Raum turns the most popular torrents on the web into malware spreading weapons

Security researchers from InfoArmor have revealed the use of Raum in active campaigns to spread malware through torrents.
On Tuesday, InfoArmor released a detailed analysis of Raum, most often found packaged with the most popular torrent files on the Internet.
While torrent packages themselves are not illegal -- as the technology behind them, BitTorrent, is simply a protocol used to increase the download speed of large files between systems -- the most popular and active torrents are usually uploaded to share copyrighted material.
Found through websites including The Pirate Bay, ExtraTorrent and TorrentHound, these torrents allow users to share movies, television shows, games and music, among other content.
When torrents and P2P networking first began to emerge online, you could often tell if torrents were fake or malicious files based on file sizes and peer reviews. However, with the evolution of both torrents and cyberthreats, ways to distribute malware have become more sophisticated.
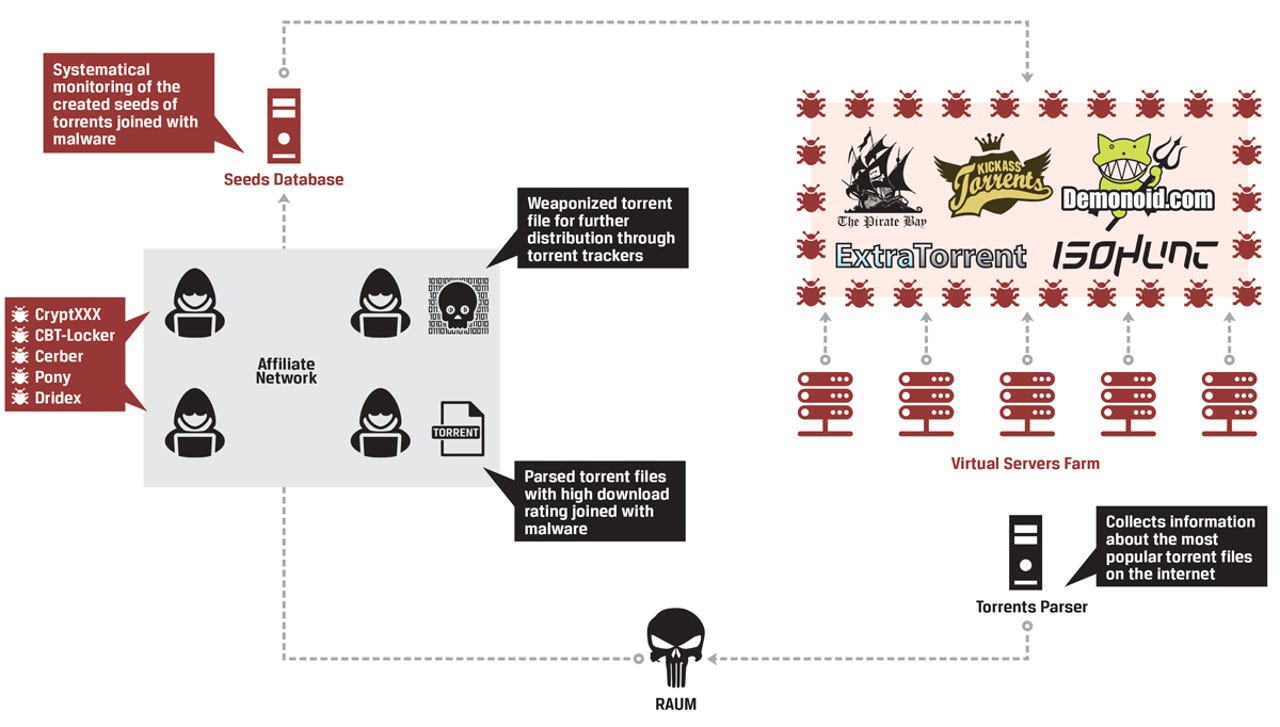
According to InfoArmor, Raum is used to "weaponize" these torrents by inserting malware into the packages through both the uTorrent client and a "special infrastructure" which allows the threat actors to manage new seeds for torrents using a network of dedicated and virtual servers, alongside compromised devices.
The cybercriminals behind the scheme use data analytics to identify trends on video, audio, software and other downloads which are popular through torrents. Once the group has identified the most popular -- and therefore most likely to distribute malicious code -- Raum is used to create malicious "seeds" -- the systems hosting the full file for download -- while "leechers" seek the file for download, execute, and potentially become compromised.
The researchers say that in some cases, the threat actors were going after specific user accounts in the community in order to use them to seed new malicious files without their knowledge.
Considering how important trust is in the torrent community, if major uploaders were compromised, malware distribution could be increased exponentially.
"In some cases, the lifespan of these seeded malicious files exceeded 1.5 months and resulted in thousands of successful downloads," InfoArmor says.
The most popular targets are PC-based online games and activation files for operating systems including Microsoft Windows and Apple Mac OS.
See also: Blizzard hit with DDoS attack disrupting play for gamers
In order to avoid detection, the cybersecurity firm says that all malicious torrents are monitored and were issued different statuses such as "closed," "alive" and "detected by antivirus."
The tool is used to distribute ransomware including CryptXXX, CTB-Locker and Cerber, as well as financial Trojan Dridex. In the past few months, InfoArmor has identified over 1,600,000 records collected in the last few months from victims infected through the tool.
Earlier this week, researchers at IBM X-Force revealed a three-year-old banking Trojan, Quadars, is now targeting UK banks and financial targets around Europe.