Chinese cyberspies targeted Tibetans with a malicious Firefox add-on

Chinese state-sponsored hackers have gone after Tibetan organizations across the world using a malicious Firefox add-on that was configured to steal Gmail and Firefox browser data and then download malware on infected systems.
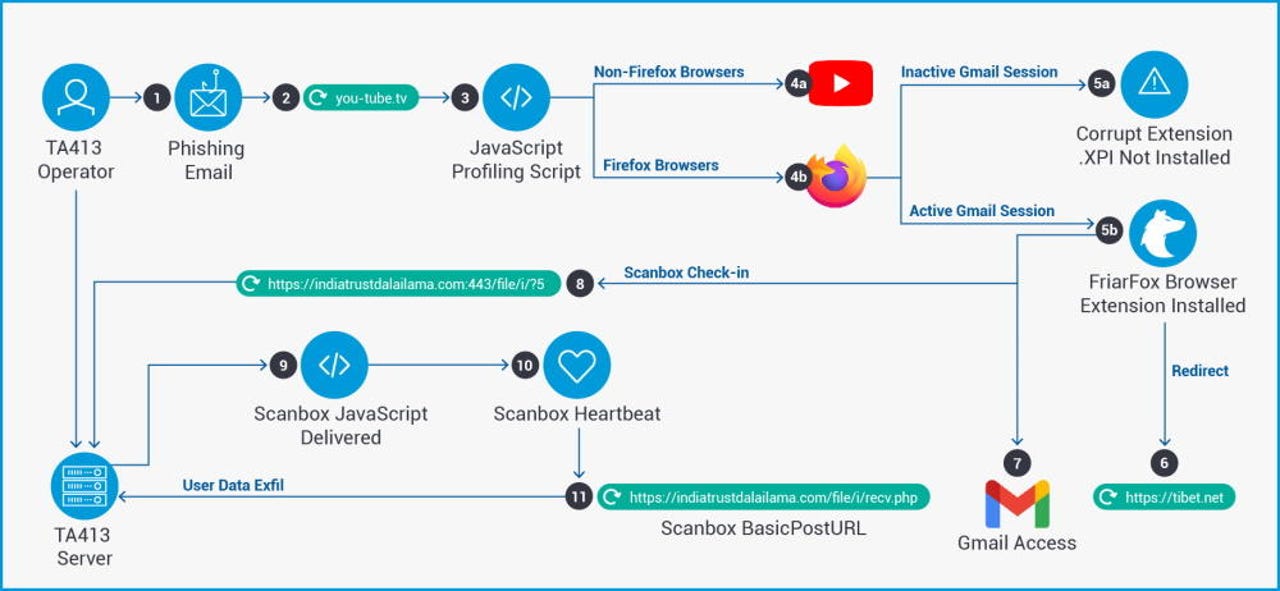
The attacks, discovered by cybersecurity firm Proofpoint this month, have been linked to a group the company tracks under the codename of TA413.
Only Firefox users were targeted
Proofpoint said the attackers targeted Tibetan organizations with spear-phishing emails that lured members on websites where they'd be prompted to install a Flash update to view the site's content.
These websites contained code that separated users. Only Firefox users with an active Gmail session were prompted to install the malicious add-on.
The Proofpoint team said that while the extension was named "Flash update components," it was actually a version of the legitimate "Gmail notifier (restartless)" add-on, with additional malicious code. Per the research team, this code could abuse the following functions on infected browsers:
Gmail:
- Search emails
- Archive emails
- Receive Gmail notifications
- Read emails
- Alter Firefox browser audio and visual alert features
- Label emails
- Marks emails as spam
- Delete messages
- Refresh inbox
- Forward emails
- Perform function searches
- Delete messages from Gmail trash
- Send mail from the compromised account
Firefox (based on granted browser permissions):
- Access user data for all websites
- Display notifications
- Read and modify privacy settings
- Access browser tabs
Firefox add-on also installed malware
But the attack didn't stop here. Proofpoint said the extension also downloaded and installed the ScanBox malware on infected systems.
A PHP and JavaScript-based reconnaissance framework, this malware is an old tool seen in previous attacks carried out by Chinese cyber-espionage groups.
"Scanbox has been used in numerous campaigns since 2014 to target the Tibetan Diaspora along with other ethnic minorities often targeted by groups aligned with the Chinese state interests," Proofpoint said in a report today.
The last recorded case of a ScanBox attack dates back to 2019 when Recorded Future reported attacks against visitors of Pakistani and Tibetan websites.
As for its capabilities, Proofpoint says ScanBox is "capable of tracking visitors to specific websites, performing keylogging, and collecting user data that can be leveraged in future intrusion attempts," making this a dangerous threat to have installed on your systems.
Flash EOL might have helped attackers
In this particular campaign, which Proofpoint codenamed FriarFox, attacks began in January 2021 and continued throughout February.
Although hackers have been using fake Flash update themes for years and most users know to stay away from websites offering Flash updates out of the blue, these attacks are believed to have worked much better than previous ones.
The reason is that Adobe retired Flash Player at the end of 2020, and all Flash content stopped playing inside browsers on January 12, 2021, when Proofpoint also saw the first TA413 FriarFox campaigns targeting Tibetan organizations.