Securing the web once and for all: The Let's Encrypt Project

In case you've been in a cave, you may not have noticed Web security is a mess. Gmail had fits this weekend with sending mail because the mail server tasked with sending messages had an expired security certificate. Before that, a Secure-Socket Layer (SSL) encryption problem that had been hiding in the code since the 1990s opened the door to the FREAK security hole. It's clear the industry needs to get its act together when it comes to web site encryption. The Internet Security Research Group (ISRG) with its Let's Encrypt project wants to give us that fix.
We've known since 2010 when Firesheep demonstrated your login could be stolen over Wi-Fi that the only way to have reliable security is for every website to be encrypted. One reason why this hasn't happened is that Transport Layer Security (TLS) certificates are both expensive and cumbersome to administer.
So, late last year the EFF and Mozilla came with the idea of a free one-click TLS CA. Today, it's getting closer to reality.
Security
"Encryption should be the default for the web," said Josh Aas, the ISRG's executive director and senior technology strategist at Mozilla in a statement. "The web is a complicated place these days; it's difficult for consumers to be in control of their data. The only reliable strategy for making sure that everyone's private data and information is protected while in transit over the web is to encrypt everything. Let's Encrypt simplifies this."
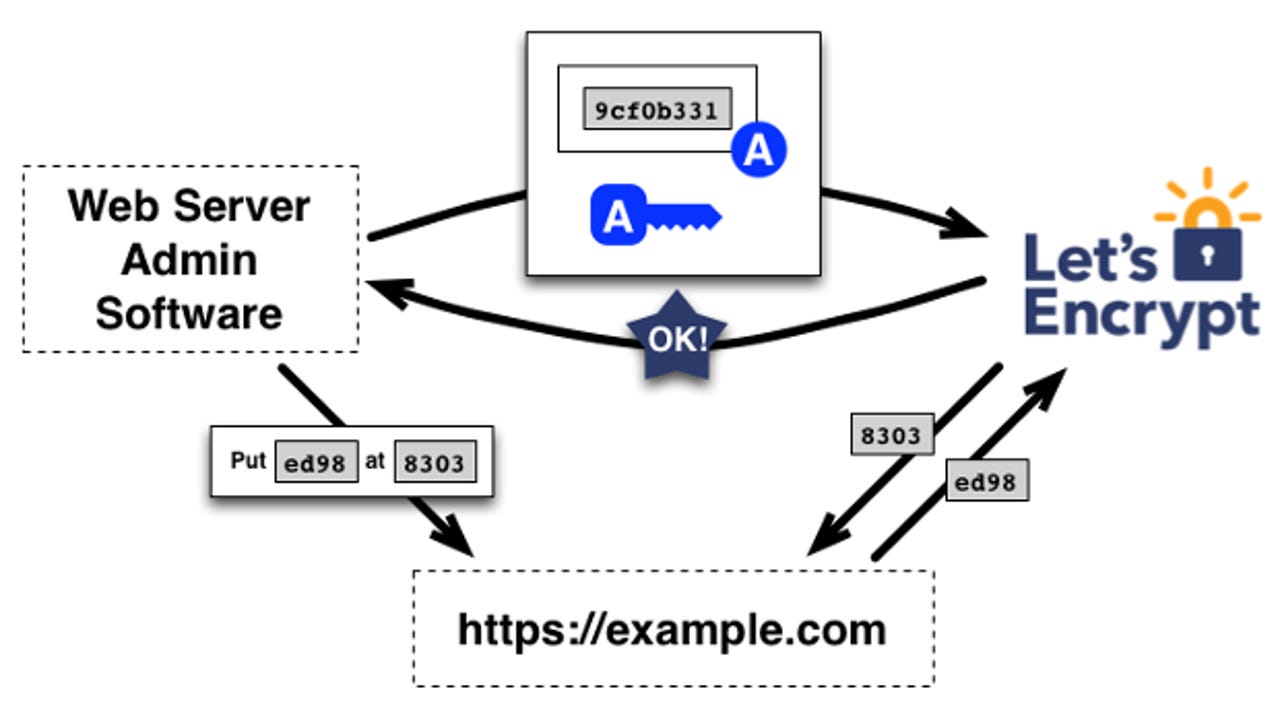
Once in place in mid-2015, Let's Encrypt will make enabling HTTPS for your site as easy as installing software on the server. In Linux, for example, it would look like this
$ sudo apt-get install lets-encrypt $ lets-encrypt example.com
And, that would be all there is to it. The now secure site, https://example.com, would be live immediately.
The Let's Encrypt management software uses Automated Certificate Management Environment (ACME) to enable you to do the following:
- Automatically prove to the Let's Encrypt Certificate Authority (CA) that you control the website
- Obtain a browser-trusted certificate and set it up on your web server
- Keep track of when your certificate is going to expire, and automatically renew it
- Help you revoke the certificate if that ever becomes necessary.
Less technically, the key principles behind Let's Encrypt are:
- Free: Anyone who owns a domain name can use Let's Encrypt to obtain a trusted certificate at zero cost.
- Automatic: Software running on a web server can interact with Let's Encrypt to painlessly obtain a certificate, securely configure it for use, and automatically take care of renewal.
- Secure: Let's Encrypt will serve as a platform for advancing TLS security best practices, both on the CA side and by helping site operators properly secure their servers.
- Transparent: All certificates issued or revoked will be publicly recorded and available for anyone to inspect.
- Open: The automatic issuance and renewal protocol will be published as an open standard that others can adopt.
- Cooperative: Much like the underlying Internet protocols themselves, Let's Encrypt is a joint effort to benefit the community, beyond the control of any one organization.
That may sound great to most of you. I like it. But I suspect one group isn't going to care for this at all: The commercial CAs such as Comodo, Symantec, and GoDaddy.
It's likely they will argue that the kind of SSL/TLS certificates that Let's Encrypt will provide won't be good enough. There are three levels of SSL certificates: Domain Validated (DV), Organization Validated (OV) and Extended Validation (EV). Let's Encrypt will provide only DV certifications.
For an OV cert, the CA must check with third parties to ensure that the name of the applying organization is the same as the domain's owner. For an EV cert, you need to prove that your business, agency, or organization really is who it says it is. It's only with EV certification that web browser's address bars turn green to show that the site is both secure and that it belongs to its claimed owner.
For the CA businesses this means their high-end services are unlikely to be damaged by ISRG's efforts. For companies that rely upon cheap, $4.95 a year SSL certificates, it will be a different story.
Related Stories: