Ten tips to avoid identity theft

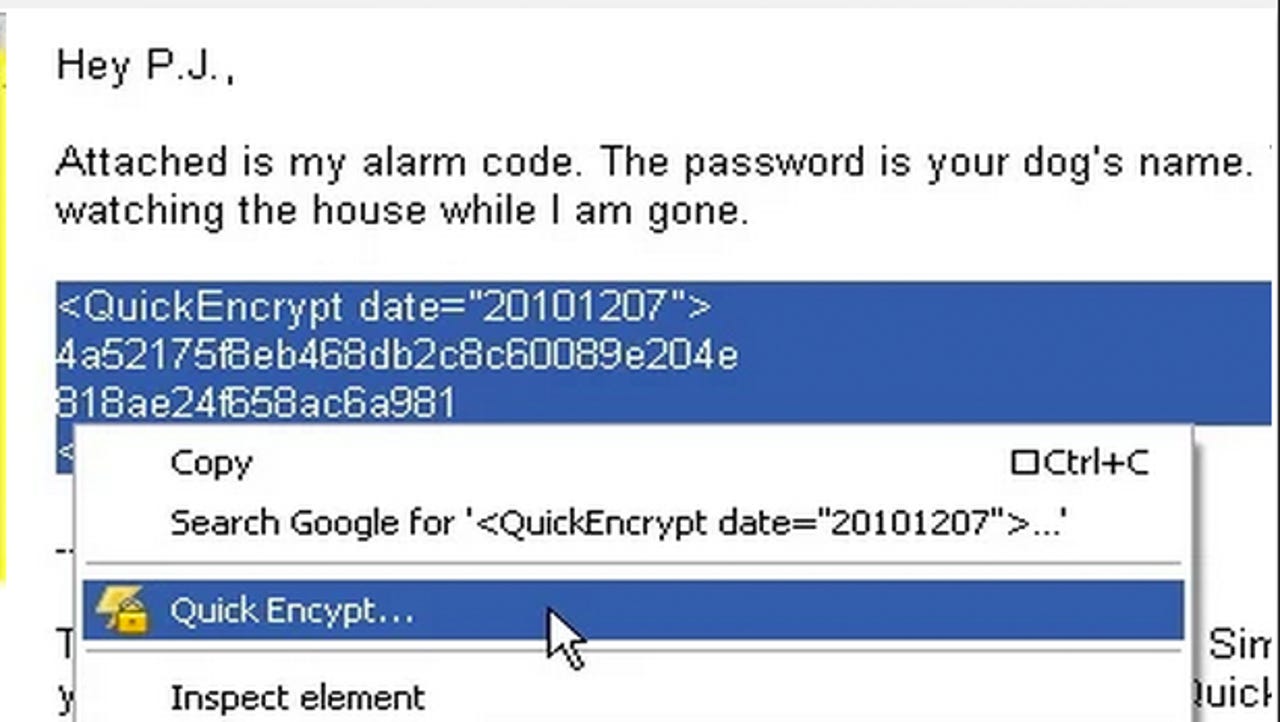
Encrypt, encrypt, encrypt
Virtual private networks (VPNs), IP hiders and HTTPS connections all contribute in making your online activities harder to track and less open to the world. While no solution is 100 percent foolproof, using extensions such as Quick Encrypt and Cryptocat, as well as VPNs such as Torguard, PIA and Hotspot Shield can help you protect yourself.
Secret email addresses
For the sake of convenience, we often link all of our online accounts to a singular, main email address. This address, when used to sign up for everything from Internet banking to Facebook and Gmail, if compromised, gives an identity thief unrestricted access to your full online identity. Instead, consider using a private email address for the most crucial services you use, such as e-commerce and Internet banking. You may also consider using separate, unlinked email addresses for your social media accounts.
Keep your birthday private
When you sign up for online accounts, they can pave the way for identity left in the physical world. If this information is stolen or the hosting service suffers a security breach, information such as your birthday might be used to set up accounts in your name. Instead of inputing your true birthday when signing up for new accounts, consider using a false birthday to keep your information secure and off the web as much as possible.
Throwaway email addresses
While disposable email addresses might not seem linked to combating identity theft, if you sign up for services, your email address may end up in the hands of third-parties -- not only clogging your email up with spam but potentially placing you at risk of phishing campaigns and fraudulent messages. To eradicate this, consider using a disposable email address when signing up for new accounts -- one that you can check once a week or so but will not impact on your everyday account.
Secure your passwords
It is said time and time again, but if you use password which are easily cracked or guessable -- such as "QWERTY," "123456," or "password1," then while you may remember them, you are handing the keys over to your digital kingdom without a fight. Up the complexity of your passwords, or consider using password management software such as Lastpass, keeping the list of passwords you need to remember to a minimum.
Security questions: The truth or not the truth?
Security questions, used to verify your identity if you are locked out of an account, forget your password or need to talk to an advisor on the phone, prompt us to reveal a piece of personal information -- such as your pet's name or mother's surname. While this data is used to verify your identity, there is no need to be truthful. Someone who wishes to make you the victim of identity theft may be able to find out the answer through public records or social media tracking, and so it is a better idea to submit a false answer -- one you can remember -- to verify your accounts.
Be wary of suspicious emails
Phishing campaigns, designed to dupe victims into revealing personal information such as bank details and sensitive information which can be used in identity theft, increase in complexity every year. We are far beyond the days of emails telling you you've won the Spanish lottery or have a long-lost relative in the depths of Africa; instead, spam and fraudulent campaigns now often mimic legitimate businesses and contain links to websites which appear genuine -- before enticing you to input your account details. Victims of these campaigns may find their financial accounts or payment systems used fraudulently. To protect yourself, watch out for suspicious links and don't panic -- if, for example, you receive an "email" from your bank, call them.
Don't take risks with shortened links
While shortened links come in handy across social media and in arenas like Twitter where message lengths are restricted, they also do not immediately show their origins. To save yourself from being hoodwinked by legitimate-looking websites asking for your account details, always check the browser address bar for legitimacy when clicking upon a short link, and never input any account details if you do not trust the source of the link. It is also worth noting that if a trusted source's account is compromised, they may be unintentionally spreading malicious links -- so if a message looks suspicious, ignore it.
Incognito browsing
Cookies are small packets of data located in browser directories which may record your browsing sessions and allow websites to track your movements. If you choose to use Incognito mode -- such as in Chrome by selecting a "New Incognito window" -- you can stop your browser from saving the details of your browsing and what you are downloading, as well as preventing cookies from being stored on your computer.
The Internet remembers
Finally, you need to remember that the Internet doesn't forget. A careless post on social media revealing your mobile number, home via GPS-based location and checking in or your full birthday may be discovered, copied or saved by someone using social engineering in an attempt to take over accounts or your identity. Be careful about what you share.