Comcast customers targeted in sophisticated malvertising scheme

Comcast customers need to watch out for a new malvertising campaign specifically designed to install ransomware on their machines or hook them through fake tech support.
Cyberattacks have evolved beyond the days of Stuxnet. Now we are faced with phishing campaigns, thousands of malware variants in the wild, software vulnerabilities and exploits, hackers breaking to servers outside of our control and pillaging our data, and everything from the remote control of Jeeps to spying via baby monitors. The list of digital threats we face today is endless, and now, even trusted websites must always be viewed with suspicion.
Running a website and a server to support visitor traffic costs money. Online services which do not support themselves via paywalls -- an unpopular method as it is -- are forced to choose other alternatives, and despite many disliking advertising, adverts are a common way to do so.
Ads placed on a website are often sourced from third-party networks which offer bidding rounds for those who want exposure to pay the best prices possible for premium spots. Unfortunately, cyberattacks have cottoned on to how wide a visitor base they can access should they secure one of these spots, and at this point, malvertising was born.
Here's how it works: A cybercriminal bids for an advertising spot through a third-party ad network with a seemingly legitimate ad. Once they secure a spot, this ad then is tweaked with malicious code which could initiate drive-by download attacks -- in which a victim only has to visit a page to potentially become infected -- or the ad links to a malicious website, which may then download malware payloads onto a victim's machine or entice users to input their data.
The problem for ad networks and legitimate websites partnered with them is that malicious ads sometimes slip through the net, and thousands of trusting visitors can end up exposed before the threat is removed.
Online services ran by the Daily Mail and Daily Motion are recent examples of legitimate domains duped into serving malicious ads. Now, Comcast customers are facing the same threat.
On Monday, security researchers at Malwarebytes said a fresh malvertising campaign is targeting Comcast customers, starting the pursuit through a fraudulent ad placed on Comcast's Xfinity search page.
The ad in question is for a review site called SatTvPro.com -- via Google AdWords -- which appears on the cable provider's search page. When users click on the advert, the review site -- running an old version of the Joomla content management system -- opens, but also quietly loads redirects leading to the Nuclear exploit kit.
The exploit kit, first appearing in 2009, is set up with a variety of exploits for software including Adobe Flash, PDF and Internet Explorer. If a victim's PC is vulnerable to the kit and not fully patched, this could lead to remote code execution, surveillance and data theft.
Security
Malwarebytes says victims could also end up with the CryptoWall ransomware, or another variant, locking their systems due to the cyberattack. Ransomware, a particularly nasty piece of malware, locks systems and encrypts files in order to force victims to pay a fee to get their files back.
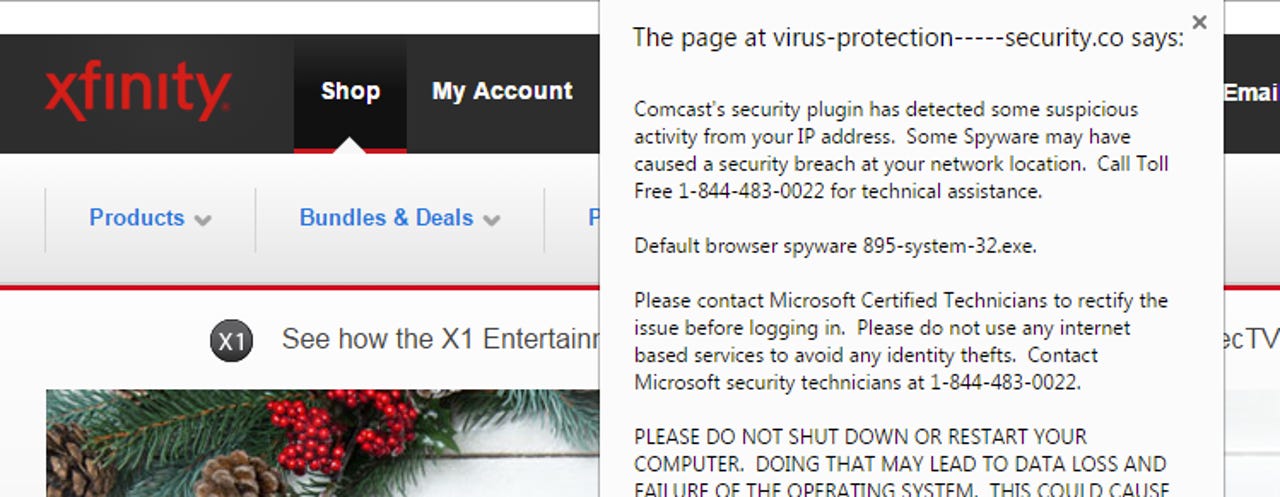
However, this isn't the end of the trail. Some Comcast customers would see an additional phishing website designed to look like the Xfinity portal, warning their system may have been breached -- before sending visitors to another domain complete with a tech support scam. The message reads:
"Comcast's security plugin has detected some suspicious activity from your IP address. Some Spyware may have caused a security breach at your network location. Call Toll Free 1-866-319-7176 for technical assistance."
The tech support scam acts as a secondary port to generate revenue from victims, should Nuclear fail. If visitors believe the "Comcast" warning to be legitimate, they end up calling the number, in which scammers could persuade victims to hand over their account details.
The security team says the two malicious websites were linked together through tracking software, commenting:
"There are still several plausible scenarios for who really was behind this attack.
Based on the evidence we collected, the tech support scam page was definitely tailored for Comcast users, and not simply the pop-up alert but also the full-screen iframe loading the Xfinity portal."
Malwarebytes immediately contacted Google and Comcast about this attack, and the SatTvPro domain is now flagged by Google's Safebrowsing scheme.
2015 Holiday guide: Gifts and gadgets for under $100
Read on: Top picks