YubiKey by Yubico
YubiKey offers a quick, cost-effective and simple way to protect your data, both online and offline, whether for personal use, business, enterprise, or even developers.

1 of 8 Adrian Kingsley-Hughes/ZDNET
YubiKey 4
2 of 8 Adrian Kingsley-Hughes/ZDNET
YubiKey 4
3 of 8 Adrian Kingsley-Hughes/ZDNET
Minimalist packaging.
4 of 8 Adrian Kingsley-Hughes/ZDNET
YubiKey 4 and YubiKey FIDO U2F
5 of 8 Adrian Kingsley-Hughes/ZDNET
YubiKey 4 connected to MacBook
6 of 8 Adrian Kingsley-Hughes/ZDNET
YubiKey range
7 of 8 Adrian Kingsley-Hughes/ZDNET
Authenticating with Facebook
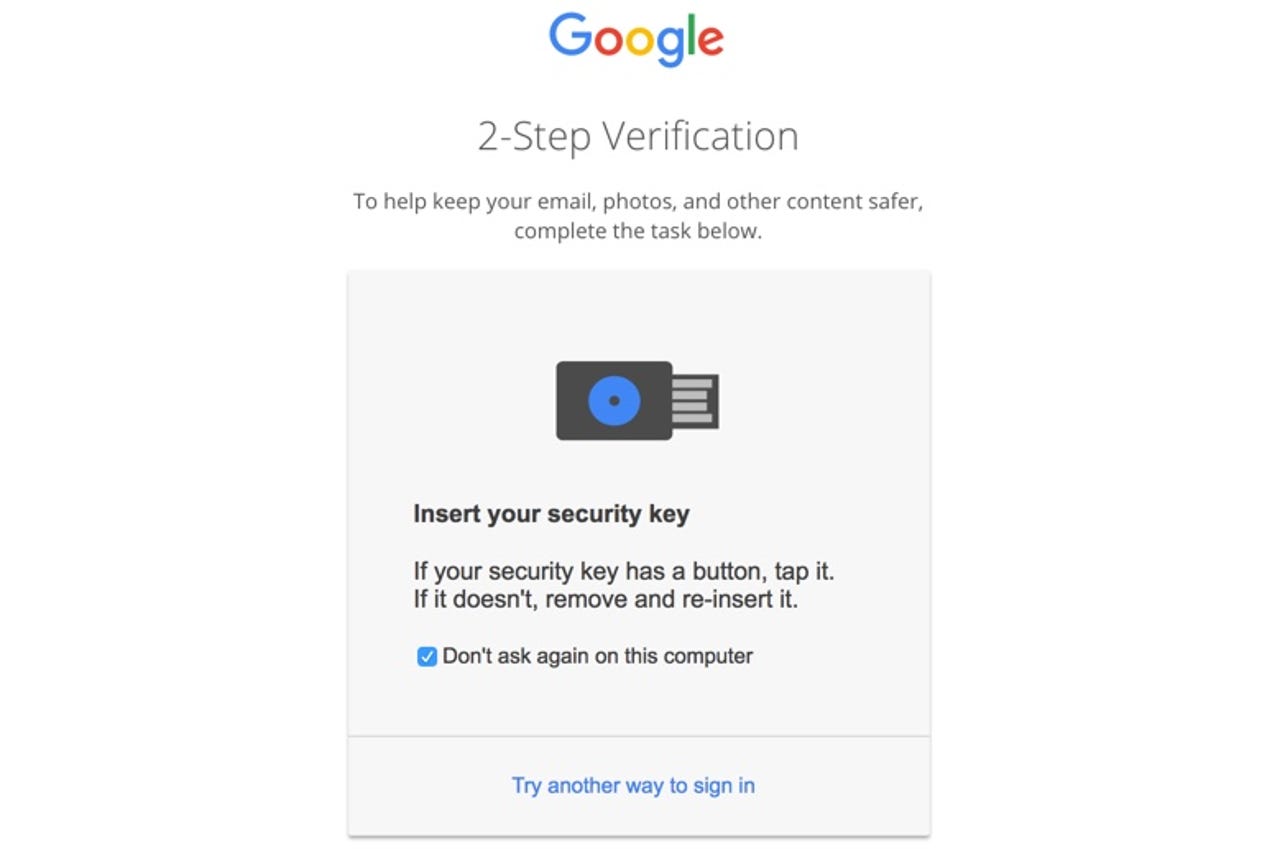
8 of 8 Adrian Kingsley-Hughes/ZDNET
Authenticating with Google
Related Galleries
Holiday wallpaper for your phone: Christmas, Hanukkah, New Year's, and winter scenes
![Holiday lights in Central Park background]()
Related Galleries
Holiday wallpaper for your phone: Christmas, Hanukkah, New Year's, and winter scenes
21 Photos
Winter backgrounds for your next virtual meeting
![Wooden lodge in pine forest with heavy snow reflection on Lake O'hara at Yoho national park]()
Related Galleries
Winter backgrounds for your next virtual meeting
21 Photos
Holiday backgrounds for Zoom: Christmas cheer, New Year's Eve, Hanukkah and winter scenes
![3D Rendering Christmas interior]()
Related Galleries
Holiday backgrounds for Zoom: Christmas cheer, New Year's Eve, Hanukkah and winter scenes
21 Photos
Hyundai Ioniq 5 and Kia EV6: Electric vehicle extravaganza
![img-8825]()
Related Galleries
Hyundai Ioniq 5 and Kia EV6: Electric vehicle extravaganza
26 Photos
A weekend with Google's Chrome OS Flex
![img-9792-2]()
Related Galleries
A weekend with Google's Chrome OS Flex
22 Photos
Cybersecurity flaws, customer experiences, smartphone losses, and more: ZDNet's research roundup
![shutterstock-1024665187.jpg]()
Related Galleries
Cybersecurity flaws, customer experiences, smartphone losses, and more: ZDNet's research roundup
8 Photos
Inside a fake $20 '16TB external M.2 SSD'
![Full of promises!]()