Photos: How does spyware get on your PC?

And what can it do?
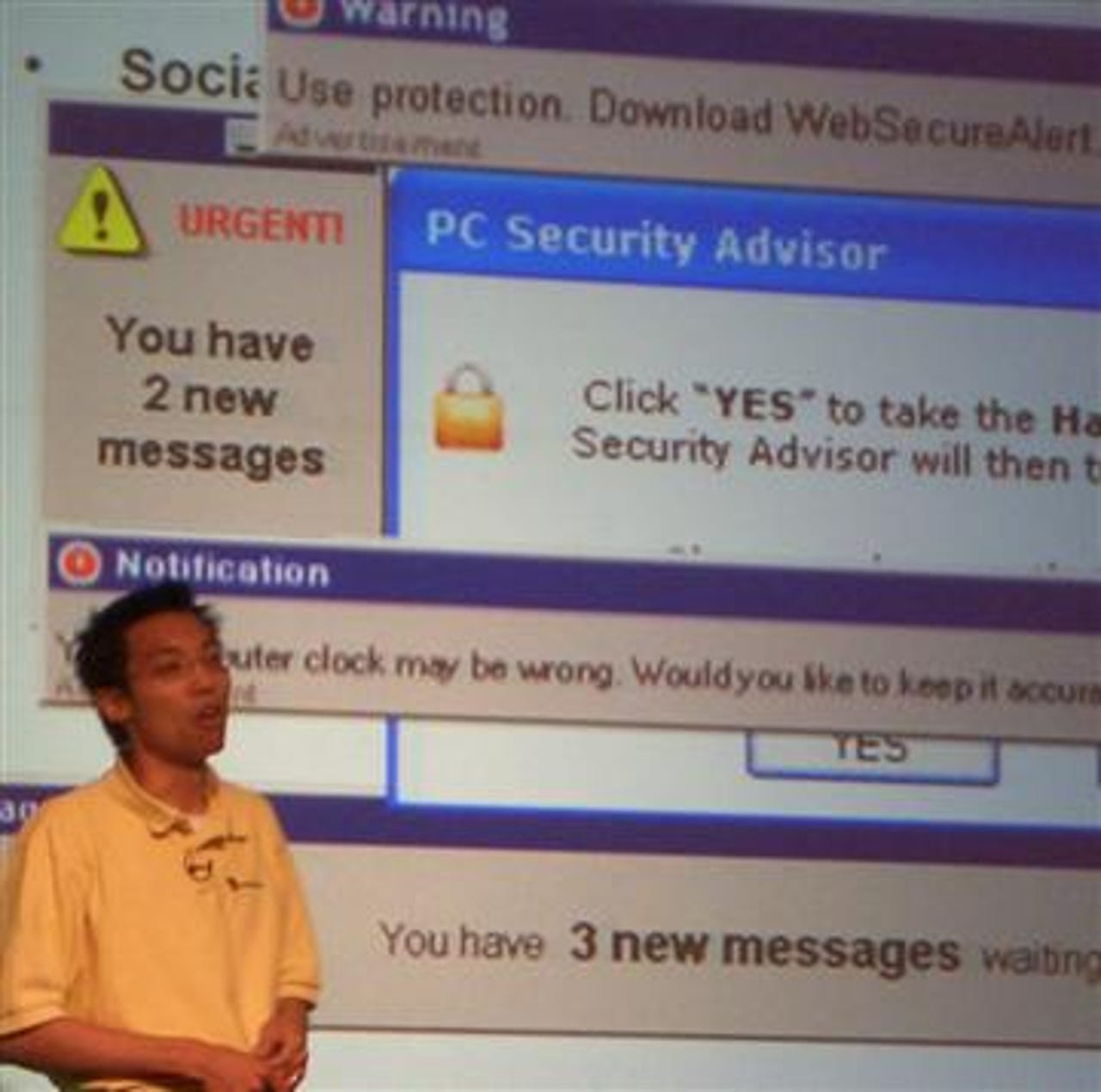
Speaking at the Virus Bulletin 2005 conference in Dublin, Eric Chien, senior antivirus researcher at Symantec, outlines the common ways users are picking up spyware. Pop-up windows which suggest security updates and clock settings are available, or new messages are unread, often tempt less security-minded users to click."We've actually seen people create a full screen pop-up of a fake 'blue screen'," said Chien. Users are forced to act out of the belief their machine has crashed.
Chien said there are currently around 11,000 families of spyware applications and those intent on getting the malicious software onto users' machines are coming up with almost as many ways of doing so.
All photos: Will Sturgeon
The use of an install window that users will have seen when installing applications they do want may also create an impression of legitimacy.
Often such windows will be persistent, said Chien, popping up repeatedly and preventing the user from navigating away. They will keep popping up until the user caves in or shuts down their browser via their task bar (ctrl + alt + del).
Media downloads can also be a source of spyware. Chien said he illegally downloaded episodes of Family Guy over BitTorrent "purely for research purposes" and found the files he received contained spyware application 180 Search Assistant, now called Zango.
GAIN features heavily in many tales of spyware woe, due to its association with the widely used Kazaa application.
Despite claiming it is an entirely legitimate organisation, GAIN and the associated Gator name are familiar thorns in the side of many anti-spyware advocates.
Chien said not only does the GAIN Eula state it will relay information back from the user's PC, it also states - in hope perhaps more than expectation - that users cannot remove the spyware from their PC or even encourage others to do. Other Eula's Chien has seen even include references to the fact the application may access and exploit user data held in Outlook address books and other critical applications.
Many spyware applications are programmed so as to be close to impossible to remove once installed, warned Chien.