Inside the botnets that never make the news
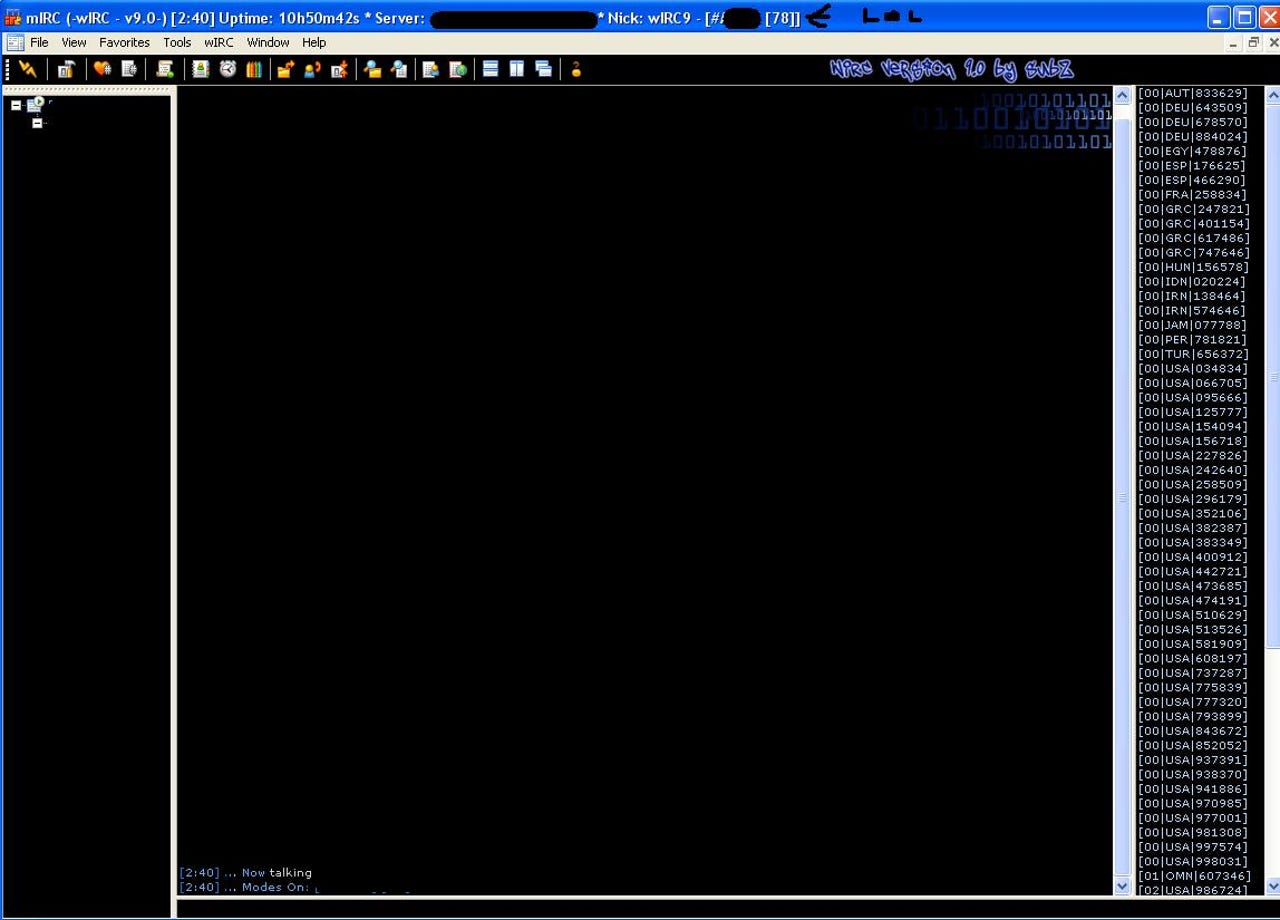
This screenshot is a great example of the social networking activities taking place inside the cybercrime ecosystem. The modest botnet consisting of 78 infected hosts has a LOL (abbreviation for laughing out loud) sign added by a competing botnet master aiming to expose a scammer pretending to have a much bigger botnet.
In this screenshot, the botnet master is advertising the obfuscated command and control interface of his commercial malware. In the deobfuscated screnshot, he's demonstrating the dropping of a presumably undetectable piece of malware which botnet masters update on an hourly/daily basis.
This targeted botnet consists of 19,528 infected hosts, the result of a spreading malware campaign across the MSN instant messaging network. The botnet has naturally blurred the exact message of the campaign, but the screenshot demonstrates the disturbing clickability of the campaign.
In this 63 infected hosts botnet, the botnet master is playing around with it by launching another MSN malware spreading campaign, and injecting the malware process within legitimate applications.
These three botnets (5,225, 3,771 and 929 infected hosts) are a good example of how the botnet master diversifying the infection vectors by launching multiple campaigns, thereby building multiple botnets. What he's forgetting is the fact that not only is he using IRC as command and control, but all the botnets are on the same server.
Yet another targeted botnet campaign in progress that has already managed to infect 621 hosts.
The botnet master in this 1017 infected hosts botnet is so paranoid he's blurred the entire screenshot
Botnet master t0nix has also extensively blurred any clues that may lead to exposing his 2,373 infected hosts botnet. What he's not taking into consideration is that among the infected hosts are several ones exclusively used for monitoring purposes.
28, 118 infected hosts are controlled by cybix through the use of multiple -- some outdated -- infection vectors.
Yet another botnet campaign in progress.
An inside view of the botnet masters desktop while he's advertising a modest 820 infected hosts botnet
Botnet master polx is actively infecting new hosts, 1182 so far.
What's worth pointing out about this particular botnet is how a single command allows the botnet master to increase the lifecycle of the campaign by injecting the malware in a multitude of local files.
Old netblocks scanning techniques aren't dead just yet, at least from the perspective of this targeted 1937 infected hosts botnet.
A relatively big botnet compared to the majority of the ones already discussed.
Another botnet campaign in progress with 1967 hosts so far.
74,901 infected hosts, with an interesting message of the day at the IRC server since the botnet master is claiming a violation of his privacy.
Botnet master ENO_2 has already managed to infect 1012 hosts, but forgot to blur the Albanian channel he's
This botnet is a an example of how insecure management of removable media in a combination with the use of AUTORUN, can easily result in a botnet like this one.
Channel #pwn is the home of a 126k+ botnet, behind the first screenshot are more botnets controlled by the same individual.
A second inside peek into the removable media/USB botnet.
Botnet master xdRl has already managed to infect 1323 hosts.
Botnet master Sonicx is currently operating a botnet consisting of 13,394 infected hosts and is using them as distributed scanning tools in order to expand the botnet.
Botnet master crim has already managed to infect 40,337 hosts from all over the world.
Botnet masters SL, Woopie and xd maintain a 24,144 infected hosts botnet.
If someone thought that Conficker is the only botnet exploiting ms0867 flaws, they'd be wrong. The copycats taking advantage of IRC command and control servers know how to exploit the window of opportunity here.