Virlock ransomware can now use the cloud to spread, say researchers

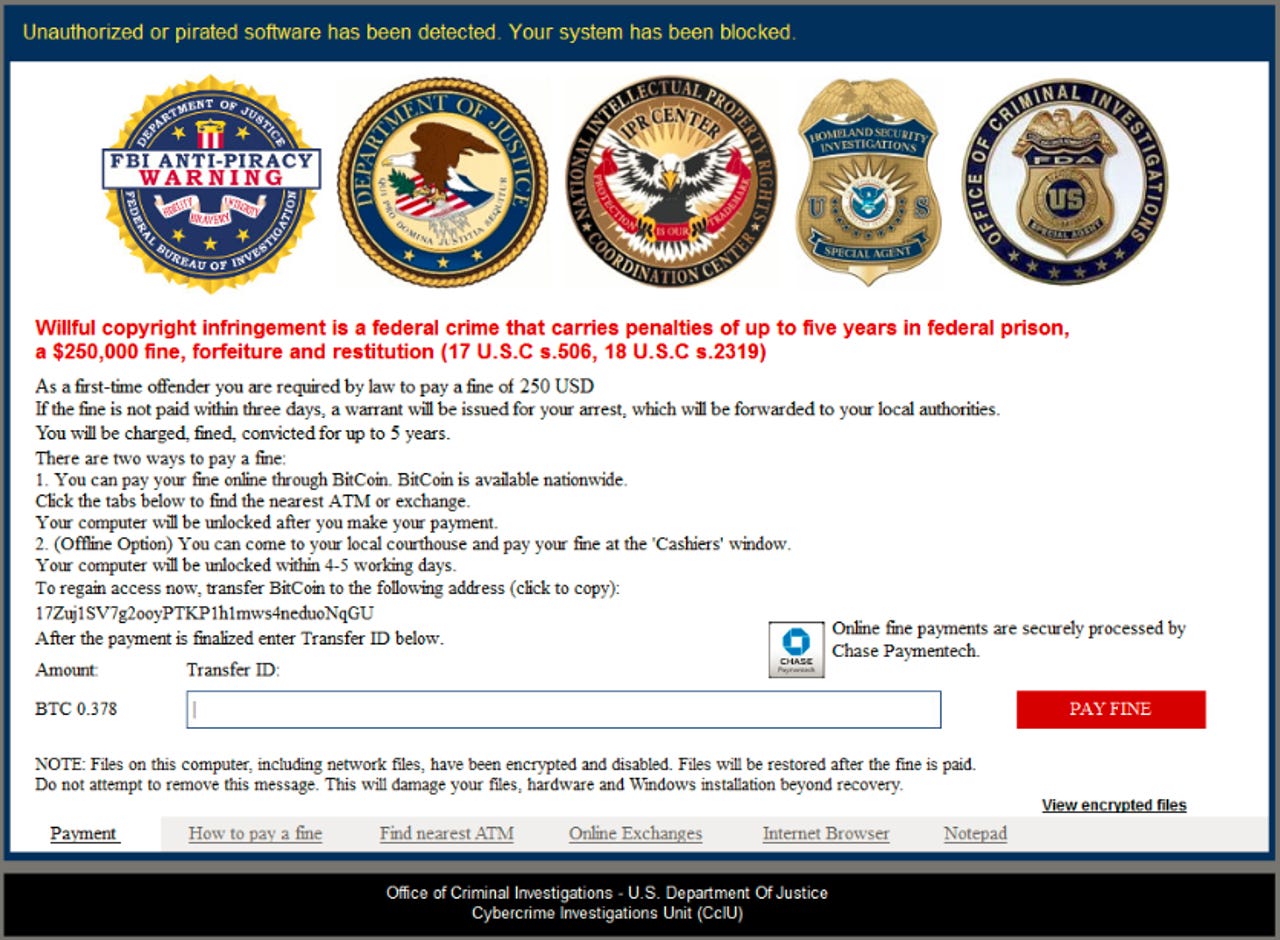
It's not the FBI demanding payment here, it's criminals.
A new variant of Virlock ransomware is capable of stealthily spreading itself through cloud storage and collaboration applications, potentially enabling one infected user to inadvertently spread the file-locking malware across their enterprise network.
Security
The Virlock variant is yet another instance of cybercriminals deploying new techniques in order to make ransomware even more effective: it's expected to cost organisations a total of $1bn during 2016 alone.
Virlock has been active for almost two years now, and security researchers at Netskope have discovered how Virlock can employ a 'fan-out' effect, spreading itself through the use of cloud sync, cloud storage, and collaboration applications.
Researchers cite an example of two users, User A and User B, collaborating on a folder called 'Important'. Both users have some of the files within the folder synced on their respective machines.
However, User A gets infected with Virlock ransomware, encrypting all their files, and also turning them into new Virlock infector files -- including the files which are synced with the cloud collaboration application. Therefore, as a result of the synced files on User A's machine being infected, Virlock also spreads to the cloud folder, and infects the files stored there.
That means if User B clicks on any of the files in their shared folder, the Virlock-infected file is executed, and the rest of the files on their machine become encrypted with ransomware -- becoming Virlock file infectors in the process.
Much like other forms of ransomware, Virlock asks the victim for a payment in Bitcoin in order to unencrypt their machine. However, unlike other forms of ransomware such as Cerber or Locky, Virlock doesn't explicitly state that the user has become the victim of cybercriminals.
Instead, it claims to be an anti-piracy warning from the FBI, stating that pirated software has been found on the user's system and threatening them with prison and a $250,000 fine unless they pay a $250 'first-time offender' fine.
It's a technique which has long been deployed by cybercriminals in an effort to spook victims into paying up. However, recently hackers haven't even pretended to be anything but extortionists, with some instances of ransomware threatening to delete files for good if a ransom isn't paid within a certain amount of time.
In order to avoid infection with Virlock, Netskope researchers recommend that critical data should regularly be backed up in a cloud account which is regularly scanned for malware. Users should also be wary of opening untrusted email attachments, especially from unknown senders -- although it seems that many aren't even heeding this basic advice, with recent research finding that malware is hitting enterprise networks every four seconds.