to use the Telegram protocol in an encryption malware case."
While cryptors either maintain offline encryption or don't, this Trojan chooses to. In order to keep communication lines between the threat actor and ransomware concealed and protected, secure channels need to be created -- and this often increases the cost of malware development.
To circumvent these costs, TeleCrypt abuses the publicly available Telegram Bot API by operating as a bot which generates unique tokens that are inserted into the malware's body so the Trojan can use the Telegram API.
By utilizing this channel rather than maintaining communication between the operator's command and control center (C&C) over simple HTTP-based protocols, commonly used by many ransomware variants, security is improved and tracing the operator is more difficult.
"TeleCrypt uses the TeleGram API to send the information on its victims to the ransomware creator and to send information back," Malwarebytes researcher Nathan Scott says. "This way of communication is very unique -- it is one of the first to use a mainstream messaging client's API, instead of a C&C server, to send commands and get information."
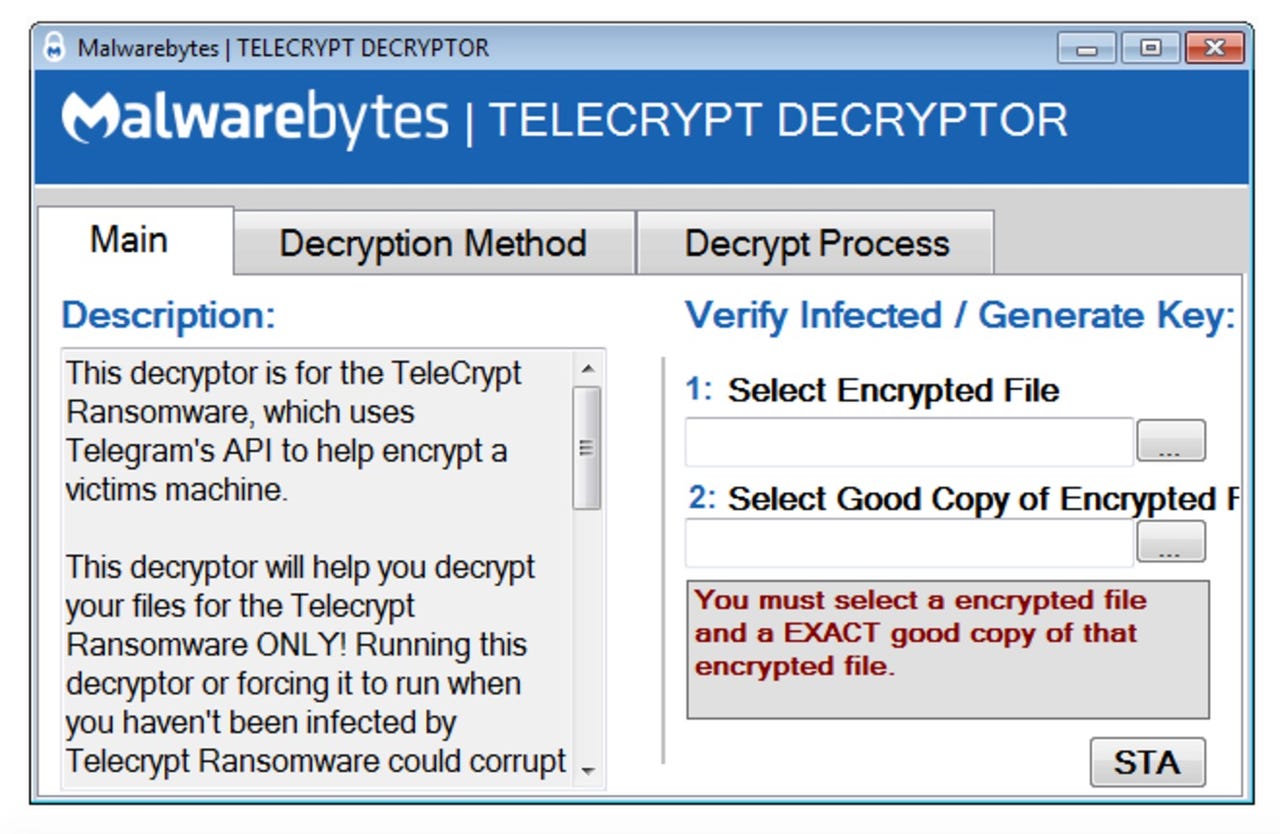
However, the ransomware also contains a major flaw. TeleCrypt encrypts files by looping through them a single byte at a time, and then simply adding a byte from the key in order, as noted by Scott, and as such, this simple encryption method made the task of creating a decryption application easier for researchers.
The security specialist has been able to rapidly develop a decryption tool which allows victims to recover their files without paying up. However, you need an unencrypted version of a locked file to act as a sample to generate a working decryption key .