Screenshots: Sites harbor Windows Trojan

Hiding places for Windows Trojan
A flaw in some versions of Microsoft Windows Meta File is spawning attacks ranging from worms to spam, security experts have warned. The Windows Meta File flaw uses images to execute arbitrary code, according to a security advisory issued by the Internet Storm Center.
Websense Security Labs has posted some examples of sites that appear to have been compromised. This is a Dutch example.
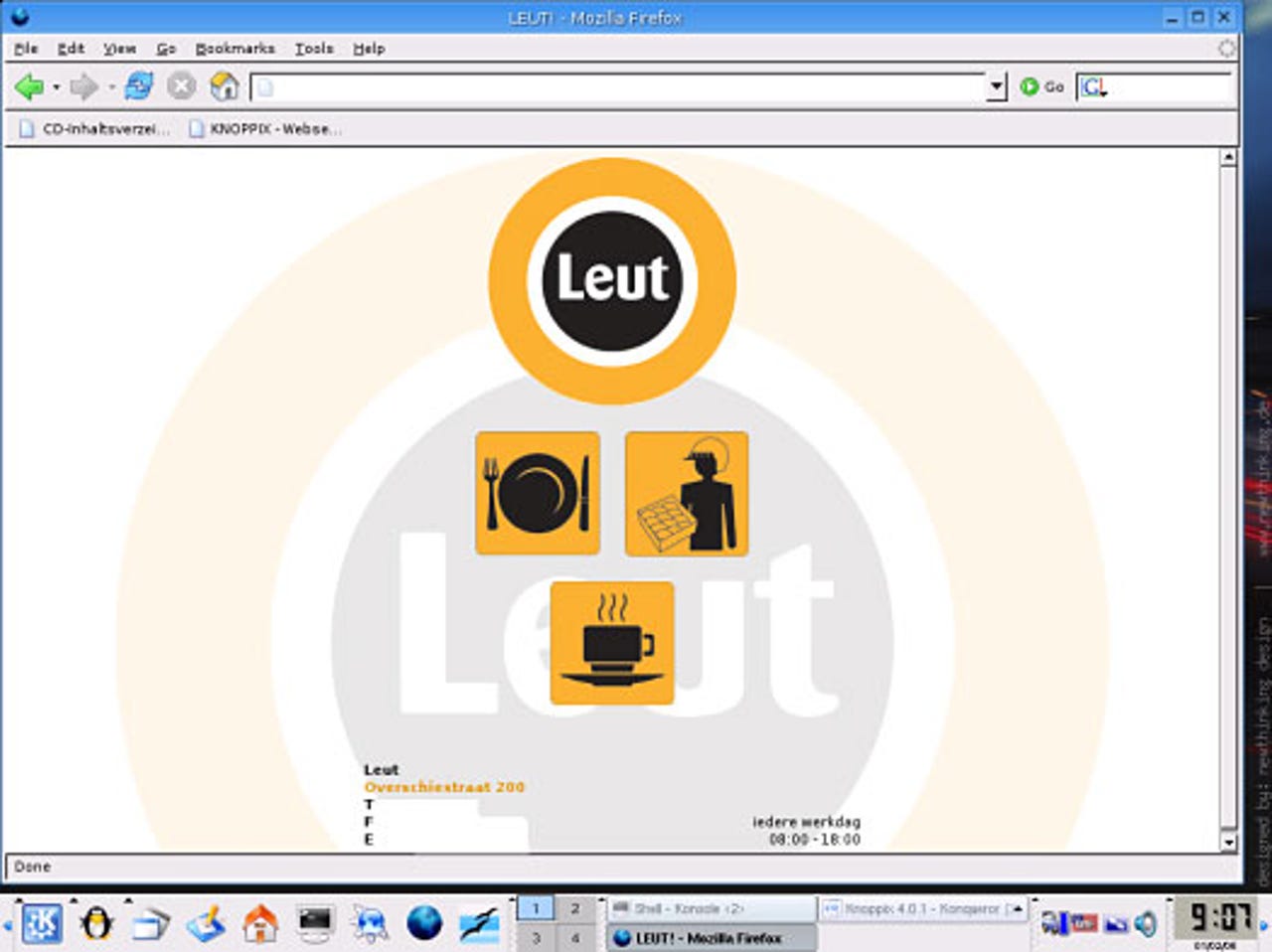
Renovation site hosts Trojan
A vulnerable Windows system could become infected if someone just views what appears to be a malicious image on this compromised Web site, according to Websense's posting.
Sites compromised worldwide
Websense, which has been tracking malicious activity around the flaw, says it has discovered malicious sites in the United States, Russia, Netherlands, the United Kingdom, China and Japan.
Compromised Cosmo site
Another example. Mikko Hypponen, chief research officer at F-Secure, estimates that 99 percent of computers worldwide are vulnerable to an attack using the WMF flaw.
Street IT site could pose a risk
Microsoft has said it plans to release a fix for the WMF vulnerability as part of its monthly security update cycle on Jan. 10.
Knoppix behavior
This is how a machine running Knoppix, a version of Unix, behaves when a malicious Web site is visited using the open-source Firefox browser. It alerts the Web surfer that a file is being opened.